Thesis
From rising cybercrime to AI-driven threats, small and mid-sized businesses (SMBs) face increasing pressure to secure their systems with limited resources. As of April 2024, SMBs made up 99% of US businesses, yet often lack the staff, budget, or technical capacity to implement in-house cybersecurity programs. Breach costs for organizations with fewer than 500 employees reached $3.3 million in 2023, and in 2021, 61% of SMBs reported cyberattacks, with 82% facing ransomware. As a result, 94% of SMBs relied on managed service providers (MSPs) for security, up from 89% in 2022.
This increase in reliance comes as the nature of cyber threats evolves. Identity has become a primary attack surface, driven by the rise of hybrid work. As of November 2025, 78% of employees with remote-capable jobs worked remotely at least part-time, weakening traditional network perimeters and increasing exposure to threats. Accordingly, attackers have shifted to targeting user accounts, SaaS integrations, and authentication systems rather than physical networks. Identity-based attacks, including session hijacking, unauthorized OAuth apps, and business email compromise, have increased by 156% since 2023 and accounted for 59% of all confirmed incidents in early 2025.
The difficulty of managing the complexity of cyber threats is compounded by a global skills alignment gap. An estimated 3.5 million cybersecurity jobs remain unfilled as of 2023, but as of 2025, 52% of cybersecurity leaders attributed breaches to skills mismatches rather than headcount shortages. Organizations are focusing more on training and internal development instead of hiring. Although nearly two-thirds of CISOs report budget increases in 2024, staff expansion has slowed significantly, dropping from 31% in 2022 to 12% in 2024.
These challenges are unfolding alongside an escalating AI arms race. Cybercriminals use AI to launch faster, more sophisticated attacks, such as crafting phishing emails, automating malware evasion, and scanning networks for vulnerabilities at scale. As of March 2025, over 80% of phishing emails incorporated AI, and 87% of security professionals reported experiencing AI-driven attacks. While defenders are adopting AI tools like behavioral analytics, deception environments, and predictive defense to improve detection and response, AI alone remains unreliable: it struggles with binary decision-making and is prone to hallucinations, prompt injection, and bad reasoning. These systems require human oversight to validate and interpret AI output.
Huntress focuses on addressing these constraints. The company delivers managed cybersecurity services designed for SMBs and their MSP partners, combining automated detection with continuous human-led response. Its platform includes endpoint protection, identity threat detection, user training, and SIEM, provided as a bundled offering to reduce reliance on separate tools. Rather than replacing humans with automation, Huntress uses AI to support its analysts, helping SMBs access advanced threat response capabilities without needing to build internal security operations teams. As threats become more complex and identity becomes central to security, Huntress serves a segment of the market that remains underserved by enterprise-focused solutions.
Founding Story

Source: Forgepoint
Huntress was founded in 2015 by Kyle Hanslovan (CEO), Chris Bisnett (CTO), and John Ferrell (Co-Founder). The team brought experience from offensive cyber operations within the US military and intelligence community, including work on NSA Red Team activities and computer network operations (CNO). They started Huntress to address a gap in detecting persistent threats targeting small and mid-sized businesses (SMBs), a segment often exposed to cyberattacks but underserved by traditional vendors.
Hanslovan, referred to by some as the “Robin Hood of Cybersecurity,” enlisted in the military at 17, worked in counterintelligence, and later served as a cyber warfare operator at the NSA. He gained early recognition after winning DEF CON’s Capture the Flag competition and was later named to Baltimore Business Journal’s 40 Under 40. After several years in government contracting at ManTech, he co-founded StrategicIO in 2013 with Ferrell, a fellow ManTech engineer with expertise in Linux systems and computer network operations (CNO).
StrategicIO was a cybersecurity contracting firm focused on defense contracts. The company specialized in offensive cybersecurity services for government agencies and grew quickly, generating seven-figure annual revenue through subcontract work. Despite its success, Hanslovan and Ferrell recognized the limitations of a services-based model. They sought to build a scalable product company, and StrategicIO became the means to bootstrap Huntress, funding its early operations and enabling the founders to transition out of defense contracting. Hanslovan later described this decision as motivated by a desire for broader impact and a more sustainable business model.
Bisnett joined the Huntress team in 2015. A US Navy veteran and former NSA operator, he had prior startup experience, including a successful exit (LegalConfirm), and held technical roles at Raytheon, Oceans’ Edge, and ManTech. His background in exploit development and cloud infrastructure helped shape Huntress’s product architecture.
With the core team in place, Huntress focused on product validation. Leveraging their experience with persistent threats, techniques attackers use to maintain long-term access to systems, and often invisible to traditional EDR or AV tools, the founders prototyped a lightweight endpoint detection and response (EDR) agent. Tested through NSA Red Team channels, the tool successfully identified all 36 compromised systems in one test and outperformed incumbent vendors. Despite a clear product use case, the company struggled initially with go-to-market execution. The founders had limited SaaS distribution experience, and early sales were described as unfocused. Investor interest was also muted, in part due to Huntress’s government backgrounds, Maryland location, and SMB focus.
The company gained traction after committing to a channel-first strategy, selling primarily through managed service providers (MSPs), managed security service providers (MSSPs), and telecommunications companies that already provided security for downstream SMBs. Huntress prioritized integration into these partners’ workflows and focused on North American service providers managing endpoints. This approach helped the company build trust with MSPs and establish a foothold in a market segment often seen as fragmented or low-margin.
From its inception, Huntress was remote-first, mirroring the structure of intelligence teams that coordinate asynchronously across distributed geographies. Small, mission-focused teams were given significant autonomy, a model that remains central to its operations. Hanslovan attributes the company’s stability to the balance among the founding team. His focus on vision and communication was complemented by Bisnett’s technical rigor and Ferrell’s methodical approach to decision-making.
As Huntress grew, it expanded its leadership team. Marcos Torres joined as Finance Director and later became CFO, while Prakash Ramamurthy, former head of Oracle’s cloud security portfolio, became Chief Product Officer. Under Ramamurthy’s leadership, Huntress extended its platform beyond endpoint detection to include identity threat detection and response (ITDR) and security information and event management (SIEM), with plans for 10+ additional products. Executives from Oracle, the Department of Defense, and Raytheon have since joined the team.
In August 2025, former CISA director Jen Easterly joined the Huntress board as a strategic advisor in her first private sector role after leaving the government. Hanslovan said of Easterly that “She’s arguably the single most transformative US government cybersecurity leader of our time, and her work at CISA set the gold standard for making critical resources accessible to the masses.”
Product
Platform Overview
The Huntress Managed Security Platform is a cybersecurity solution designed for small and mid-sized businesses (SMBs). It provides centralized management for endpoint, identity, and employee security through a single dashboard. The platform is structured to support organizations with limited IT resources and is operable by generalist or junior IT staff.
Key components include a 24/7 Security Operations Center (SOC) that provides continuous monitoring, analysis, and response. The platform combines automated threat detection with analyst review to reduce false positives, reporting a 0.7% false positive rate. It is designed to have minimal system impact, using less than 1% of CPU resources.
The platform provides centralized tools for detecting and responding to cybersecurity threats. Its persistent foothold detection feature scans for unauthorized persistence mechanisms on Windows and macOS systems and removes them as needed. Integration with Microsoft Defender allows for centralized antivirus configuration and incident tracking. To detect ransomware activity, the platform uses decoy files that trigger alerts if modified or encrypted. It also includes external reconnaissance capabilities that identify exposed ports and services, helping flag potential vulnerabilities in a system’s perimeter.
For employee-focused security, the platform includes Security Awareness Training (SAT) that delivers training episodes, phishing simulations, and usage reporting. Huntress also maintains an ongoing education program through monthly webinars, multi-day security events, and a resource library containing technical guides, videos, and tabletop exercises.
The platform is designed for rapid deployment and routine operation without requiring specialized security personnel. All features are integrated and managed through a unified dashboard. The core solutions housed on this platform are described in further detail below.
Managed Endpoint Detection and Response
Source: Huntress
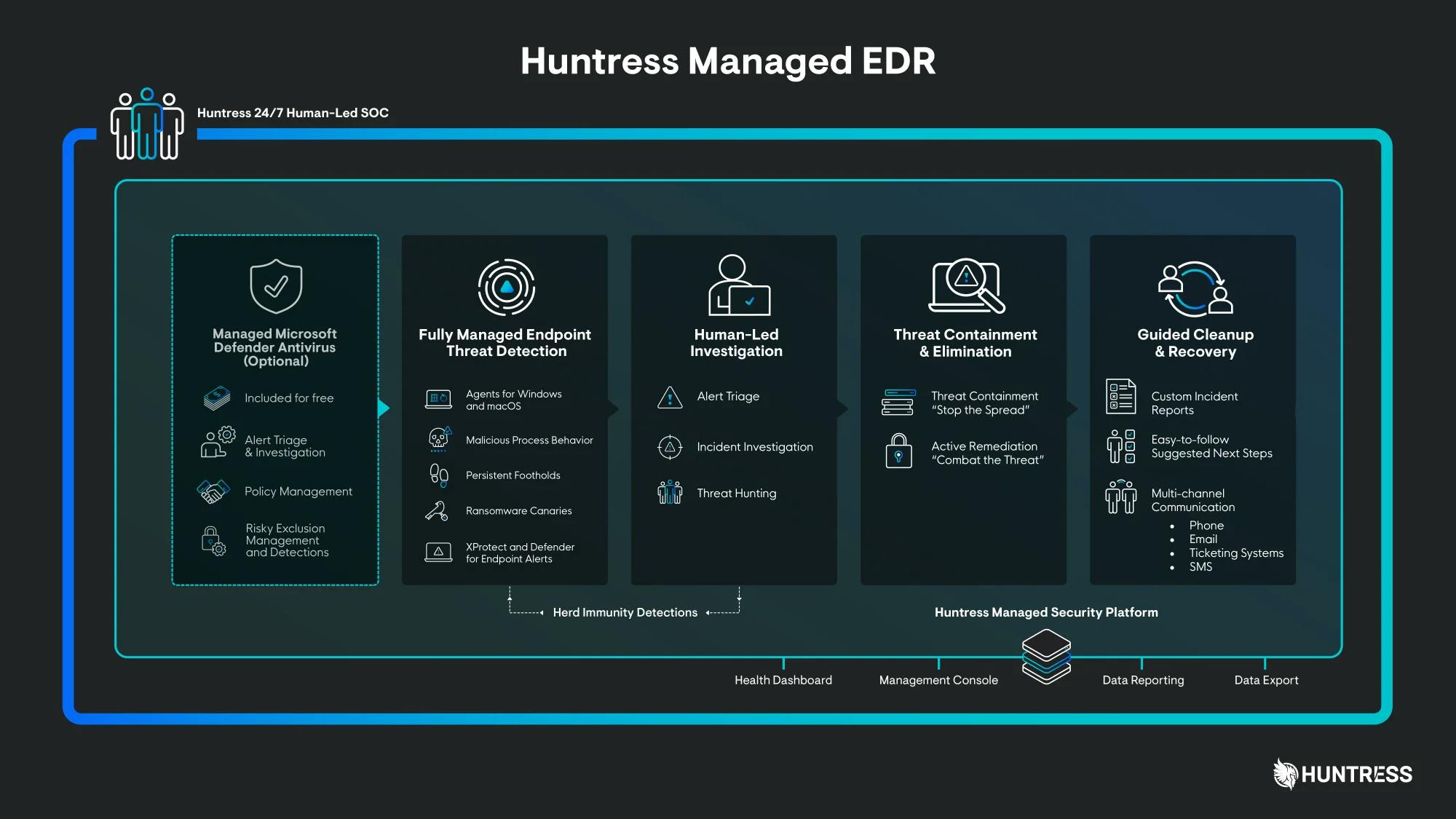
Huntress’s Managed Endpoint Detection and Response (EDR) provides continuous monitoring, detection, and response for threats targeting endpoint devices. These include laptops, desktops, and servers, which are common entry points for attacks such as malware, unauthorized access, and ransomware. The platform is supported by a 24/7 human-led Security Operations Center (SOC) and was deployed across more than 4 million endpoints as of November 2025. As of 2025, the service maintained a mean time to respond (MTTR) of eight minutes, with a reported false positive rate of under 1% and a customer satisfaction score of 98.8%. Huntress’s EDR service identifies threats using persistent foothold detection, malicious process behavior analysis, ransomware canaries, and external reconnaissance.
Persistent Foothold Detection: The platform identifies persistence mechanisms that allow attackers to maintain long-term access to systems, often by embedding themselves in legitimate software or system configurations. Upon deployment, Huntress agents scan for and collect data related to known and unknown footholds. This data undergoes automated analysis, and potential threats are reviewed by the SOC. Verified threats are documented in custom incident reports, which include detailed context and remediation instructions. Remediation can be executed directly in the platform with one click. In addition to automated detection, the SOC conducts proactive threat hunting to identify and remove footholds before further compromise. Customers also receive access to educational materials, such as the Persistence Knowledge Kit, to better understand attacker tactics.
Malicious Process Behavior Analysis: Huntress monitors live system processes to detect suspicious behavior, including unauthorized privilege escalation, lateral movement, and malware execution. This behavior-based approach does not rely on pre-defined malware signatures but instead looks for patterns that match known attacker techniques. When activity is flagged, the platform aggregates related system data to build a contextual understanding of the threat. SOC analysts then review and validate each incident and provide a written summary with suggested actions. Customers receive detailed incident reports and remediation guidance, which may be executed automatically or manually. The focus on attacker behaviors allows Huntress to detect and respond to threats that may bypass traditional antivirus tools.
Source: Huntress
Ransomware Canaries: To detect ransomware at an early stage, Huntress uses a “canary system,” a method borrowed from early-warning practices. The platform places lightweight, harmless decoy files—called "canaries"—on protected systems. These files are not used for any operational purpose but are monitored closely for unexpected modifications. If ransomware attempts to encrypt or alter a canary file, it triggers an immediate alert to the SOC. Analysts then investigate the alert and initiate a response to contain the threat. This approach allows Huntress to quickly identify affected endpoints and take action before the ransomware spreads. The canary files are designed to consume minimal system resources and integrate with standard incident response processes.
External Reconnaissance: Huntress scans for publicly accessible services and misconfigurations, such as open RDP, SMB, or SQL ports, that could be exploited by attackers. These external-facing vulnerabilities can serve as initial access points in an attack. Scan results are enriched using Shodan.io, a search engine for internet-connected devices and exposed systems, to provide details such as the type of service, port number, and last observed activity. Customers receive visibility into risky configurations or weak points in customer environments, and are advised on corrective actions. These scans are run regularly to monitor for new exposures or system changes that could introduce risk.
Threat Response: When a threat is detected, the Huntress SOC follows a standardized process: endpoint agents collect suspicious activity, analysts manually review the data, analysts generate incident reports, and customers receive guidance on next steps. Recommended remediation actions can be executed within the platform via one-click commands or performed manually with included instructions. This process combines automation with expert review to reduce false positives and ensure a timely, accurate response. As of November 2025, Huntress maintained a 98.8% customer satisfaction score for its SOC-led threat response.
Managed Microsoft Defender: Huntress offers configuration and ongoing management of Microsoft Defender Antivirus as an optional service. Through the Huntress dashboard, customers can centrally manage Defender settings, including scan schedules, detection policies, and exclusions. This is available across Defender for Endpoint, Defender for Business, and Defender on macOS. Huntress analysts tailor Defender settings to align with each customer’s environment, enhancing its built-in protection and improving visibility for incident detection and response.
Together, these managed EDR capabilities allow organizations to detect and respond to a wide range of endpoint threats, such as persistence mechanisms, malware, privilege abuse, and ransomware, using a combination of automated analysis, behavioral detection, and human-led investigation.
Managed Identity Threat Detection and Response
Source: Huntress
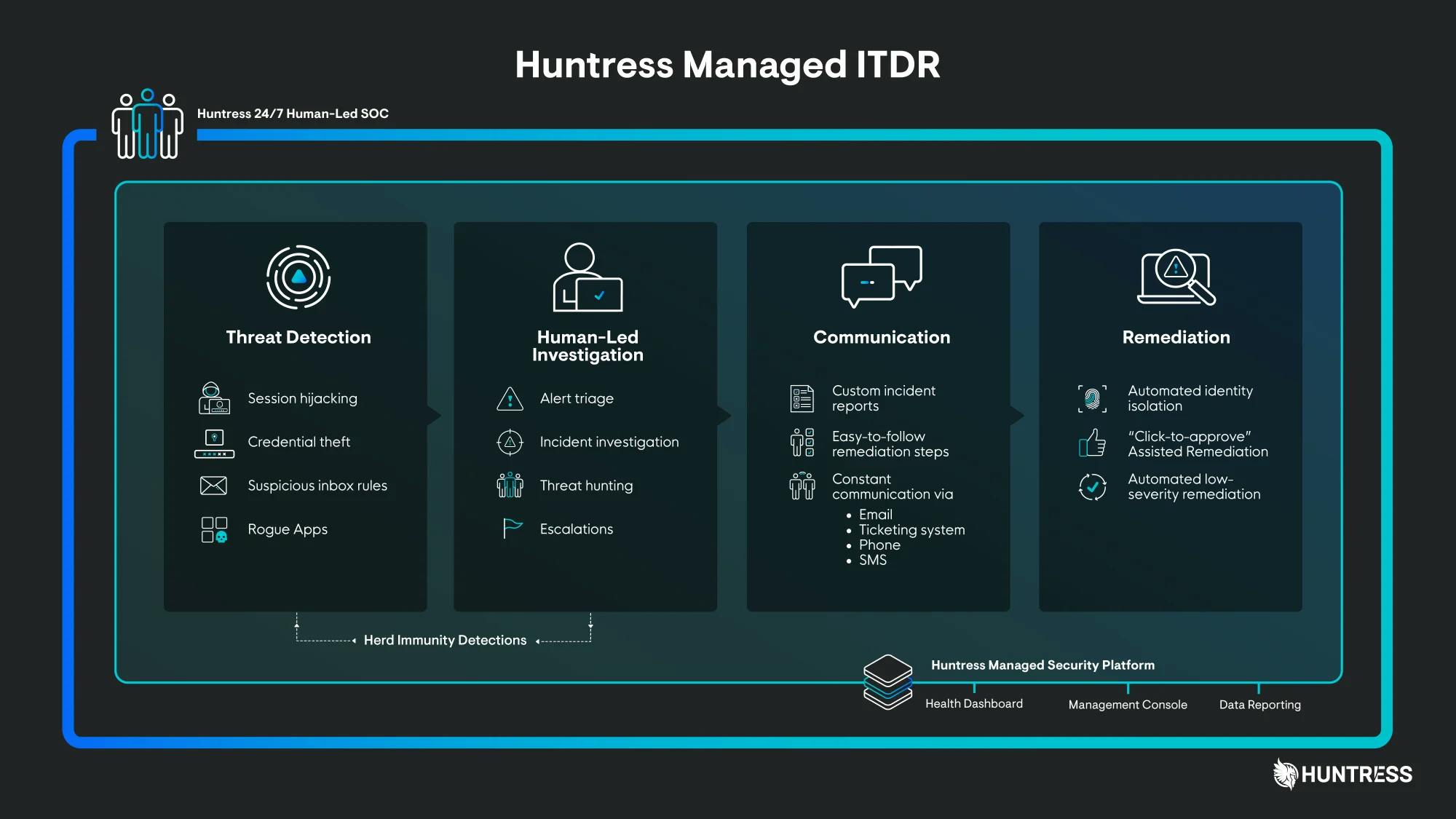
Huntress’s Managed Identity Threat Detection and Response service (ITDR) protects Microsoft 365 environments by monitoring for threats that target user identities, such as compromised accounts, unauthorized logins, or unusual user behavior, rather than focusing on devices or network traffic. ITDR solutions are designed to identify and stop attacks that bypass traditional endpoint security, including techniques like phishing, session hijacking, and unauthorized access using stolen credentials. Huntress’s Managed ITDR provides continuous monitoring without requiring premium Microsoft licenses, making it a cost-effective option for small and mid-sized businesses. When a threat is detected, the system offers both automated and guided response options to help organizations respond quickly and contain incidents.
The service monitors for several common threat patterns. It detects session hijacking, where attackers bypass multi-factor authentication by stealing session tokens and using them to take over accounts. It also monitors for credential theft, locking down compromised accounts to prevent unauthorized access. Location-based anomalies are flagged when login attempts come from unexpected geographic regions or suspicious VPNs. In cases of rogue applications, Huntress identifies unauthorized third-party apps that request excessive access to user data through OAuth permissions, commonly known as “traitorware” or “stealthware.” The platform also defends against shadow workflows, such as inbox forwarding rules and filters that attackers use during business email compromise (BEC) attacks.
When a threat is identified, Huntress provides containment and remediation support. This may involve automated lockouts, guided instructions for IT teams, or both. As reported by one customer, Huntress’s ITDR service enabled containment and response to 100% of their BEC incidents over two years, due to the platform’s fast reaction time and account lockdown capabilities.
Managed Security Awareness Training
Source: Huntress

Source: Huntress
Huntress offers a fully managed Security Awareness Training (SAT) platform designed to reduce human-related security risks, one of the most common vectors for cyberattacks. The platform combines phishing simulations, educational videos, and behavior-based interventions to build long-term security awareness across a workforce. It was developed following Huntress’s acquisition of Curricula, a security training firm known for its engaging, narrative-driven content.
The SAT platform features short, story-based training episodes informed by real-world threat intelligence gathered from millions of endpoints and over 100K protected organizations. Content is created by Huntress’s internal security experts and regularly updated to reflect evolving attacker tactics. Lessons are designed using adult learning principles to improve engagement and retention. These lessons include relatable scenarios, threat simulations, hands-on experiences, and episodes with recurring characters like heroes and villains.
Administrators can automate training through directory integrations, schedule lessons and reminders, and track progress using a centralized dashboard. The platform supports custom training content and allows organizations to apply internal branding, including logos, policies, and color schemes.
In addition to training modules, Huntress manages phishing simulations end-to-end. These campaigns include design, delivery, and automated follow-up. Users who interact with simulated phishing emails receive just-in-time coaching to reinforce secure practices. A self-service option is also available, allowing organizations to create and manage their own simulations using built-in dashboards and reporting tools.
Source: BizGuard
The platform also delivers targeted coaching to users who demonstrate risky behavior, with behavior-based training assignments designed to reduce repeat incidents. Reporting includes metrics on simulation click rates, course completion, and compliance readiness.
Together with Huntress’s Managed Identity Threat Detection and Response (ITDR), the SAT platform forms part of a broader strategy to mitigate identity-based and human-layer threats through monitoring, education, and behavior change.
Managed Security Information and Event Management
Huntress’s Managed SIEM platform is designed to streamline threat detection and compliance for small and mid-sized businesses by filtering out irrelevant security data and surfacing only actionable insights. The system simplifies threat response while reducing the operational burden on IT teams.
At its core is a proprietary filtering engine that analyzes security logs and events across multiple sources such as endpoints, firewalls, VPNs, and identity systems, and narrows them down to the activity that genuinely warrants investigation. This smart filtering reduces alert fatigue and investigation time while keeping operational costs in check.
The platform supports threat hunting and analysis led by Huntress’s Security Operations Center (SOC). SOC analysts monitor for known attacker tradecraft, such as remote desktop protocol (RDP) brute-force attempts, and conduct ongoing investigations to detect threats earlier in the attack lifecycle. When incidents are confirmed, the SOC delivers detailed incident reports that include step-by-step remediation guidance or offers fully managed response services.
The system helps organizations meet long-term compliance by storing encrypted logs for up to seven years and following industry and regional data rules. It pulls together logs from different sources to give a clear, central view of security activity while supporting regulatory needs. Huntress SOC analysts keep the platform up to date by adjusting detection rules, removing false positives, and responding to new threats, allowing internal IT teams to focus on more strategic work.
Market
Customer
Huntress serves over 105K small and mid-sized businesses (SMBs), primarily in the United States, with plans to expand into Canada, the United Kingdom, Europe, Australia, and New Zealand as of March 2025. Its customers include internal IT teams, value-added resellers, and a large network of managed service providers (MSPs) and managed security service providers (MSSPs), which are central to the company’s go-to-market model. These MSPs, including Tech Keys, 1Path, Logically, and Intelligent Technical Solutions, collectively support nearly 100,000 SMBs and have played a key role in Huntress’s growth and customer engagement. For example, during the 2021 Kaseya VSA supply chain attack, which deployed ransomware through vulnerable remote management software and disrupted thousands of MSPs and clients, Huntress organized a “war room” to coordinate response efforts and protect systems. This built loyalty and trust with MSPs.
SMBs use the Huntress platform to detect, respond to, and recover from a range of cyber threats. Stamm Tech, an MSP, used the platform to investigate a compromised CEO email account, remove malicious inbox rules, and reestablish multi-factor authentication. Cytek responded to a ransomware incident affecting a dental client by isolating the threat, restoring access, and performing forensic analysis. Cascade Technologies stopped a phishing-delivered remote access trojan, while East Coast Metal Distributors used Huntress to analyze and contain a crypto virus infection. Huntress also supports direct customers such as Cohere Health, Standard Supply, TELCOR, and Ronald McDonald Charity Houses, offering managed tools for detection, remediation, and training across diverse industries.
Industry Coverage
The company maintains a diversified customer base across multiple industries, including healthcare, education, financial services, manufacturing, and the public sector.
Healthcare: Huntress serves over 14K healthcare organizations, including members of the United/Change Healthcare network. The healthcare sector remains a high-risk target, with 133 million data breaches reported in 2023 alone. As of 2025, it took an average of 231 days to detect these breaches, 36% of which originated from phishing or other malicious emails. Smaller providers often face budget constraints and regulatory scrutiny. Huntress supports these organizations through managed threat detection, remediation, and training tools. For example, Cohere Health uses Huntress’s Security Awareness Training (SAT) to meet HIPAA compliance requirements through continuous staff education and phishing simulations.
Education: In education, schools and universities are targeted due to limited IT resources and the sensitivity of their data. In 2023, ransomware attacks affected 79% of higher education institutions, with recovery costs estimated at $9 billion. By 2024, over 20% of cyber incidents tracked by Huntress involved educational institutions. Huntress helps minimize data loss and learning disruptions by offering managed protection and response services.
Financial institutions: Financial institutions face constant threats. As of 2025, over 46 million cyberattack signals are detected globally each day, with many aimed at banks. In 2023, 64% of financial institutions experienced ransomware incidents, and malware accounted for 40% of all attacks in the sector. In 2025, the average cost of a financial breach was estimated at $4.5 million, with more than 16 million daily transactions at risk. Huntress provides monitoring, remediation, and compliance tools to help protect financial data and maintain customer trust.
Manufacturing and construction: Manufacturing and construction companies also face rising cyber risk, likely due to operational complexity and high transaction volumes. In 2023, Brunswick Corporation reported $85 million in cyber-related losses, while Applied Materials reported $250 million. By 2024, 70% of construction firms had experienced phishing attacks. Huntress helps mitigate these threats, which can disrupt operations or compromise supply chains.
Local government: State and local governments continue to face growing cyber threats. In 2023, public administration entities experienced 3.3K cyberattacks and 582 confirmed breaches. From 2022 to 2023, endpoint and data breaches in this sector rose by 313%, with the average cost to contain an incident reaching $2.6 million. Huntress supports these entities by helping secure interconnected systems and reduce operational risks.
Market Size
As of November 2025, Huntress operated in the cybersecurity market for small and mid-sized businesses (SMBs), offering managed solutions across endpoint detection and response (EDR), identity threat detection (ITDR), security information and event management (SIEM), and security awareness training (SAT), all supported by a human-led Security Operations Center (SOC). As of June 2025, the SMB cybersecurity market was valued at $25 billion in 2023 and was projected to reach $70 billion by 2034, growing at a compound annual growth rate (CAGR) of 11% during the 2025–2034 period.
The financial impact of cyberattacks was expected to exceed $10.5 trillion globally by the end of 2024. With 34 million SMBs in the US and 400 million worldwide, this segment represents a large and growing market. Huntress’s focus on SMBs gives it access to a sizable portion of global demand for managed cybersecurity services.
Competition
Huntress competes in the cybersecurity market alongside a wide range of providers offering threat detection and response tools. This includes large companies like CrowdStrike, SentinelOne, Sophos, and Bitdefender, as well as smaller firms such as Blackpoint, Blumira, Red Canary, and ThreatLocker. The market is fragmented, with some companies focusing on large businesses and others offering more specialized services with teams of human analysts.
As of November 2025, Huntress held about 8.9% of mindshare in managed detection and response. Unlike many competitors that sell directly to large companies, Huntress focuses on small and mid-sized businesses and works through managed service providers (MSPs) who handle IT and security for these customers.
Huntress’s focus on low system impact and ease of use sets it apart from competitors that require more complex setups or heavier resources. Huntress’s Managed EDR agent uses less than 1% CPU, making it lightweight and easy to run on most systems. By comparison, Bitdefender’s agent consumes around 24% CPU, Sophos uses 24–30%, SentinelOne up to 5%, Webroot around 6% (and often requires manual fixes), and Kaseya (formerly Datto) about 3%. CrowdStrike matches Huntress with less than 1% CPU usage. The company has also built credibility by sharing information during major security events and offering educational resources, while its MSP-focused strategy has enabled faster growth than traditional sales models.
Managed EDR
Crowdstrike: CrowdStrike, founded in 2011, is a publicly traded cybersecurity company with a market cap of $135 billion as of November 2025. The company’s core product is the Falcon platform, a cloud-native suite that delivers AI-powered endpoint protection, real-time threat detection, threat intelligence, and incident response. Before its IPO in 2019, CrowdStrike raised approximately $481 million across six funding rounds from investors including Accel, Google Capital, IVP, and General Atlantic.x
CrowdStrike primarily serves large enterprises and public sector organizations through a combination of global direct sales and channel partnerships. Its business model emphasizes scale, offering a wide range of specialized tools, over 40 SKUs, across endpoint, cloud, identity, and workload protection. While this modular approach provides flexibility for complex IT environments, it can also lead to pricing and packaging complexity.
In contrast, Huntress focuses on small and mid-sized businesses (SMBs) and managed service providers (MSPs), offering a bundled cybersecurity platform that includes endpoint protection, identity threat detection (ITDR), security awareness training (SAT), and managed SIEM. Unlike CrowdStrike, which requires a 300-endpoint minimum for managed services and often charges separately for support, Huntress offers transparent per-endpoint pricing with SOC support and remediation included, aiming to simplify adoption and reduce overhead for smaller organizations.
Bitdefender: Bitdefender, founded in November 2001 as a spinout from Romanian software company Softwin, is a privately held global cybersecurity firm. The company provides endpoint protection, antivirus, and advanced threat detection to a broad range of customers, including consumers, small and mid-sized businesses (SMBs), and enterprises. Its capabilities are delivered through the GravityZone platform, which includes Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR) services. As of November 2025, Bitdefender had raised $187 million across two funding rounds, with its last known valuation at approximately $600 million based on a secondary market transaction in 2017. As of July 2025, the company was reportedly planning an initial public offering in 2026.
Bitdefender operates as a legacy vendor offering a broad product suite through global channel partnerships. While it provides robust tools for enterprise environments, many of its advanced features, such as MDR and fully managed EDR, require upgrades to premium licenses or add-on services. This structure can result in higher total costs and more complex management, particularly for SMBs. Huntress focuses on serving SMBs and managed service providers (MSPs) with a security platform that includes managed EDR, 24/7 SOC support, and remediation under a flat-rate pricing model. The platform is designed to reduce alert volume and provide operational support for organizations without dedicated security staff.
Managed ITDR
Blackpoint: Blackpoint Cyber, founded in 2014 by former NSA cyber operations expert Jon Murchison, is a privately held cybersecurity company that provides Managed Detection and Response (MDR) services through managed service providers (MSPs). Its platform, SNAP-Defense, offers 24/7 threat monitoring, automated containment, and incident response. As of November 2025, Blackpoint had raised a total of $207 million in funding, including a $190 million Series C round led by Bain Capital Tech Opportunities and Accel. Other investors include Adelphi Capital Partners, Telecom Ventures, Pelican Ventures, and WP Global Partners.
Blackpoint uses third-party EDR tools for its MDR service, offering flexibility but limiting control over telemetry and response. Huntress uses its own EDR infrastructure, reporting an average response time of eight minutes in 2025, compared to a reported 27 minutes (seven for cloud incidents) for Blackpoint. Both companies serve SMBs through MSP partners, but differ in approach. Huntress also provides educational content like Tradecraft Tuesdays to support IT teams with limited security expertise.
Blumira: Blumira, founded in 2018 in Ann Arbor, Michigan, is a privately held cybersecurity company offering a cloud-native extended detection and response (XDR) platform. Its product combines SIEM, limited endpoint visibility, and automated threat response, targeting small and mid-sized businesses (SMBs) with lean IT teams. As of November 2025, Blumira had raised $27.9 million in total funding, including a $15 million Series B round in 2023 led by Ten Eleven Ventures, with participation from RPS Ventures, Mercury, Hyde Park Angels, and Jon Oberheide.
Blumira offers a lightweight, software-based deployment model with flexible pricing, including a free tier. However, as of November 2025, the platform lacked a fully managed SOC. Alerts are surfaced to customers but require internal triage and response. In contrast, Huntress includes 24/7 human-led SOC coverage, managing threat investigation and remediation on the customer’s behalf. Huntress offers functionality across endpoint, identity, SIEM, and training. Its cloud-based SIEM does not require hardware and includes filtering to reduce false positives. Blumira requires a Linux collector for each client and may generate more manual alerts. Huntress provides process-level telemetry through its own EDR, while Blumira relies on third-party tools with less detailed visibility.
Managed Security Awareness Training
KnowBe4: KnowBe4, founded in 2010, is a cybersecurity company focused on Security Awareness Training (SAT) and phishing simulation. Its platform is designed to help organizations reduce user-driven security risks by educating employees about social engineering and phishing tactics. KnowBe4 had raised $693.5 million in total equity funding, including a $300 million Series C round in 2019 led by KKR, which brought the company to a $1 billion valuation, before it was acquired by Vista Equity Partners in 2023.
KnowBe4 focuses primarily on training and phishing simulation, without offering detection, protection, or response capabilities. It offered managed service at an additional cost. Huntress includes training as part of a broader managed platform that also provides EDR, identity protection, SIEM, and 24/7 SOC support. Huntress incorporates current threat data into its training materials, while Huntress reports that KnowBe4’s content has been noted for slower updates in response to emerging threats.
Managed SIEM
Red Canary: Red Canary, founded in 2014, provides cloud-based Managed Detection and Response (MDR) services that combine behavioral analytics, automated response playbooks, and 24/7 SOC monitoring across endpoints, networks, and cloud environments. The company had raised $129.9 million across five funding rounds, including an $81 million Series C in 2021 led by Summit Partners, prior to being acquired by Zscaler in May 2025.
Red Canary focuses on mid-market and enterprise customers and relies on third-party endpoint detection and response (EDR) tools. Customers must procure and manage their own EDR, and some automation features may require additional fees. While this allows integration flexibility, it can add complexity for organizations without dedicated security teams. Huntress develops and maintains its own EDR and includes 24/7 SOC support, threat containment, and remediation in a bundled offering. It targets SMBs and managed service providers that may lack the capacity to manage multiple security tools. Red Canary’s acquisition by Zscaler may also bring changes as its offerings are absorbed into a broader enterprise platform.
Business Model
Revenue
Huntress generates revenue through a subscription-based model, with pricing tied to usage across its various cybersecurity products. Customers are charged based on the number of endpoints, user identities, active users, or data sources, depending on the product.
Managed EDR: Customers pay a recurring fee based on the number of endpoints protected. The subscription includes 24/7 monitoring by Huntress’s Security Operations Center (SOC), antivirus management through Microsoft Defender, incident remediation, and custom reporting.
Managed ITDR: Pricing is based on the number of user identities monitored. This product provides SOC-led monitoring and response for identity-related threats, particularly within Microsoft 365 environments.
Managed SAT: Pricing is based on the number of active users enrolled in training. This service includes phishing simulations, cybersecurity awareness training modules, and automated progress reporting.
Managed SIEM: Pricing is according to the number of integrated data sources. It includes pooled data storage and a flat-rate billing structure that allows organizations to consolidate logs from multiple systems.
Costs
Huntress appears to operate an asset-light model that does not depend on physical infrastructure, hardware, or capital-intensive equipment. The company’s main expenses are likely concentrated in areas tied to service delivery and customer support.
A significant portion of costs is believed to be related to staffing its 24/7 Security Operations Center. Because Huntress provides human-led threat detection and response, it must maintain a team of analysts to continuously monitor customer environments and address incidents in real time.
Research and development is considered another major area of investment. Huntress regularly updates its detection capabilities across endpoint, identity, and log-based systems to keep pace with evolving threats and maintain the relevance of its products. As of June 2024, some of its Series D funding had been earmarked for security research.
The company is also likely to invest in sales, marketing, and partner enablement. Given that Huntress sells primarily through managed service providers and targets small and mid-sized businesses, resources are likely devoted to acquiring, supporting, and training partners and customers at scale.
Traction
Huntress launched its managed endpoint detection and response (EDR) platform in 2020 to address growing cybersecurity needs among small and mid-sized businesses (SMBs). In January 2021, it acquired EDR and network visibility technology from Level Effect to strengthen its detection capabilities. In May 2021, the company raised a $40 million Series B round led by JMI Equity and Forgepoint Capital to expand its reach through enhanced reseller and MSP partnerships.
In both 2021 and 2022, Huntress doubled its annual revenue, driven by increasing demand from MSPs and SMBs. To broaden its product suite and address the human side of cybersecurity, Huntress acquired Curricula in July 2022, adding security awareness training and phishing simulations to its offerings under what is now Managed SAT.
By May 2023, Huntress had protected over 2 million endpoints. It raised a $60 million Series C led by Sapphire Ventures, with JMI and Forgepoint returning, to support global expansion. In September 2023, it launched Managed ITDR for Microsoft 365, expanding into identity threat detection to address rising identity-based attacks.
In 2024, Huntress closed a $150 million Series D round led by Kleiner Perkins, Meritech Capital, and Sapphire Ventures. That year, it also launched Managed SIEM, rounding out its transition from a single-product company to a broader cybersecurity platform. As of 2024, Huntress worked with over 4.3K MSP partners, protected over 105K organizations, and secured more than 3.5 million endpoints. The company was expected to reach $100 million in ARR, with annual revenue growth exceeding 70%.
In July 2025, Huntress announced a strategic collaboration with Microsoft to integrate its security tools with Microsoft Defender and Microsoft 365 licenses. This partnership aimed to improve protection for businesses already using Microsoft tools by layering Huntress’s EDR, ITDR, SIEM, and SAT offerings into familiar environments, helping customers better operationalize Microsoft’s built-in security features.
Revenue growth has largely been driven by increasing adoption of additional products by existing customers rather than solely by acquiring new logos. The company’s infrastructure allows telemetry to flow across modules, enabling cross-product correlation. Hanslovan has described Huntress’s strategy as that of a “1.5 mover”—not the first to market, but early enough to build an advantage through focus, speed, and disciplined execution.
In October 2025, Huntress initiated a distribution partnership with global cloud distributor Sherweb to enable Huntress products to be accessed by MSPs in North America, the UK, and Ireland. This was Huntress’s first partnership, with Hanslovan saying of the partnership, “Together, we’re not just scaling globally - we’re making enterprise-grade cybersecurity accessible to every MSP.”
Valuation
As of November 2025, Huntress had raised a total of $309.8 million across seven funding rounds. In June 2024, the company closed a $150 million Series D round led by Kleiner Perkins, Meritech Capital, and Sapphire Ventures. The round valued Huntress at $1.6 billion. Other notable investors in earlier rounds included JMI Equity, Forgepoint Capital, and SaaS Ventures. In 2024, funding for AI-focused cybersecurity companies grew 96% year over year. Huntress distinguished itself during this period by maintaining a human-centric model for threat detection and response, in contrast to peers that prioritized automation and machine learning.
Key Opportunities
Human-Enhanced Security
Many organizations have adopted AI-driven security tools for their efficiency and scalability. However, concerns about false positives, limited contextual understanding, and a lack of transparency in how these systems make decisions have raised skepticism and backlash. In practice, human intervention can be critical to validate or interpret alerts, particularly when benign activity is misclassified or when alerts lack sufficient context.
Huntress combines automated detection with human-led threat validation through a 24/7 Security Operations Center (SOC), where analysts review and verify incidents before alerts are issued. This process has reduced false positives to under 1% and helps prioritize actionable threats. The platform avoids the limitations of opaque AI decision-making by incorporating analyst review and includes threat detection tools such as ransomware canaries, persistent foothold monitoring, and integrations with Microsoft 365 and Defender. The model is designed to support organizations that require assistance in assessing and responding to potential threats without large internal security teams.
Identity-Based Perimeters
As hybrid work and cloud-based software adoption grow, traditional network perimeters, once defined by firewalls and on-premises infrastructure, are losing relevance. With 52% of US employees in remote-capable roles working hybrid and another 26% fully remote as of July 2025, corporate systems are accessed from various devices and locations. At the same time, the SaaS market size reached an estimated $420 billion as of June 2025, outpacing broader IT spending. As a result, identity has become the main control point for access and security, a shift often referred to as "identity as the new perimeter."
Protecting user credentials, monitoring login behavior, and detecting identity misuse have become key components of security. Identity-based attacks, including session hijacking, unauthorized OAuth apps, and business email compromise, have increased by 156% since 2023 and accounted for 59% of all confirmed incidents in early 2025. Huntress’s Managed Identity Threat Detection and Response (ITDR) monitors identity threats alongside endpoint activity and user training. For small and mid-sized businesses and managed service providers, this integration offers a way to secure user accounts without large in-house teams.
This also supports emerging regulatory expectations. As frameworks like zero-trust and data privacy rules evolve, organizations may need to show identity controls such as multi-factor authentication (MFA), monitoring, and response protocols. As of 2021, 54% of SMBs had not implemented MFA. Huntress includes these controls as part of its core offering.
SaaS Usage Expansion
As the global SaaS market grows from $358.3 billion in 2024 to a projected $408.2 billion in 2025, app vendors are seeking simpler ways to secure their platforms without integrating full endpoint detection agents. As of 2025, 55% of organizations reported employees using SaaS applications without involving security teams, creating visibility gaps. Huntress has an opportunity to address this by offering a lightweight, embedded detection and response layer that SaaS providers can bundle directly into their apps. Through containerized middleware or SDKs, Huntress can deliver behavioral monitoring, automated alerts, and SOC response from within the application itself. This can help vendors close blind spots while extending Huntress’s reach into the growing cloud app ecosystem.
Key Risks
SMB Budget Constraints
Huntress may face challenges in driving adoption and expansion within its core SMB customer base due to limited cybersecurity budgets. 47% of businesses with fewer than 50 employees reported having no cybersecurity budget at all as of January 2025. Even amid increasing threat levels, only a small percentage of SMBs—7% in 2024—planned to increase security spending by 10% or more. These budget limitations, coupled with a tendency to prioritize short-term operational needs over long-term security investments, may constrain demand for Huntress’s offerings or slow the pace of customer upgrades and renewals.
Competition from Incumbents
Huntress may face pressure from large technology providers that are increasingly offering built-in security tools as part of their core products. Companies like Microsoft and Google are bundling endpoint and identity protection directly into their cloud services and operating systems, often at little or no additional cost. For example, Microsoft Defender for Business is included with Microsoft 365 Business Premium and provides security coverage for up to 300 users without requiring separate licensing or installation.
As these built-in tools become more sophisticated, adding AI-driven detection and automated response capabilities, the need for separate security products may decline, especially among cost-sensitive small and mid-sized businesses. When security tools are already included with widely adopted platforms, customers may be less willing to pay for additional standalone solutions. This dynamic could make it more difficult for Huntress to differentiate its offerings or maintain pricing power, particularly as built-in options continue to improve in functionality and ease of use.
Overreliance on MSPs
Huntress’s expansion has been closely tied to its 4.3K managed service provider (MSP) partners, but this dependence also introduces risks. As private equity and strategic buyers continue acquiring MSPs, such as Revelstoke Capital’s purchase of Omega Systems and PTP’s acquisition of Stratogent and Protocol Networks in Q1 2025, consolidation could disrupt Huntress’s customer base and renewals. Additionally, major vendors like CrowdStrike and Microsoft are expanding their MSP programs with aggressive incentives, including discounts and co-selling benefits. These programs may pressure MSPs to consolidate spending on larger platforms, limiting Huntress’s ability to maintain wallet share and partner loyalty.
Summary
Huntress offers cybersecurity tools designed for small and mid-sized businesses (SMBs), particularly as hybrid work and widespread SaaS adoption introduce new security challenges. The company focuses on identity-based threats such as session hijacking, rogue OAuth apps, and business email compromise by combining account monitoring and device-level threat detection in one platform. This setup allows managed service providers (MSPs), who often oversee IT for SMBs, to manage security more efficiently.
As data privacy regulations and zero-trust requirements become more common, Huntress supports core compliance needs like multi-factor authentication and identity monitoring. However, its growth depends on balancing reliance on MSP partnerships with increased competition from large tech providers like Microsoft and Google, which are bundling similar security features into their platforms at little or no extra cost.




