Thesis
Business Email Compromise (BEC) is one of the costliest forms of vendor attacks. It occurs when an attacker hacks into a corporate email account and impersonates the real owner to defraud the company, its customers, partners, and/or employees into sending money or sensitive data to the attacker’s account. As of 2020, BEC was the single greatest cause of cybersecurity-related financial loss. In 2019, the FBI Internet Crime Complaint Center (IC3) recorded 23.8K complaints about BEC, which resulted in more than $1.7 billion in losses.
In total, the email security market was valued at $3.9 billion in 2022. The market is growing at an 11.1% CAGR, with growth being driven by an increase in phishing activity; malicious phishing emails were found to have increased by 569% in 2022. Within email security, the BEC market alone was valued at $1.2 billion in 2022 and was growing even faster than email security as a whole at a CAGR of 20.5%. Growth in the space is being driven by not only the rise in attacks but also by increasingly sophisticated AI capabilities that allow for better BEC solutions.
Abnormal Security is designed to help businesses shield themselves from modern email threats like phishing, malware, and account takeovers. The company implements a cloud-native, API-based architecture and utilizes AI-based behavioral anomaly detection to detect attacks that might otherwise slip past traditional filters. Abnormal’s core product is inbound email security, and it also provides email account takeover protection, email security posture management, and other email productivity and security tools.
Founding Story
Abnormal Security was founded by Evan Reiser (CEO) and Sanjay Jeyakumar (CTO) in 2018.
Reiser, a serial founder, founded several other startups before Abnormal. His first company, an online-to-offline advertising platform called Bloomspot that used behavioral profiling to direct offline purchasing through online ads, sold to JP Morgan in 2010. After that, he founded a company called AdStack that applied machine learning to advertising technology which was acquired by TellApart in 2013, which was itself acquired by Twitter in 2015.
While working at Twitter, Reiser found that he “missed the pace of startups”, along with startup culture. He therefore decided to start a company again, this time in the enterprise technology space. He was joined by Jeyakumar, who was a founding engineer at TellApart and who Reiser said “shared his vision.”
By chance, Reiser and Jeyakumar met with a partner at Greylock, Asheem Chandna, a successful enterprise technology investor. In talking to him, they learned about enterprise challenges that came as a consequence of the shift to new cloud architectures. The pair then conducted over 50 meetings with Fortune 500 CIOs and CISOs to uncover large enterprise IT pain points.
Through their conversations, they noticed a pattern of enterprises feeling a need to prevent financial loss due to socially engineered email attacks. At the time, cloud email providers were not doing much to help with the issue, and Reiser and Jeyakumar believed they could apply similar machine learning technology that they saw used at TellApart and Twitter to quickly identify and prevent targeted email attacks. This led to the birth of Abnormal Security.
Product
Core Product
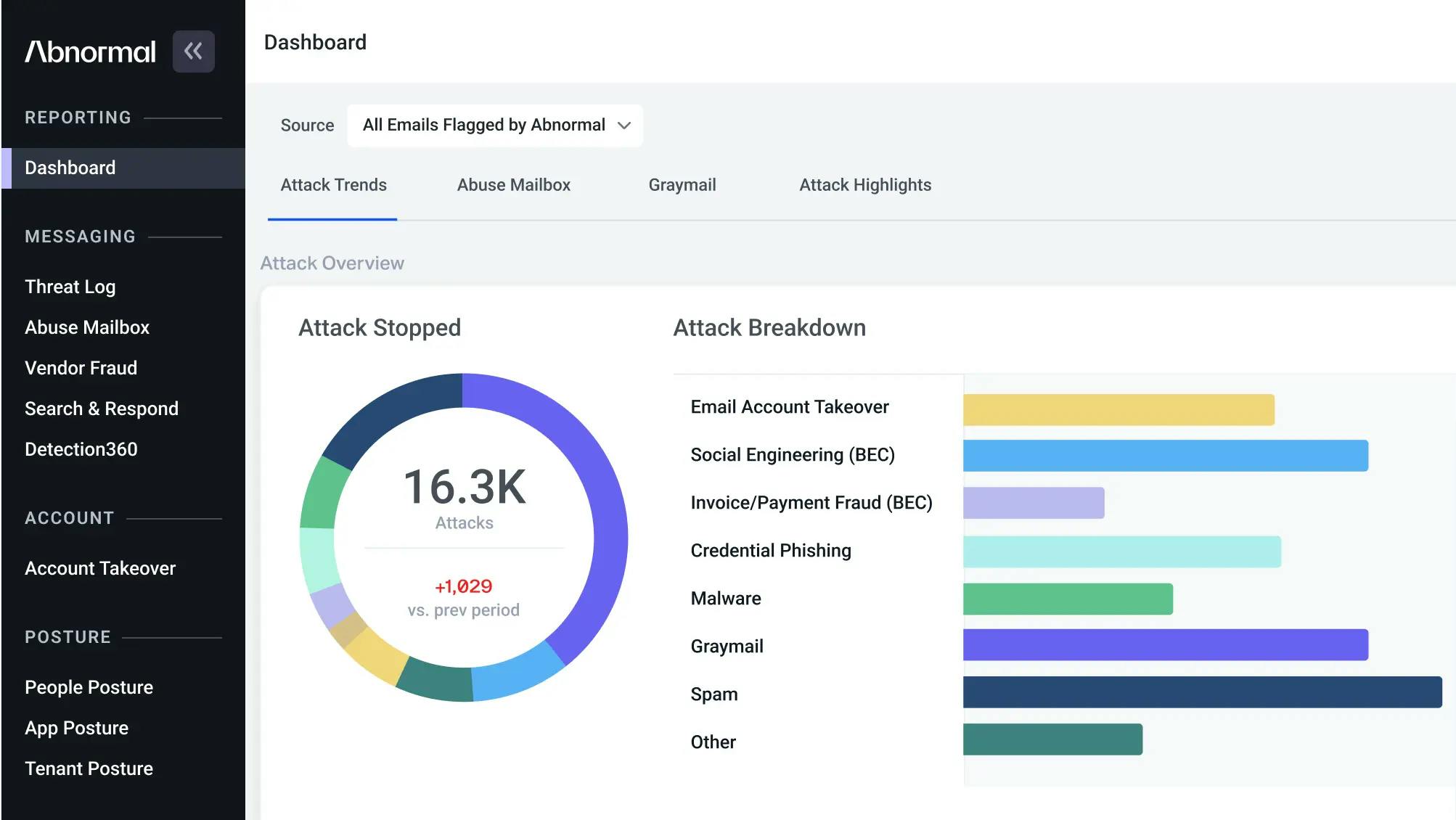
Source: Abnormal Security
Abnormal Security’s core product is inbound email security. According to Abnormal Security, the average business email compromise costs organizations $125K. 89% of companies see a supply chain compromise attack every week, and it takes an average of 308 days to identify and contain breaches.
The company uses behavioral AI to help stop a spectrum of targeted attacks. It claims it can detect “never before seen” attacks with its ability to detect anomalous behavior; as the company puts it, it can do this with “no traditional indicators of compromise by analyzing tens of thousands of unique signals to detect anomalies in email messages.”
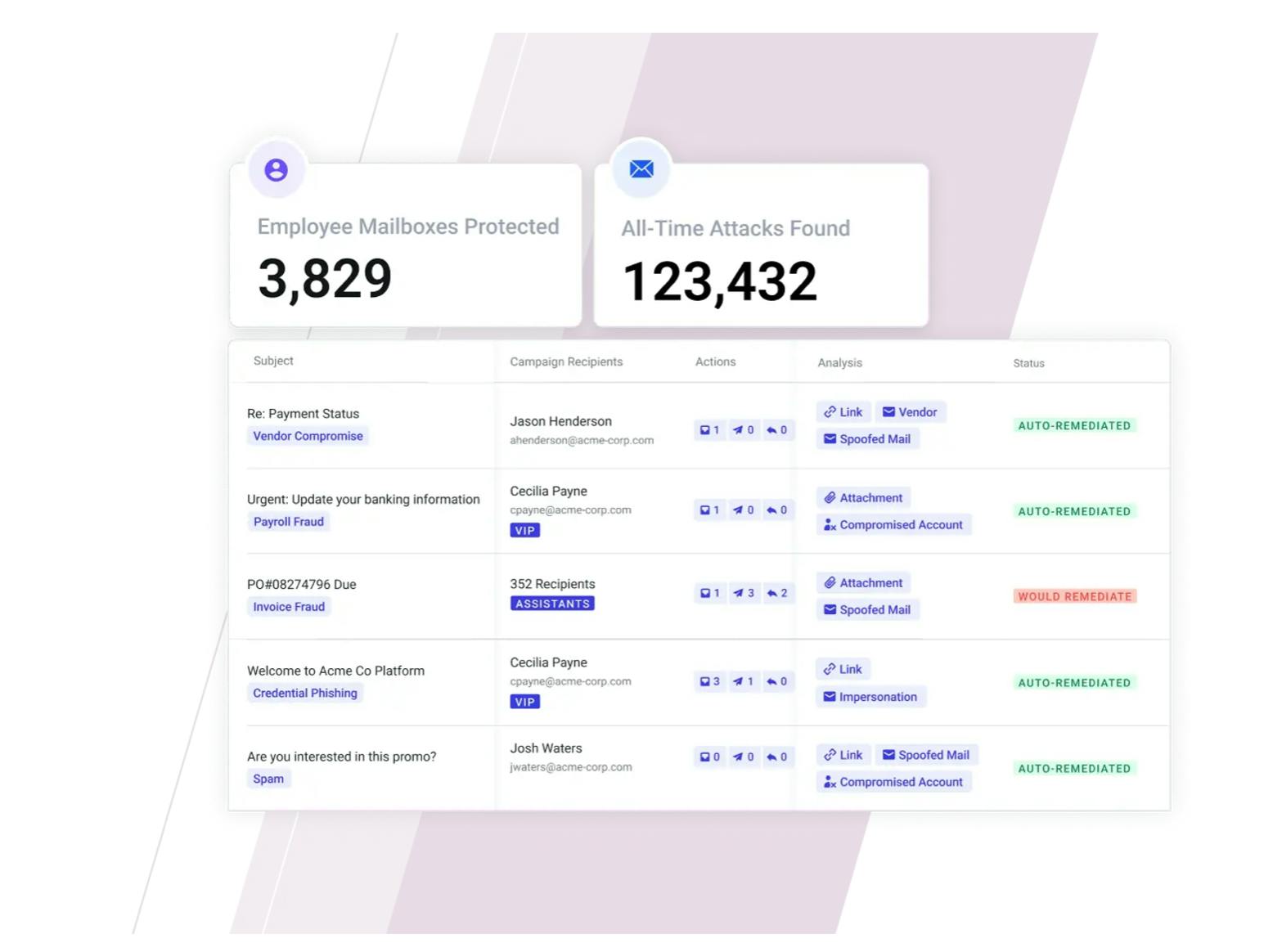
Source: Abnormal Security
Abnormal Security also automatically remediates messages it identifies as malicious to “remove the possibility of end-user engagement”, while also providing records of email messages it categorizes in a searchable “Threat Log”. This feature is intended to help administrators get an overview of threats and trends.
The Abnormal Platform
The Abnormal platform integrates with cloud email platforms, cloud collaboration apps, Okta, and Crowdstrike via API, allowing it to take in thousands of signals that could point to suspicious behavior across tenants.
As Brian Markham, a customer at EAB, noted:
“The proof of value with Abnormal was easy. After a quick API integration, we let it collect data for two weeks. I showed our CFO the results, and Abnormal instantly made sense to them.”
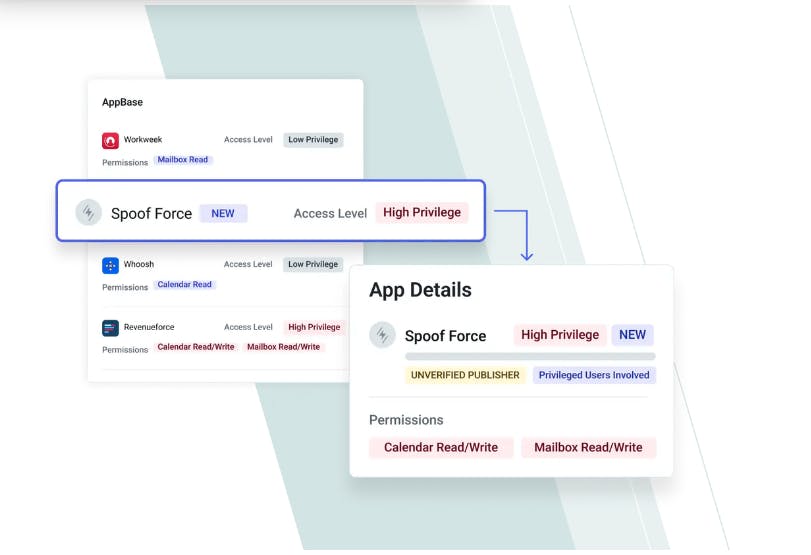
Abnormal’s Knowledge Bases — including PeopleBase, VendorBase, AppBase, and TenantBase —provide visibility into entry points across the cloud email platform, revealing high-impact events.
Source: Abnormal Security
The platform also supports security teams in their investigation and remediation tasks by tracking insights on their Threat Log; analysts can search and respond to specific messages or campaigns.
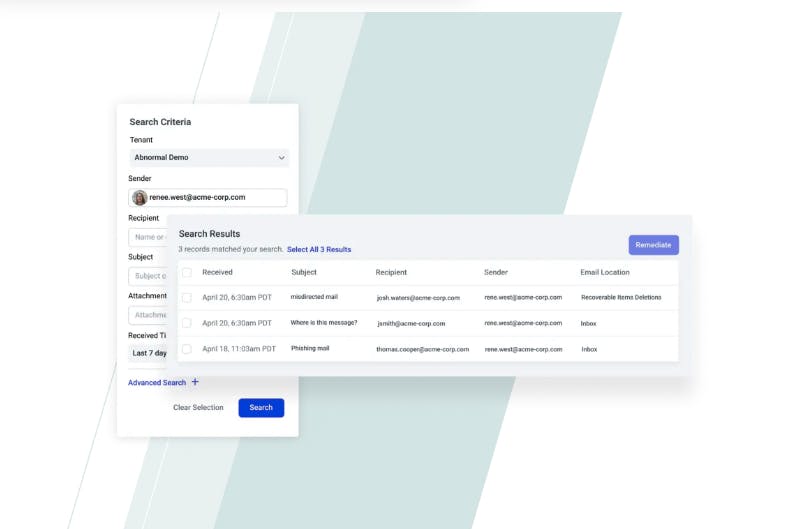
Source: Abnormal Security
Abnormal can integrate into popular security operations solutions with API-based integrations that allow security teams to use Abnormal’s threat detection within existing workflows.
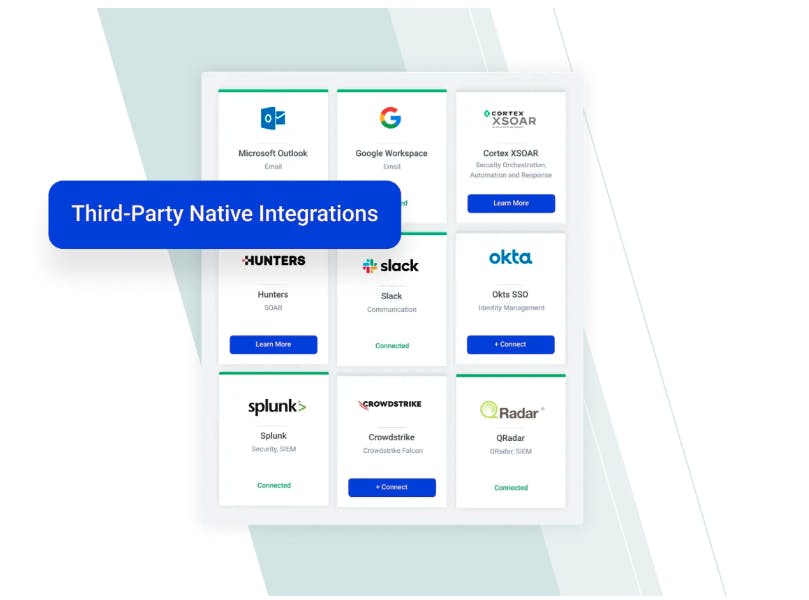
Source: Abnormal Security
Platform Features
API Integration: Abnormal’s platform features give users access to thousands of contextual signals that the company says other solutions do not address. It also enables Abnormal to correlate behavior indicators, user identity, and email content to detect attacks.
AppBase: Abnormal’s AppBase provides a directory of applications integrated into the cloud email environment. where one can learn more about each application, including current app permissions.
PeopleBase: Abnormal’s “PeopleBase” provides a directory of each active user in the cloud email environment, while building profiles for each user based on their activity.
VendorBase: Abnormal’s VendorBase provides a directory of all vendors that an organization works with via email and assigns a risk score based on the vendor’s communication activity.
TenantBase: Abnormal’s TenantBase highlights changes to mail tenant configurations, including conditional access policy changes that could bring risk into the cloud email environment.
Role-Based Access Control (RBAC): This feature allows security teams to ensure Abnormal Portal users maintain the right amount of access to the Portal, data, features, and email content.
Tenant Management: Abnormal provides self-service tenant management which allows administrators to add tenants directly within the Abnormal Portal, thus automating integrations.
Notification & Alerts: With Abnormal, administrators can receive automated notifications across different email categories, from graymail updates to weekly threat alerts.
Audit Log: Abnormal provides a portal to meet audit requests and investigate potential risks if unauthorized users have been granted access.
Reporting: Abnormal also provides visual reports of historical attack metrics with trending data and additional insights.
Email Add-Ons
Abuse Mailbox Automation
Reviewing reported emails can be a large operational burden for many businesses; manually triaging user-reported phishing emails can consume hours of an analyst’s workweek. What’s more, there is a high false positive rate, meaning ~90% of user-reported phishing emails are safe after all, clogging the queue.
To solve this issue, Abnormal automatically sorts reported emails into three categories: malicious, spam, or safe. If malicious, Abuse Mailbox Automation locates and remotes other unreported emails in the same phishing campaign. Abnormal then sends a follow-up email to inform reporters of the outcome.
Email Account Takeover Protection
Account takeovers lead to expensive data breaches, which cost companies an average of $4.5 million according to Abnormal. In 2021, 33 million email credentials were stolen. To minimize account takeovers, Abnormal baselines normal end-user behavior, then detects deviations across logins, such as location or MFA methods. Then, Abnormal creates a case file for manual review. To kick attackers out of hijacked accounts, Abnormal forces password resets, blocks access, and ends all active sessions.
Email Productivity
Graymail, which Abnormal describes as "a type of email that you’ve technically solicited but may serve little to no purpose to you" like product newsletters, marketing emails, etc. that you might have opted into without thinking about it, can be a drain on productivity. On average, employees lose at least two business days a year sorting external emails, and the average employee receives 23 graymail messages per week.
This disproportionately impacts executives, who Abnormal says receive “nearly 3x” more graymail than average employees. Abnormal inspects inbound emails and identifies graymail using tens of thousands of signals from email tenants to build a behavior profile specific to each organization.
Once Abnormal categorizes a message as graymail, it is instantly moved into the Promotions folder. Since everyone has different preferences (some employees may want to have graymail) Abnormal learns the preferences of each user, meaning users have no need to create filtering rules or blocklists. Graymail statistics are stored on a dashboard, which highlights trends in daily volume, top graymail senders, and the most targeted users in the company.
Email Security Posture Management
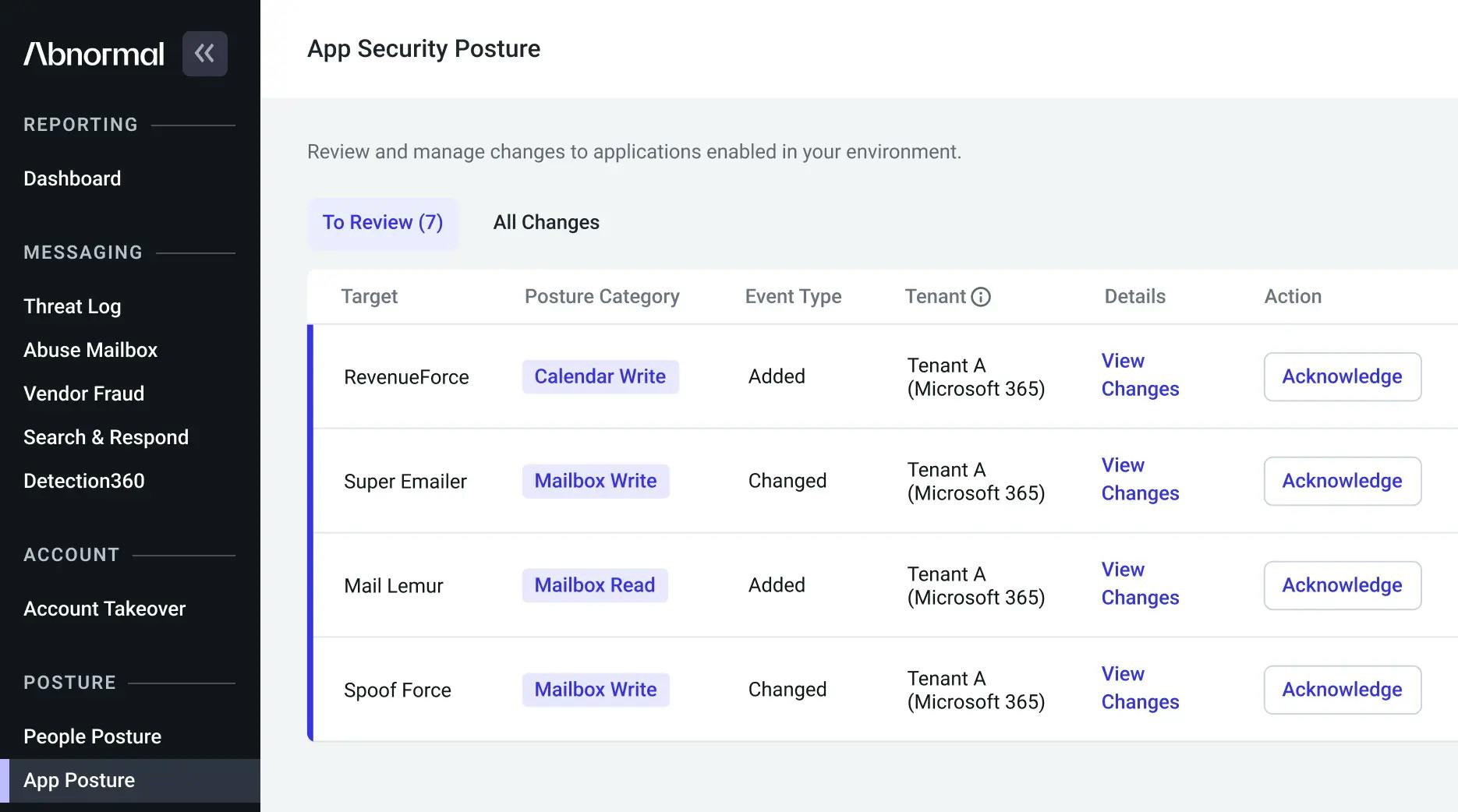
Source: Abnormal Security
Abnormal helps to discover and fix key security configuration risks across the cloud email environment. Cloud configurations remain an email security blind spot; attackers exploit configuration gaps across user accounts, third-party apps, and mail tenants, security teams often struggle to see posture changes and determine risk, and auditing is often manual and time-intensive.
Abnormal attempts to solve this issue by building behavioral profiles across environments in Knowledge Bases and operationalizing this data to surface changes in app permissions and user privileges. Surfacing high-impact changes to accounts, applications, and tenants eliminates the need for quarterly audios, PowerShell scripts, or spreadsheets.
Email-Like Add-Ons
Email-Like Messaging Security
Bad actors may launch attacks via email, but can also move to collaboration apps to send additional malicious content. An email breach can grant attackers unrestricted access to private data in Slack, or Teams; the most popular collaboration apps do not have robust built-in security scanning. Abnormal uses AI-based security to scan for suspicious links and detect malicious content in Slack, Microsoft Teams, and Zoom.
Email-Like Account Takeover Protection
Account takeovers often go unnoticed. An email compromise can provide full access to collaboration apps when corporate credentials are tied to employee email accounts. Account takeovers beyond the inbox bypass legacy email security tools and are hard to detect.
Abnormal surfaces suspicious authentication activity, correlating historically bad IPs and sign-in locations to highlight compromised accounts. Once the account is identified, Abnormal builds a case, giving teams a detailed timeline of suspicious authentication activity so teams are able to coordinate remediation. Abnormal integrates with providers like Okta to enrich each case with single sign-on activity, allowing security teams to see differences between IdP sessions and those initiated on Zoom or Slack.
Email-Like Security Posture Management
Excessive administrative rights result in higher risk. Abnormal compiles a running inventory of privilege changes across Slack, Teams, and Zoom, including timestamps and the users involved to see which changes may need further investigation. Admins can drill into an individual change to see a before-and-after view, providing insight into how the application was affected by the change.
Market
Customer
Abnormal’s target customers are large, established companies. As of August 2023, Abnormal served over 1.3K customers, including Maersk, ADT, Choice Hotels, Xerox, University of Kentucky, Mattel, Domino’s, and Avery Dennison, as well as more than 12% of the Fortune 500. Other notable customers listed on the company’s website as of January 2024 include Foot Locker, Liberty Mutual, and AAA.

Source: Abnormal Security
Market Size
Abnormal competes in the business email compromise industry. Business email compromise (BEC) alone is responsible for $51 billion in exposed losses from 2013-2023, one of the largest attack vectors on organizations. The business email compromise (BEC) market was valued at $1.2 billion in 2022 and is projected to reach a value of $4.4 billion by 2030 at a CAGR of 20.5%. In total, the email security market was valued at $3.9 billion in 2022. The market is growing at an 11.1% CAGR, with growth being driven by an increase in phishing activity; malicious phishing emails were found to have increased by 569% in 2022.
Competition
Proofpoint
Proofpoint was founded in 2002 by Eric Hahn, former CTO of Netscape. As of January 2024, it serves over 8K enterprises worldwide. In 2020, Proofpoint generated more than $1 billion in revenue, making it the first SaaS-based cybersecurity and compliance company to meet that milestone. In 2021, Proofpoint was acquired by Thoma Bravo in a transaction that valued Proofpoint at $12.3 billion.
As one consultant and customer stated in 2020, Proofpoint is the “800-pound gorilla in this space.” A Gartner customer review corroborated this sentiment, stating, “Proofpoint is an exceptional solution for Email security” However, Gartner reviewers rated Abnormal Cloud Email Security Platform higher than Proofpoint Email Security and Protection in the following categories as of January 2024: service and support, integration, and deployment, and evaluation and contracting.
Avanan
Avanan was founded in 2015 by Gil Friedrich (CEO), Avi Zelovich (CTO), and Don Byrne (CRO).
Avanan's enterprise email security solution is powered by AI to prevent phishing, malware, data leakage, account takeover, & shadow IT for cloud infrastructure, similar to Abnormal. Avanan says its AI solution leads to a 99.2% reduction in phishing attacks reaching the inbox, along with protection from ransomware, account takeover, BEC, and supply chain attacks. As a customer noted, Avanan “has the capability to also secure OneDrive and SharePoint… that's huge. “
Avanan was acquired by Check Point in 2021 for $300 million. Prior to the acquisition, the company had raised $40 million from investors such as Magma VC and StageOne Ventures. Gartner’s reviewers rated Abnormal Cloud Email Security Platform higher than Avanan for service and support as of January 2024.
Mimecast
Mimecast was founded in 2003 by Peter Bauer and Neil Murray. It provides an email security solution designed to protect organizations from a range of email-borne threats, offering features such as spam and malware filtering, data loss prevention, and advanced threat protection. As of January 2024, Mimecast serves over 40K customers in more than 100 countries, with more than 2K employees worldwide.
Reviewers on Gartner rated Abnormal Cloud Email Security Platform higher than Mimecast Email Security in the following categories as of January 2024: service, support, integration, deployment, evaluation, and contracting.
Business Model
Abnormal used a “per user, per year” pricing model as of 2020, according to Reiser. It can operate both as an email gateway and as a relay if using other security products. Pricing started at $35 per user per year as of 2021 according to a third-party source. The company does not publicly disclose pricing on its website.
Traction
In August 2023 surpassed $100 million in annual recurring revenue, Abnormal was #80 on Forbes Cloud 100 and was also listed in the Forbes AI 50 in 2023. Abnormal serves more than 5% of the Fortune 1000 and numerous notable companies, including Xerox, Hitachi Vantara, Urban Outfitters, Groupon, Royal Caribbean International, and AAA. Abnormal had a 99% renewal rate as of May 2022.
Valuation
Abnormal announced its $210 million Series C in May 2022 which valued the company at $4 billion and was led by Insight Partners, with participation from Greylock Partners and Menlo Ventures. This was its most recent round of funding as of January 2024, and the round brought the company’s total funding to $284 million.
Key Opportunities
Generative AI
In October 2023, Abnormal released a report entitled “The State of Email Security in an AI-Powered World” which looked at security leaders’ greatest concerns about the growing threat of generative AI in the enterprise and how they are planning to adapt their defenses in response.
Based on a survey of 300 senior cybersecurity stakeholders from organizations of all sizes across multiple industries, the research found that 98% of security leaders are concerned about the cybersecurity risks posed by ChatGPT, Google Bard, WormGPT, and similar tools. Not only are security leaders nervous about these threats, but many are already experiencing them. 80.3% of respondents confirmed that their organizations have either already received AI-generated email attacks or strongly suspect that this is the case.
The research highlights an opportunity for an alternative approach with AI-driven security as the next frontier of email protection, as 92% of survey participants see the value in using AI to defend against AI-generated email threats. As Abnormal CEO Evan Reiser noted in October 2023:
“The good news is that cybersecurity leaders recognize the need for a modernized approach to email security—one that puts AI at the center… With generative AI making it possible to create never-before-seen attacks at scale, it’s no longer enough to look for known indicators of compromise. There is a huge opportunity for security leaders to tap into the power of AI to effectively stop advanced attacks targeting their organizations—regardless of whether they were generated by AI or created by humans.”
Increasing Security Budgets Security
Budgets for security initiatives are sizable and remain a top priority for enterprises. A July 2022 survey of 60 CSOs within organizations of 500+ FTEs conducted found that ~30% of respondents reported paying more than $1 million for 3rd party security. CSOs plan to increase budgets, with ~1/4 of security budgets to increase by at least 50% in the next decade.
Key Risks
Alert Fatigue
All security players — from SIEM to phishing to EDR — generate alerts. As one customer lamented:
"There is nothing worse than getting a page Saturday at 2:00 a.m. about a printer that went down. I guess the worst thing ever […] would say the players that can alleviate alert fatigue, only send me an alert would it's actually needed, allow me to fine tune my alerts is important.”
Abnormal Security's sophisticated email threat detection capabilities, while effective, could inundate security teams with a surplus of alerts, potentially leading to alert fatigue. The behavioral analytics and machine learning algorithms employed by Abnormal may overwhelm security analysts with an excessive volume of notifications to investigate. Without streamlined processes for prioritizing and managing alerts, the influx of data could lead to overlooked genuine threats amidst the noise, exacerbating alert fatigue within security operations.
Summary
Abnormal Security, founded in 2018 by Evan Reiser and Sanjay Jeyakumar, addresses the rising threat of Business Email Compromise (BEC), one of the costliest forms of vendor attacks. BEC involves attackers hacking into corporate email accounts to defraud companies. Abnormal Security's core product is inbound email security, utilizing AI-based behavioral anomaly detection to identify attacks that traditional filters might miss. The company's market focus is on large enterprises, and it competes in the BEC industry, which was valued at $1.2 billion in 2022.
Abnormal Security, with a valuation of $4 billion after a Series C funding of $210 million in May 2022, surpassed $100 million in annual recurring revenue by August 2023. The company faces competition from established players like Proofpoint, Avanan, and Mimecast. Notably, it offers features like Abuse Mailbox Automation, Email Account Takeover Protection, and Email-Like Messaging Security. Abnormal Security aims to capitalize on the growing concern of generative AI in cybersecurity and the increasing budgets for security initiatives in enterprises. However, there's a potential risk of alert fatigue due to the sophisticated nature of its threat detection capabilities.