Actionable Summary
One of the biggest tailwinds in tech since the early 2000’s has been the adoption of the cloud. Cloud migration has been a gradual process with most large organizations slowly transitioning their infrastructure. The COVID-19 pandemic accelerated that transition. From 2018 to 2021, public cloud revenue grew from $32 billion to over $400 billion.
Historically, one of the biggest impediments for cloud migration has been the need to laboriously overhaul enterprises' existing security and networking setup.
The last decade has seen a rapid acceleration of new workloads moving to the cloud. With the rising adoption of cloud computing, companies can build and scale their businesses faster than ever. However, the downside of the cloud’s widespread adoption is an increased attack surface due to the many types of workloads that run on the cloud compared to on-prem.
In 2021, IDC estimated that 750 million new cloud native apps would be built by 2025. Cloud workload security is now high on CISO’s priority list.
Major cloud providers like AWS and Azure operate under a shared responsibility model. Those services provide tools to help customers secure their cloud environments, but the customer is ultimately responsible for ensuring the tools are used correctly. This configuration and the best practices around it can be complex, which is why cloud misconfigurations are often the leading cause of security breaches.
This dynamic has driven a rapid increase in demand for cloud security solutions. Spending on cloud infrastructure security was estimated at ~$172 billion in 2022. Gartner estimates that over 90% of all cloud security failures will be the result of the customer’s failure to adopt a proper cloud security posture through at least 2023.
Cloud security ranked as the fastest-growing cybersecurity sector on Gartner’s cybersecurity spending forecast report, with companies like Lacework, Wiz, and Orca all seeing meaningful traction in cloud security, with Wiz reaching $100 million ARR in 18 months. Meanwhile, the major cloud providers are bundling products for cloud security, creating questions around the potential for standalone solutions.
The current cloud security landscape includes companies addressing functionality like cloud workload protection (CWPP) and cloud security posture management (CSPM). However, the current cloud security paradigm has revolved around moving the traditional security framework into the cloud (i.e. identify vulnerabilities, prioritize signals, and trigger alerts) which leads to alert fatigue.
60% of breaches came from vulnerabilities that were already known. The future of cloud security will experience a paradigm shift that aligns closely with shift-left in DevSecOps. The market will transition from security-minded development to developer-minded security as developers and security practitioners become intricately connected.
Security is shifting from a centralized structure to embedded security where developers are increasingly being asked to assume responsibility for their workloads.
Why Cloud Security?
The cybersecurity ecosystem has become increasingly fragmented over the past few years. This report is part of a series on cybersecurity from Contrary Research to unpack that complex ecosystem.
In our previous deep dives on the topic, we started with a big picture look at cybersecurity examining the broader landscape to give readers a framework for understanding the sector. Our second report covered endpoint security and its adjacent industries like security operations and SIEM platforms. We also covered emerging startups to monitor within the ecosystem. For this third report, we’re unpacking the world of cloud security that is relatively new and still very much in flux. In our forthcoming final entry in this series, we’ll break down the role of identity in a rapidly changing digital playing field.
As we’ve discussed in previous reports, cybersecurity has become a priority for executives over the past three years. Going into 2023, security continues to remain an important focus followed closely by cloud migration.
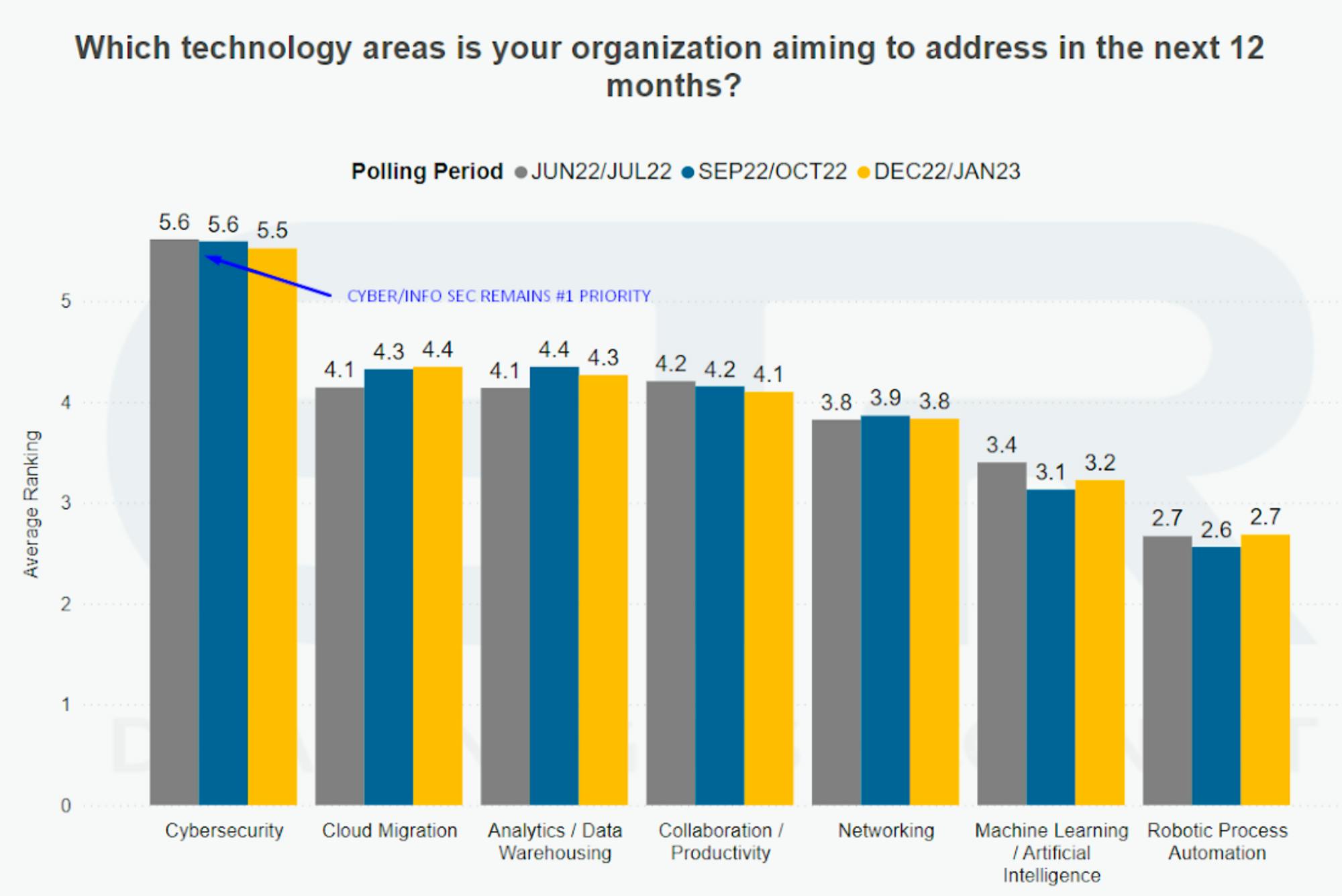
Source: ETR Research
In a recent Gartner survey, cybersecurity was the top priority for new spending, with 66% of CIOs pointing to cyber and information security as their top area for increased investment in 2023. Similarly, a recent BCG analysis indicated that, while categories like server infrastructure and ERPs are seeing reduced spend, cloud services and security infrastructure are seeing budgets increased by 26-33%.
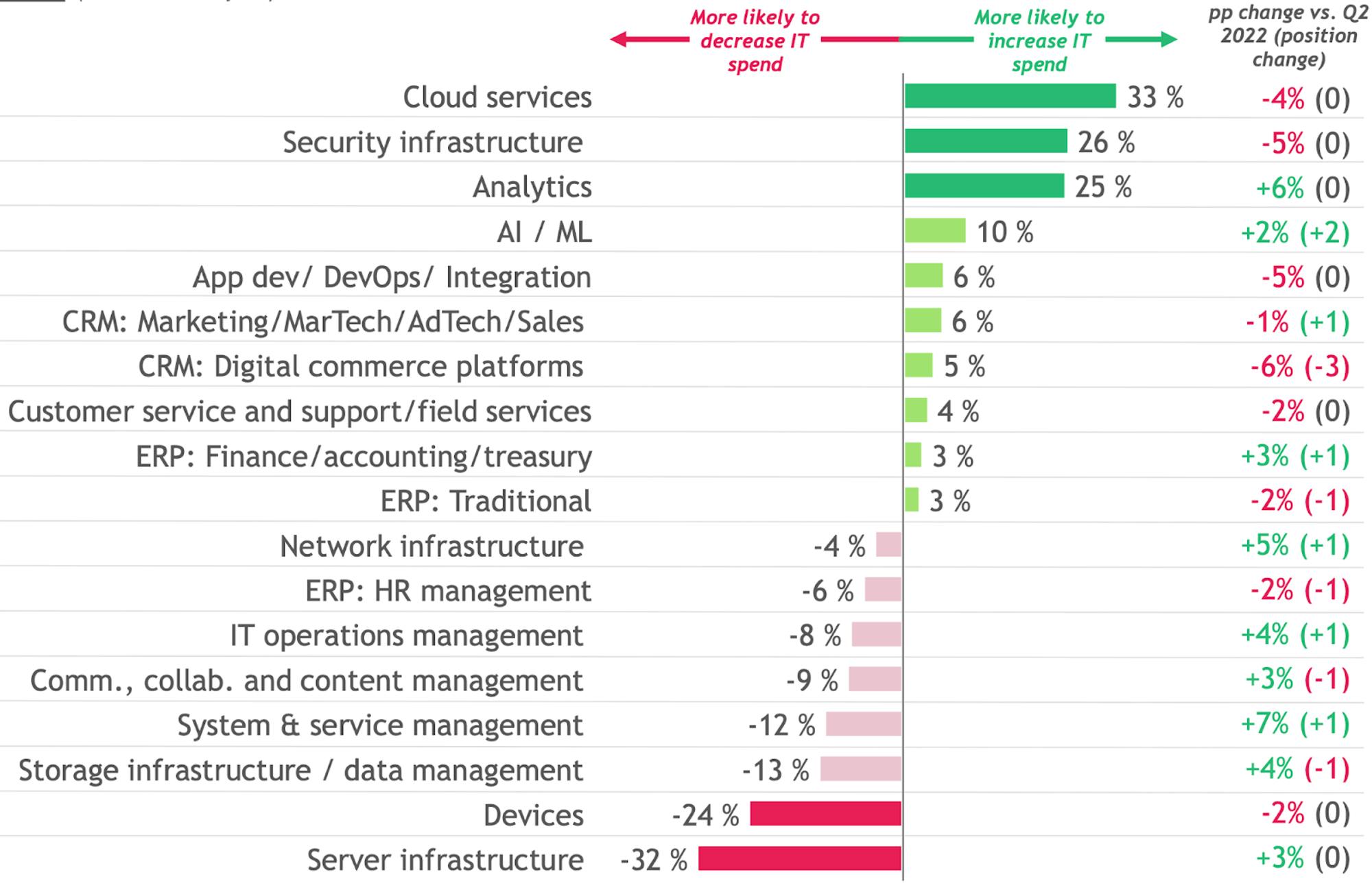
Source: BCG; Buyer Survey 5.0, December 2022
The evidence is clear that executives see their cybersecurity spend going hand-in-hand with continued investment in cloud computing. While spending on cloud computing has grown dramatically, expected to grow from $490 billion in 2022 to $592 billion in 2023 alone, cloud penetration is still in the early days. In 2021, only ~30% of new digital workloads were deployed on cloud-native platforms. That number is expected to grow to ~95% by 2025. The continued rapid adoption of the cloud has created an entirely new attack surface for companies to be concerned about.
Building Blocks of the Cloud
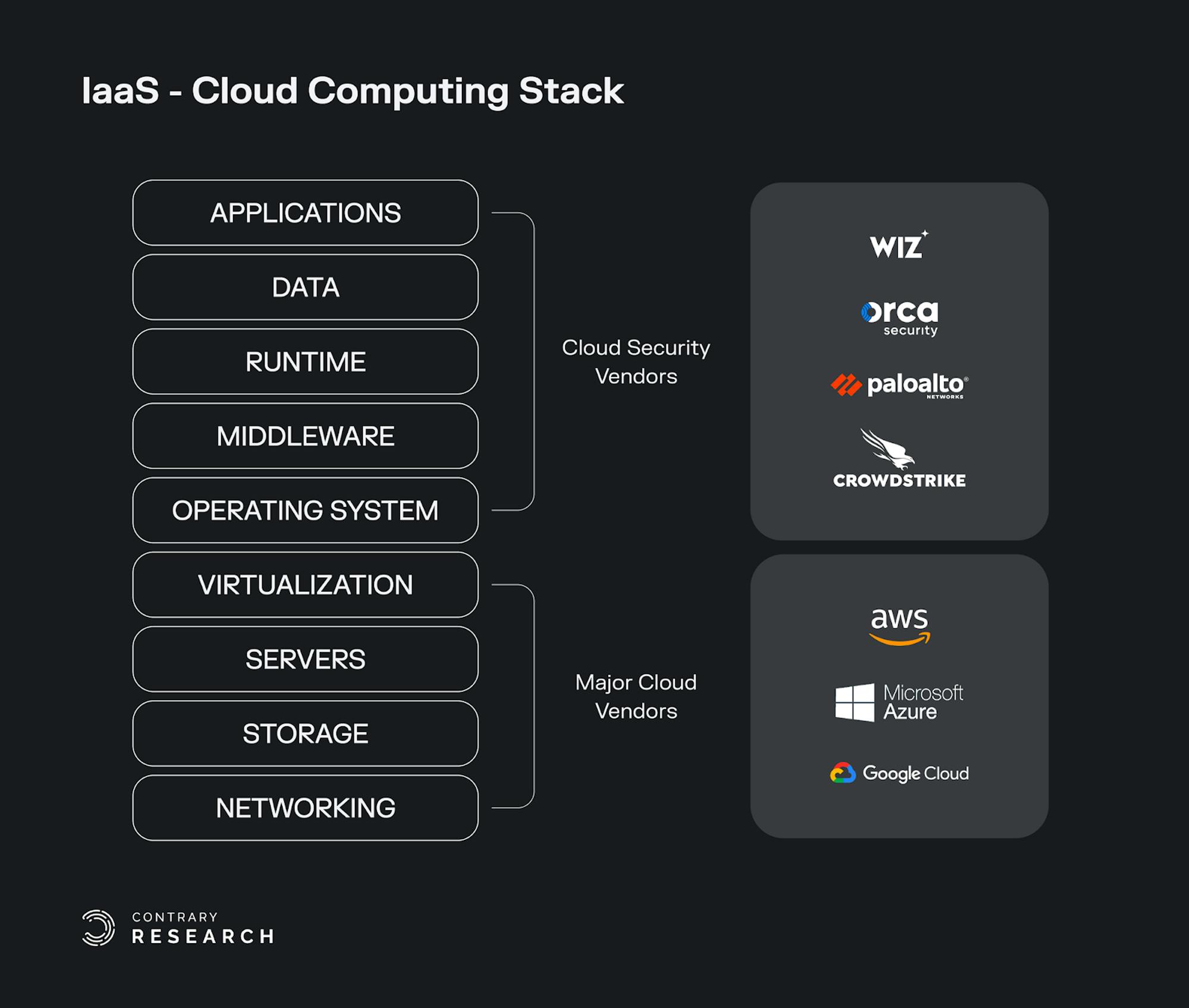
Cloud computing is about using cloud technology for delivery of on-demand computing services, from computing power to storage and applications. Responsibilities are shared between the cloud service providers and cloud service consumers:
Infrastructure-as-a-Service (IaaS) involves a method for delivering infrastructure such as servers and storage through IP-based connectivity as part of an on-demand service. Clients can avoid the need to purchase hardware and operating systems, and instead procure these resources in an outsourced, on-demand model. Popular examples of IaaS services include Amazon Web Services (AWS), Microsoft Azure, and Google Cloud (GCP). Other tools like HashiCorp Terraform are used to provision infrastructure resources from cloud providers.
Platform-as-a-Service (PaaS) is used to create software that is delivered via the internet. Examples include Application Services, Azure Search, AWS Elastic Beanstalk, and Heroku.
Software-as-a-Service (SaaS) involves the licensing of an application to customers. Licenses are typically provided through a pay-as-you-go model or on-demand. SaaS is a common offering with products such as Microsoft Office 365, Salesforce, Dropbox, and others.
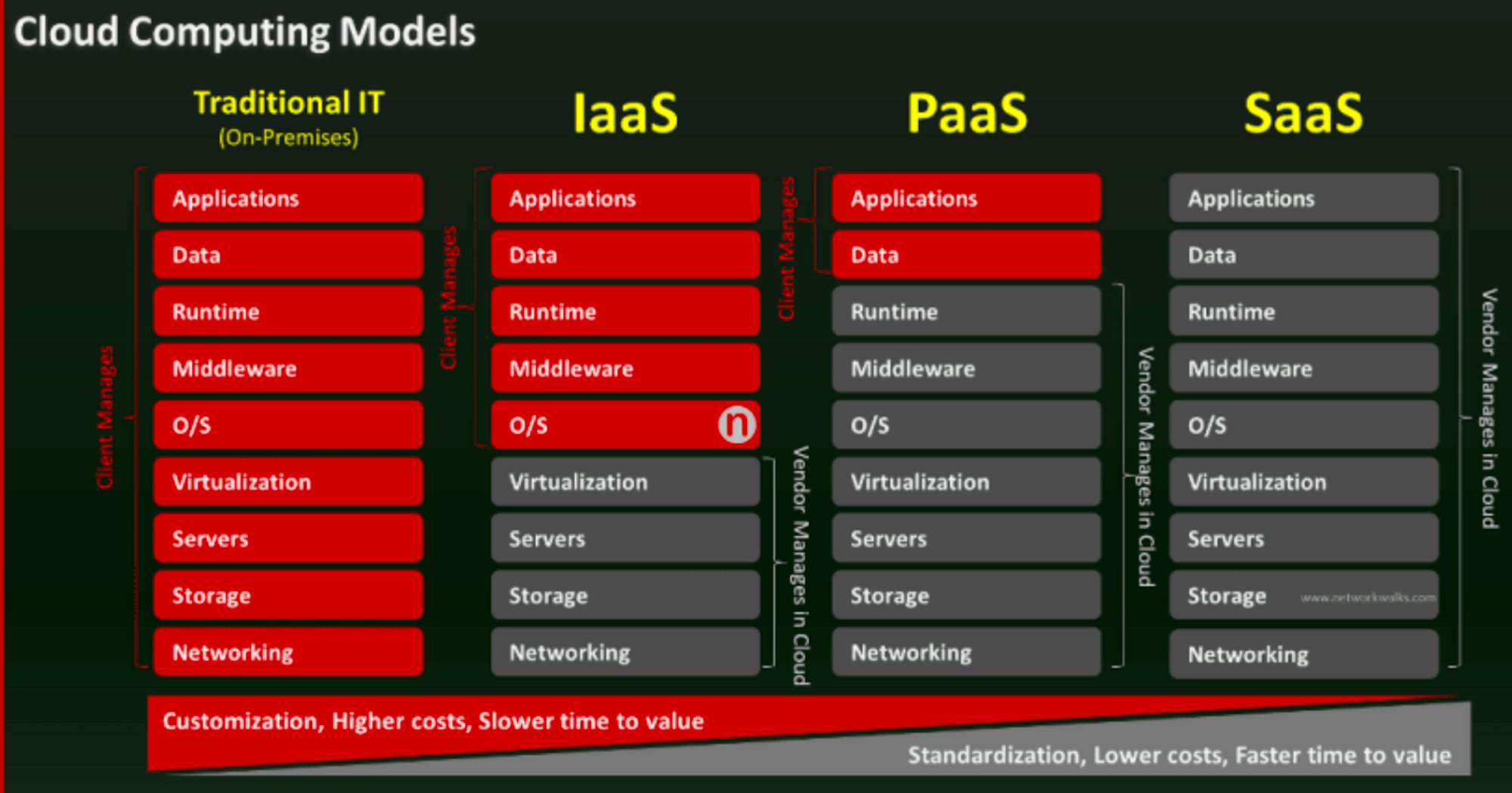
Source: Network Walks
Public cloud providers like AWS and GCP provide physical infrastructure, like servers, and then provide compute capacity as a service to a variety of different customers. When cloud providers initially emerged, security concerns arose as the result of sharing resources and losing control of data. This presented a key barrier for many organizations to adopt cloud solutions.
Over time, the IaaS providers became responsible for protecting aspects of that infrastructure including hardware, networking, and physical facilities. While IaaS providers will support certain security parameters, customers of services like AWS are ultimately responsible for ensuring the security of their environment. Most often, cloud security vendors focus on the correct configuration of IaaS services (i.e. databases missing authentication and accidentally open to the internet, or AWS services that require complex policy configuration that are often accidentally exposed.)
Unpacking Cloud Security
Cloud security vendors primarily focus on securing data, applications and workloads on public cloud computing systems. Cloud security broadly encompasses the processes, policies, and mechanisms used to protect and ensure that both the customer and cloud provider are able to mitigate cloud risks. Customers are focused on ensuring several categories of security:
Identity: Proper authentication and authorization
Applications: Ensure proper threat intelligence, and vulnerability testing
Data: Secure and encrypted
Workloads: Deep packet inspection
Network: Analysis of encrypted traffic and next-gen firewalls
Many cloud security companies have broad product platforms which allow them to address several attack surface areas. In addition, companies take different approaches to addressing cloud security. Many of the largest players in cloud security have taken a “scanning” approach. These scanning tools review cloud resources and applications looking for vulnerabilities. Others anchor more heavily to the shift-left movement by empowering developers to ship products that are more secure from the outset.

To be clear, many platforms will point to examples where their products emphasize shift-left in addition to leveraging scanning, so these are not mutually exclusive market segments. For example, Orca Security utilizes side-scanning to understand cloud workloads. However, its platform also enables security and compliance checks for developers to review for possible misconfigurations. The broader point is that some platforms are more focused on enabling developers as part of the security lifecycle, while others are still focused on traditional security operations teams.
Shared Responsibility Model
Before public cloud providers, companies were responsible for setting up their own physical servers and data centers. While this gave them full control over their own data, it also made them responsible for all their own security. The adoption of the cloud ushered in a shared responsibility model in which cloud vendors take on aspects of a customer’s security requirements, while customers work directly with cloud security vendors for additional security needs they may have.
Typically, companies will work with cloud security providers in securing applications, workloads, and data. Cloud providers are responsible for managing the security and compliance of the platform in terms of the network, container, runtime, and isolation.
The level of involvement in cloud security from cloud providers may be changing as cloud providers look to take a more active role in security. For example, at AWS re:Invent in December 2022, Amazon announced security products or services across product categories like cloud native application protection (CNAPP), identity and access management (IAM), extended detection and response (XDR), and more. Similarly, Microsoft has always been highly security conscious. In January 2023, Microsoft announced that their security business had surpassed $20 billion in revenue. The company articulated their position this way:
“We're the only company with integrated end-to-end tools spanning identity, security, compliance, device management, and privacy informed and trained on over 65 trillion signals each day. We are taking share across all major categories we serve. Customers are consolidating on our security stack in order to reduce risk, complexity and cost.”
But for now, cloud security remains a large enough pool that cloud providers, incumbent security platforms, and new-age cloud security startups are able to ride the market tailwind created by many companies’ needing to secure workloads as they move into the cloud.
Drivers of Cloud Security
Historically, security was driven by a physical network. Companies would secure their physical on-premise servers with a firewall around the company’s systems. The advantage of cloud environments is that they lack these limiting factors, especially as work-from-home and bring-your-own-device (BYOD) policies become more common. Customers, vendors, and employees can access data from anywhere around the globe. As applications become more integrated through APIs, accessibility on cloud-based applications becomes universal. To effectively establish a cloud security framework, practitioners have to be aware of a number of factors that drive cloud security risks:
Cyber breaches
Data loss
Cyber attacks and disruptions
Misconfigurations
Ubiquitous technology weaknesses
Malware
Advanced persistent threats
Insider exposures
Inadequate access management
Insufficient research
To respond to each of these disparate factors, security platforms have been built around a number of different core competencies. Each of those functionalities respond to a different set of risks in the cloud, including overall security posture, workload protection, and managing access and entitlements to different types of infrastructure.
The Bundling of the Cloud Ecosystem
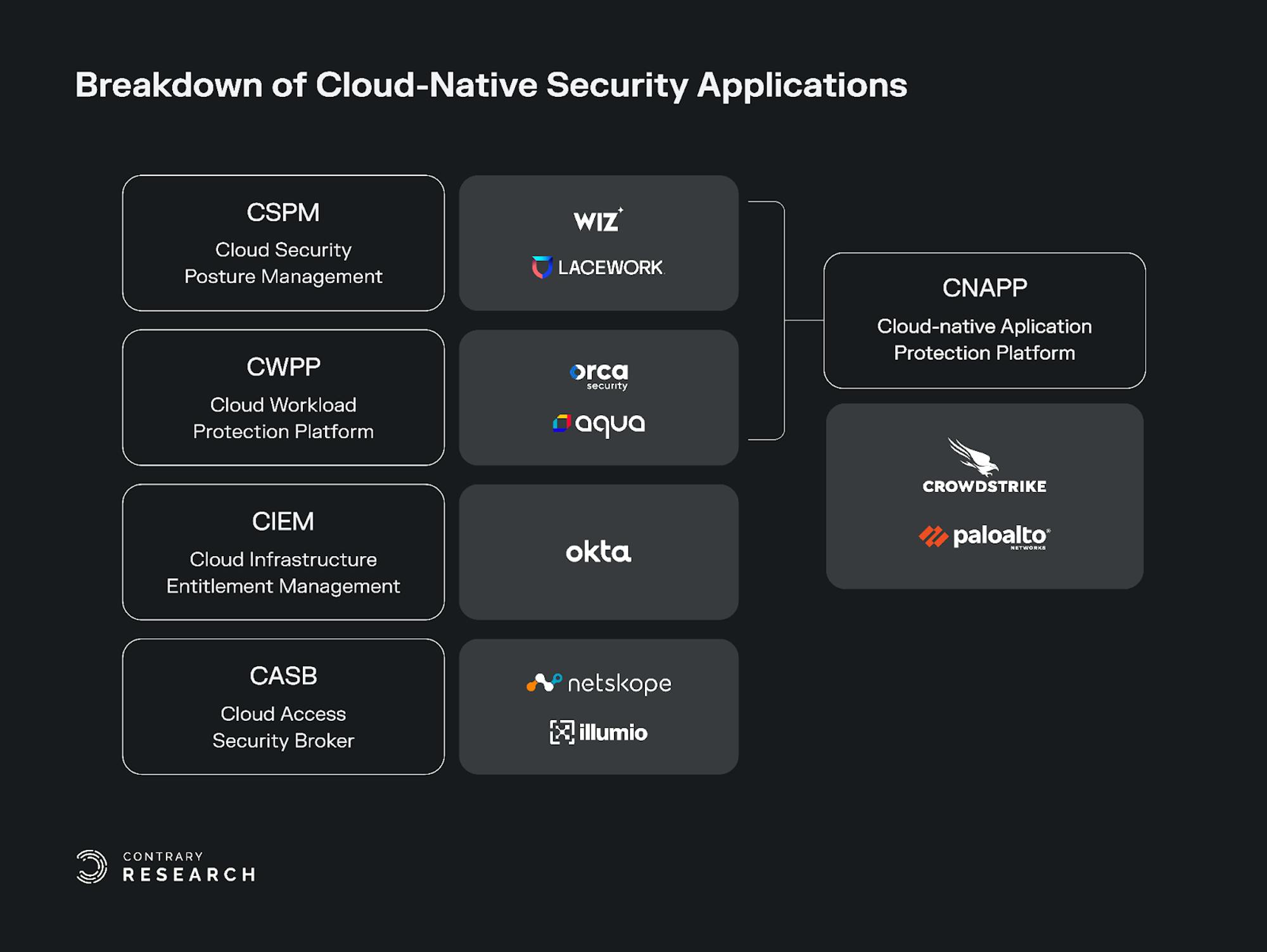
In May 2021, Gartner released a report that coined a number of categories used to describe the multi-faceted nature of the cloud. These categories help articulate different aspects of a number of cloud security vendors and the parts of the security stack that they address:
Cloud Security Posture Management (CSPM): A process to identify and remediate risk by automating visibility, uninterrupted monitoring, threat detection, and remediation workflows to search for misconfigurations across diverse cloud environments and infrastructure, including Infrastructure-as-a-Service (IaaS).
Cloud Workload Protection Platform (CWPP): Platforms that provide security tailored to the needs of workloads deployed in public, private, or hybrid cloud environments. The objective of a CWPP is to keep the applications secure, by providing security for the application and all of the associated cloud capabilities.
Cloud Native Application Protection Platform (CNAPP): A cloud-native security model that encompasses Cloud Security Posture Management (CSPM), and Cloud Workload Protection Platform (CWPP) in a single holistic platform. CNAPPs emphasize the need for enterprises to focus on cloud-native security solutions that provide a complete lifecycle approach to application security as opposed to a patchwork of tools.
Cloud Infrastructure and Entitlement Management (CIEM): The security process of managing access rights, permissions, or privileges for the identities of a single or multi-cloud environment. This process helps to identify and avoid risks resulting from privileges being higher or broader than they should be.
Cloud Access Security Broker (CASB): Cloud-based security policy enforcement points, placed between cloud service consumers and cloud service providers to combine and interject enterprise security policies as the cloud-based resources are accessed.
Below, we’ll outline these different segments and use relevant companies to illustrate these capabilities. But first, a caveat: one of the complexities of cybersecurity is the intricate overlap between different functionalities. As a result, while we may provide examples of CSPM with companies like Wiz, or examples of CWPP with companies like Orca Security, both of these companies would claim they have functionality that extends to multiple categories on the list beyond the one we think they exemplify.
Cloud Security Posture Management (CSPM)
Source: Uptycs
Cloud Security Posture Management (CSPM) is a category of cloud security platforms aimed at improving a company’s security posture, identifying misconfigurations, and ensuring compliance standards for companies in the cloud. Misconfigurations can include cases where developers have provisioned S3 buckets with incorrect settings or improperly exposed permissions, leaving them vulnerable.
For example, in October 2021, Facebook experienced an outage affecting all their platforms across 2.9 billion users. The cause of the outage was a misconfiguration. While not a breach in the sense that it wasn’t caused by a malevolent external party, outages of this type still represent a significant business continuity threat because they put a company’s systems at risk. A single misconfiguration can expose hundreds of thousands of systems or highly sensitive data to the public internet.
According to Gartner, 95% of cloud security issues will be the result of misconfiguration or user mistakes. Using a CSPM tool can reduce cloud-based security incidents due to misconfiguration by 80%. In a recent survey, 27% of organizations experienced a public cloud-related security incident in 2022, up from 10% the prior year.
The biggest problem that companies face on the cloud is a lack of visibility into their cloud assets. As a result, CSPMs focus on providing visibility and constantly conducting risk assessments of a customers' cloud infrastructure. Some estimates indicate that the number of cloud native applications will grow 4x from 2022 to 2025 to reach 750 million. That explosion of applications will require more robust management of configuration for public cloud IaaS and PaaS services.
Wiz
Wiz’s core product is Cloud Security Posture Management (CSPM), which collects metadata from clients’ cloud accounts via APIs. Wiz uses an API-based agentless deployment method and offers a variety of products including vulnerability management, container security, and cloud detection & response (CDR). Wiz’s agentless model allows the product to scan a customer’s cloud environment without the need for complex deployments that can take months, even for large teams. Within a few minutes, Wiz’s product provides an overview of the cloud environment.
As cloud environments become increasingly complex, Wiz offers a way to gain visibility and identify or correct misconfigurations that could lead to vulnerabilities. Wiz’s deployment model appeals to companies with more constraints on their technical resources, as well as compliance-heavy industries that avoid pervasive deployment methods.
Wiz’s CSPM scans and manages cloud assets including virtual machines, containers, and object storage (an architecture for unstructured data storage). It also collects management information from cloud accounts that includes firewall policies, identity entitlements, and networking settings. With these inputs, CSPM contextualizes the information and gains a comprehensive mapping into a client's cloud infrastructure. Wiz calls this feature set the Wiz Security Graph. Using this capability, CSPM can then alert clients about misconfigurations and potential compromises within the cloud environment.
Lacework
Lacework is a cloud security platform that offers security for workloads, containers, Kubernetes, and cloud accounts operating within cloud environments. Lacework’s broad cloud security platform has its roots in CWPP. It has agent-based and agentless options.
Unlike Wiz, Orca, and other peers, Lacework doesn't rely on rule-based security engines that require human experts to code and update. Instead, Lacework aims to collect data wherever possible through data agents like CWPP vendors do. With the most comprehensive input set possible, Lacework then normalizes and organizes the data into tables. Machine learning algorithms are then applied to classify anomalies from normal behaviors. This allows Lacework to deliver more adaptive security not available in static engines like those provided by Wiz.
Lacework also identifies cloud vulnerabilities and misconfiguration settings to ensure compliance with cloud best practices. For example, if an employee forgets to lock access to an AWS S3 bucket for several days, the platform is able to detect this security risk and alert SOC teams. It identifies misconfiguration issues and compliance risks across a multi-cloud environment.
Lacework’s cloud-native platform offers automated anomaly detection that provides consistent visibility, context, and security across multi-cloud environments. It provides customers with the ability to detect attack activity stemming from known and unknown threats. Lacework created their Polygraph Data Platform which uses data and machine learning to automatically identify risks, vulnerabilities, and abnormalities across the cloud environment, and then surface high-value alerts, prioritize risk, and speed up investigations.
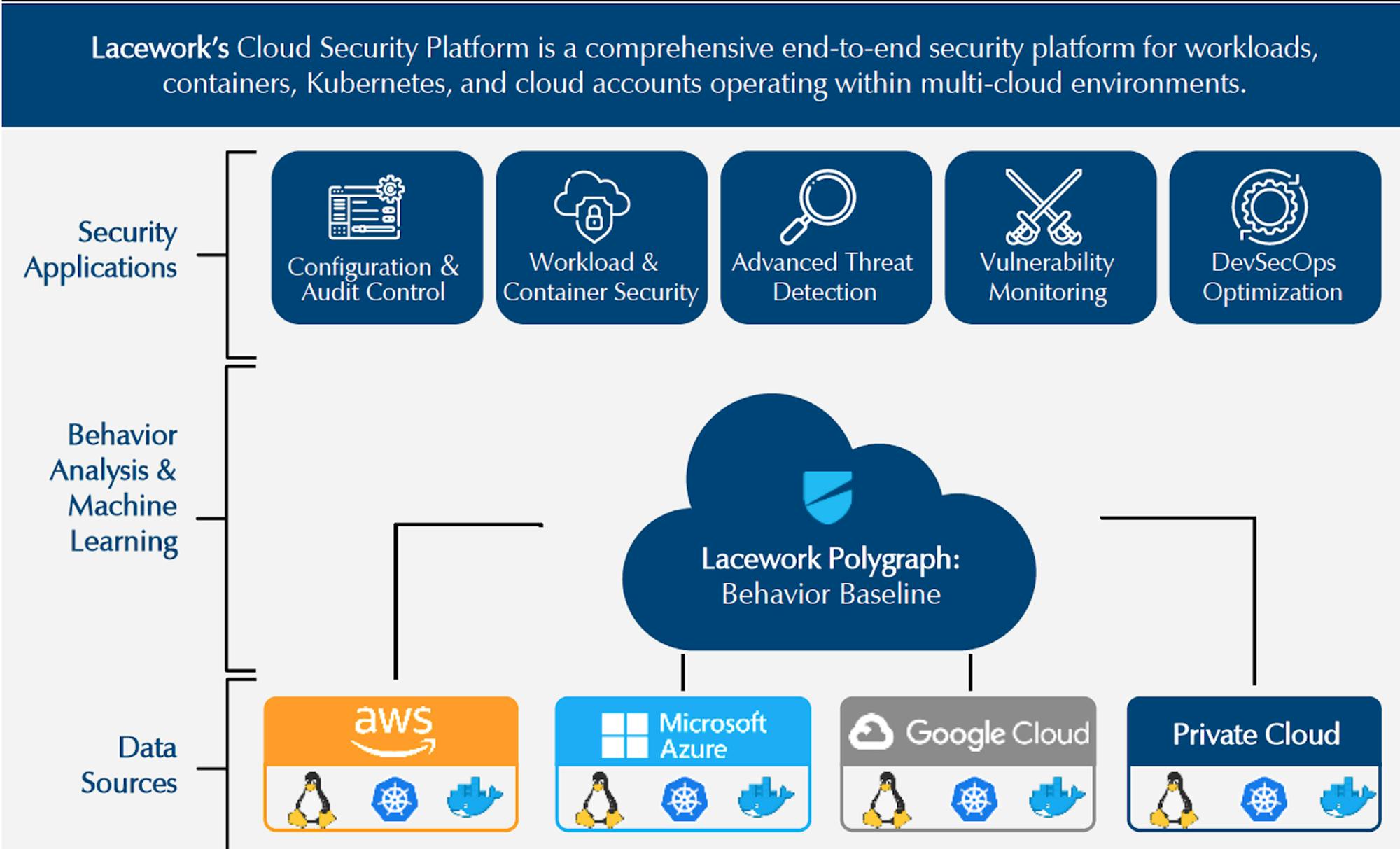
Source: Momentum Cyber
Several other companies offer CSPM platforms, including Orca Security, which offers a CSPM evaluation, and many other vendors that provide a robust CSPM Scanning capability.
Cloud Workload Protection Platform (CWPP)
Cloud Workload Protection Platforms (CWPP) are security solutions that monitor, protect, and eliminate threats on cloud workloads such as virtual servers, containers, and infrastructure. There are two key objectives in cloud workload protection: (1) visibility, and (2) protection.
One of the many challenges that companies face is a lack of visibility on what is happening in their cloud environments. Companies can’t detect, stop, or respond to something if they can’t see it. Workload events need to be captured, analyzed, and stored so that security products and services teams alike have the visibility to detect and stop threats as they happen.
CWPP platforms can also automate security responses to suspicious activity. Most CWPP platforms support continuous integration and continuous delivery (CI/CD) workflows, which allow the protection of particular workloads to occur as quickly as developers can deploy containers or applications.
There are four core pieces of technology in CWPP:
Containers: Containers are key elements of cloud security. Containers have evolved as quick ways to rapidly build and deploy applications on the cloud. Some of the key risks associated with containers include unsecured images, risky container hosts, registries, and orchestration platforms like Kubernetes.
Serverless Platforms: As on-prem has moved to cloud, firewalls have become less relevant. Serverless applications consist of distributed cloud services working together, such as an S3 bucket which triggers a Lambda Function, which in turn triggers DynamoDB. In this architecture, the focus of security is around permissions, code analysis, and behavioral analysis.
Microservices: Within an application developers can use microservices as small, independent services that are part of the broader application. Each of these services communicate with each other using simple APIs. Despite the critical role that microservices play in cloud workloads, there is no universal way to secure microservices, and applications that use them are instead dependent on the broader security infrastructure.
Infrastructure-as-Code (IAC): IAC allows developers to more easily provision different types of cloud infrastructure. Tools like Terraform by HashiCorp are used to simplify this process, however misconfigurations within the infrastructure-as-code are common.
Orca
Orca Security provides an agentless CWPP that heavily leverages the cloud provider’s APIs. The company’s product leverages side-scanning technology that is able to simultaneously gain deep insights into cloud workloads and relevant metadata. Orca’s product doesn’t require an agent, instead creating a 1:1 replica of the cloud workload environment to provide greater context for risk alerts.
Orca’s solution runs in parallel with the production environment, and therefore helps speed up the software development and deployment process. Orca also has native SIEM-like remediation and response tools typically found in third-party solutions. With deep integration into these SecOps features, Orca could also help automate and speed up the broader DevSecOps cycle.
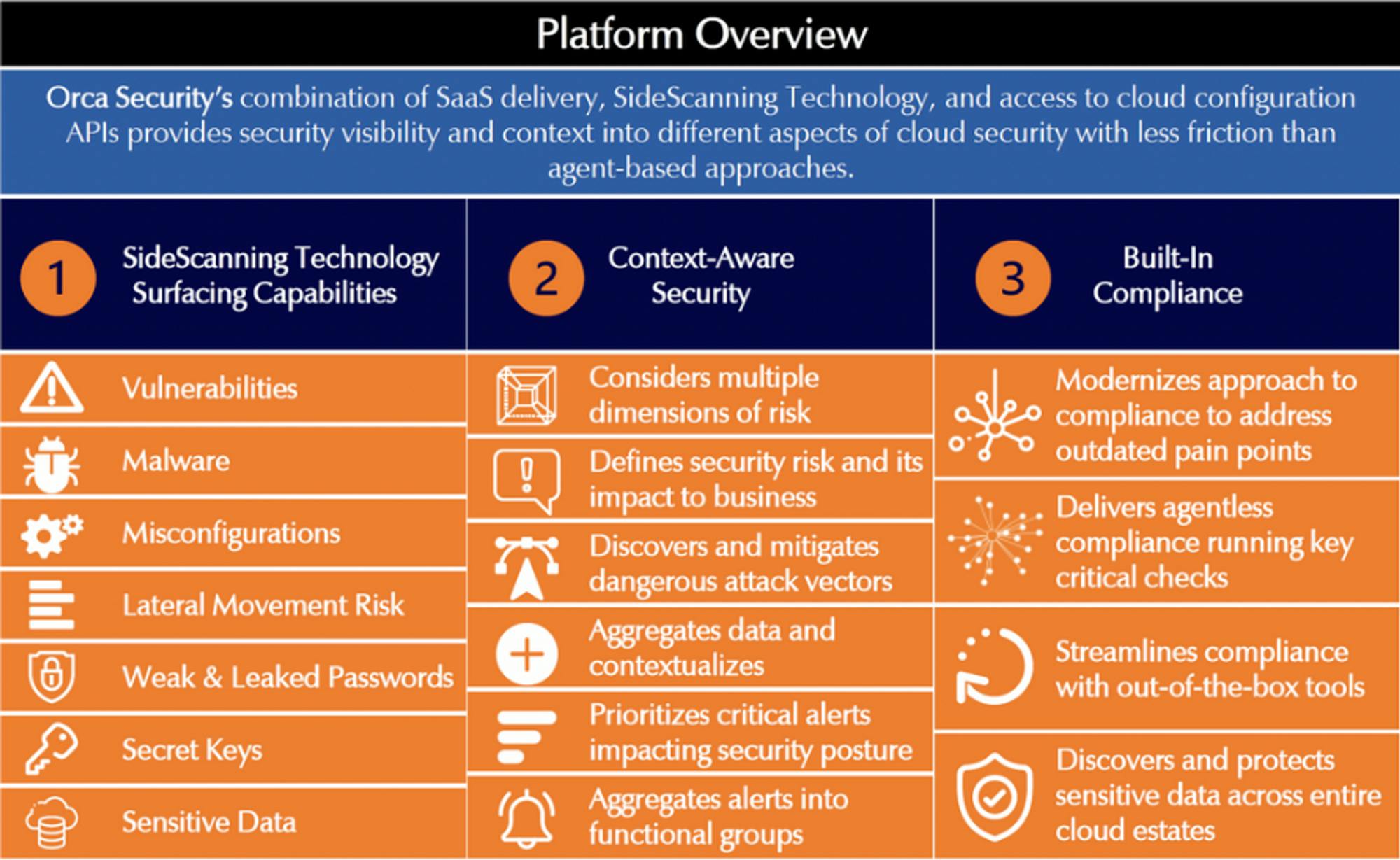
Source: Momentum Cyber
Aqua
CWPPs primarily protect server workloads at runtime with installed agents that can detect threats (malware, suspicious lateral movement, fileless attacks, etc.). CWPPs detect and respond to anomalous behavior and identify vulnerabilities across containers, VMs, and microservices. Given the prevalence of containers, container security has become an integral part of any CWPP.
Aqua is a cloud security platform well-known for its container security features. It was one of the earliest standalone platforms to provide container scanning that could scan container images for vulnerabilities. These include scanning images in repositories and images integrated into the CI/CD pipeline.
Source: Kuppingercole Analysts
Aqua started as a vulnerability scanning tool for container images, but quickly became specialized in Kubernetes, which is the orchestration platform for managing containers. Aqua has an agentless sandboxing method for scanning and running containers before they are ready for production called Dynamic Threat Analysis (DTA). Due to its architecture, Aqua also has advantages in static container image scanning. However, static container space is becoming increasingly competitive and undifferentiated.
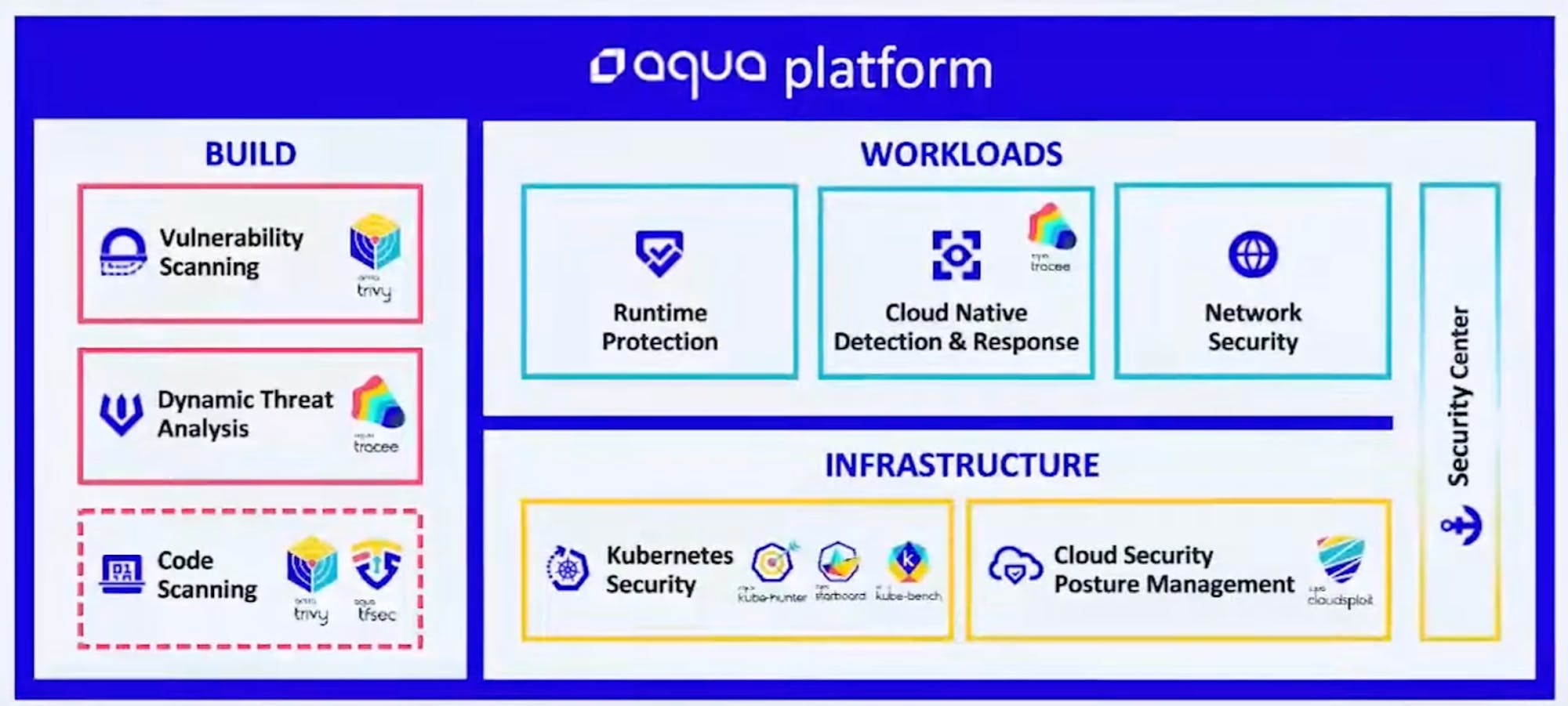
Source: Aqua Security at RSA Conference
Cloud Native Application Protection Platform (CNAPP)
Cloud-Native Application Protection Platforms (CNAPP) are a category of security platform that encapsulates Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) products. CNAPP represents the convergence of security technology that protects cloud workloads and helps mitigate misconfigurations in the cloud. Since CNAPP encompasses all the key elements of cloud security, the largest players are typically more established multi-product platforms.
Palo Alto Networks
Palo Alto Networks has one of the most comprehensive cloud security products. A large portion of their platform functionality has come from a series of acquisitions including Twistlock (container security), Evident.io, Bridgecrew (Infrastructure-as-Code), Cider Security, Aporeto, and PureSec (serverless and vulnerability management).
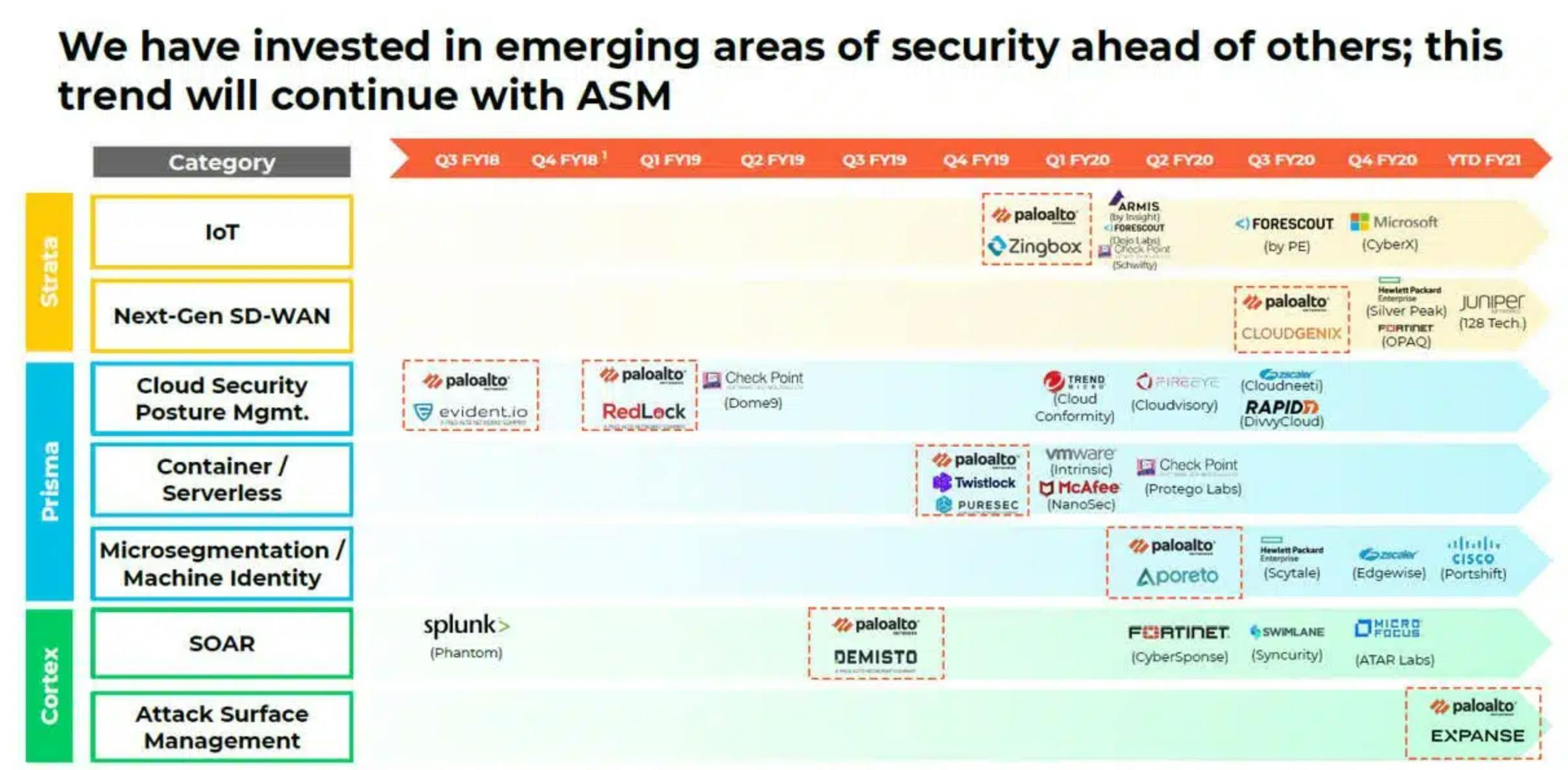
Source: Nosible
Palo Alto Networks refers to the broad umbrella of its cloud security portfolio as Prisma Cloud. According to Palo Alto Networks’ Q4 2022 Earnings Call, Prisma Cloud now has 9 core modules that extend from development to deployment to production.
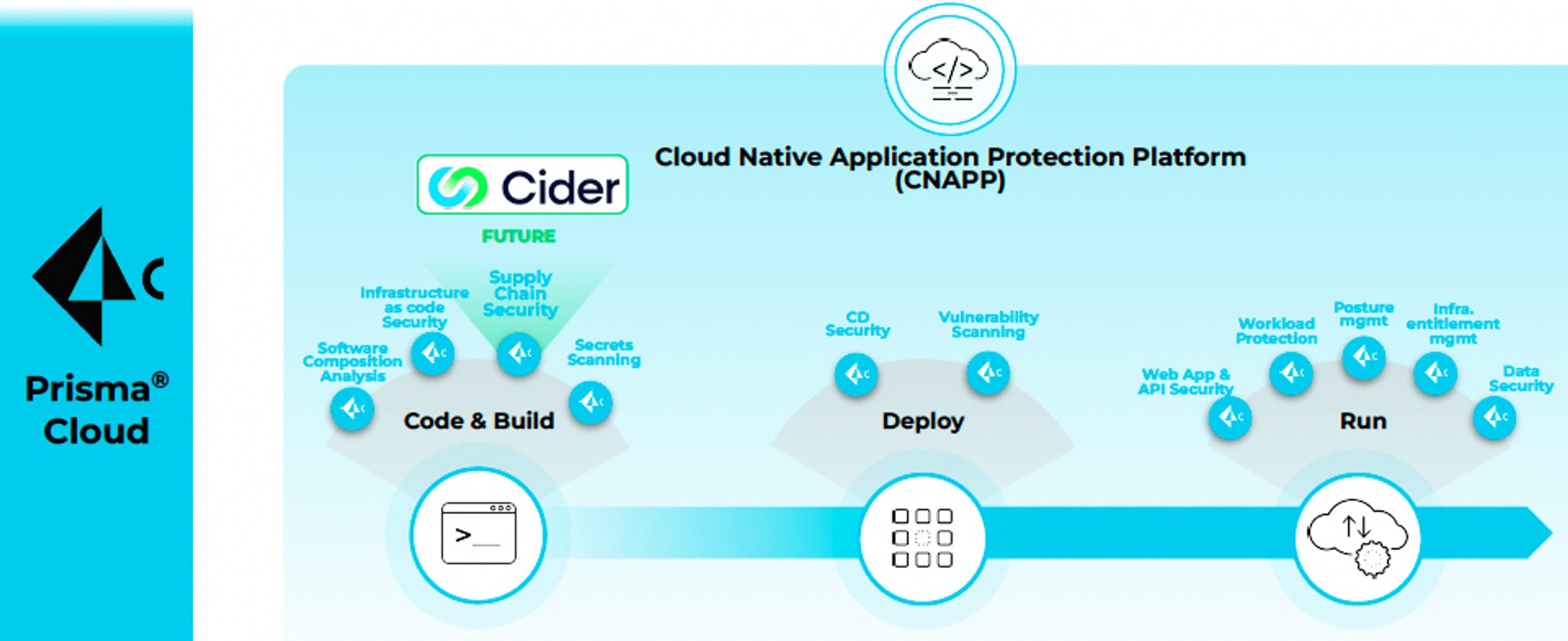
Source: Palo Alto Networks
Crowdstrike
Crowdstrike has emerged as one of the major platform companies in cybersecurity. Crowdstrike expanded into cloud workload protection and Falcon Container Security from endpoint security primarily due to the agent solutions that come with its platform. CrowdStrike’s cloud-native platform provides visibility and protection capabilities to all workloads across data centers and platforms. With Crowdstrike, the same agent protects the host as well as any running containers.
Crowdstrike provides Falcon Cloud security for AWS, Azure, and GCP. Its Platform provides vulnerability scanning, multi-cloud workload discovery, CI/CD pipeline, container security and runtime protection, MDR for the cloud, and DevOps security.
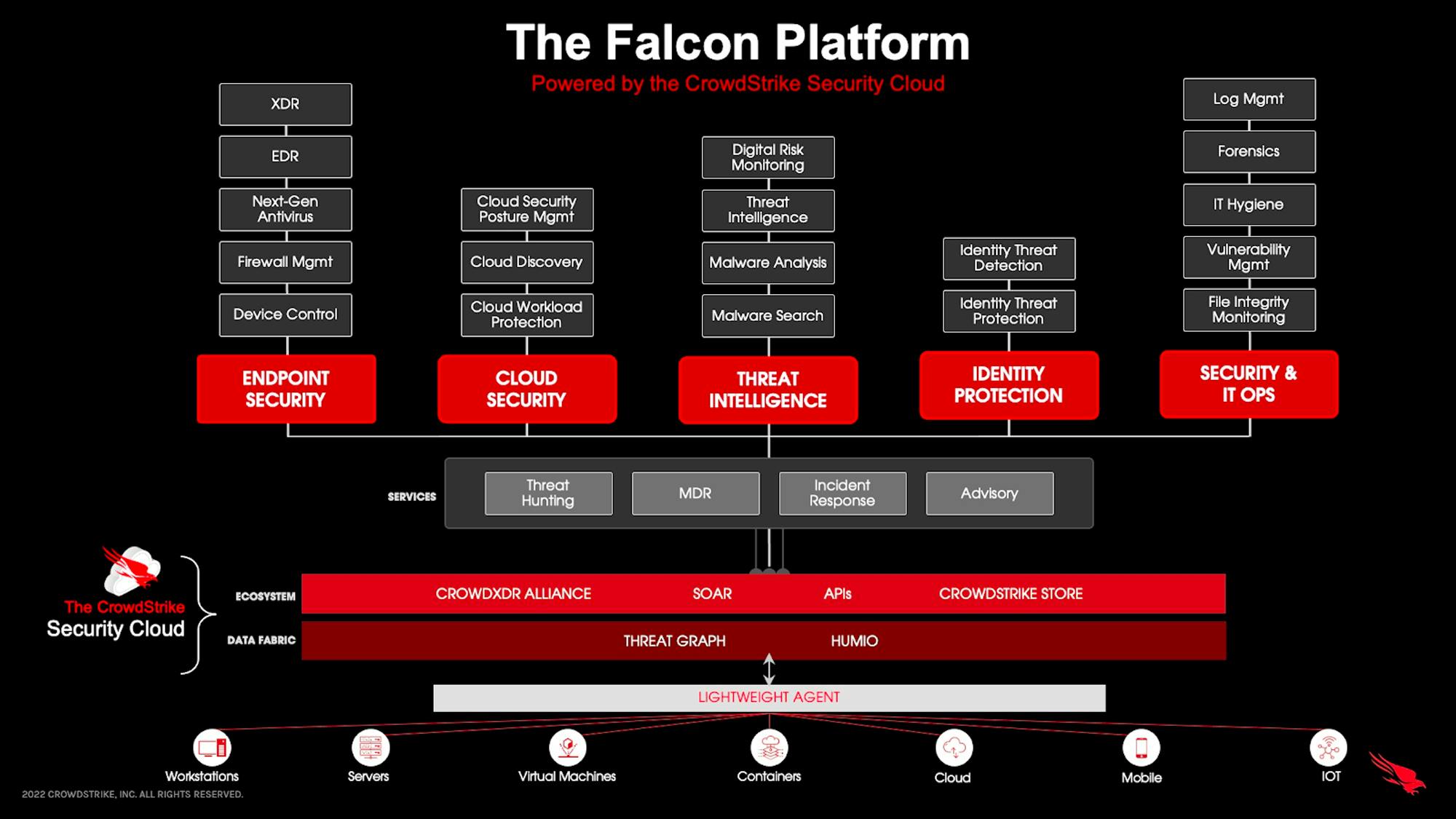
Source: Crowdstrike
Datadog
While Palo Alto Networks and Crowdstrike were already security incumbents that expanded into cloud security, Datadog is unique in that its initial product was focused on observability and application performance monitoring (APM). The positioning that Datadog’s product has within data flows from a given product enabled the company to position itself as a central platform for cloud security.
Muji at Hhhypergrowth describes Datadog’s positioning this way:
“Datadog has what I like to call ‘beachfront access’ to the underlying infrastructure, as their Datadog Agent is installed directly onto host systems. Datadog already has all the observability data across the apps, the app stack, and the infrastructure. It already has ML capabilities in Watchdog that are looking for anomalies. It is no surprise that they eventually transitioned all of this into security.”
While Datadog’s core cloud security platform has been built around CSPM, the company’s additional modules around security monitoring, runtime security, and threat intelligence enable Datadog to expand into CWPP more broadly.
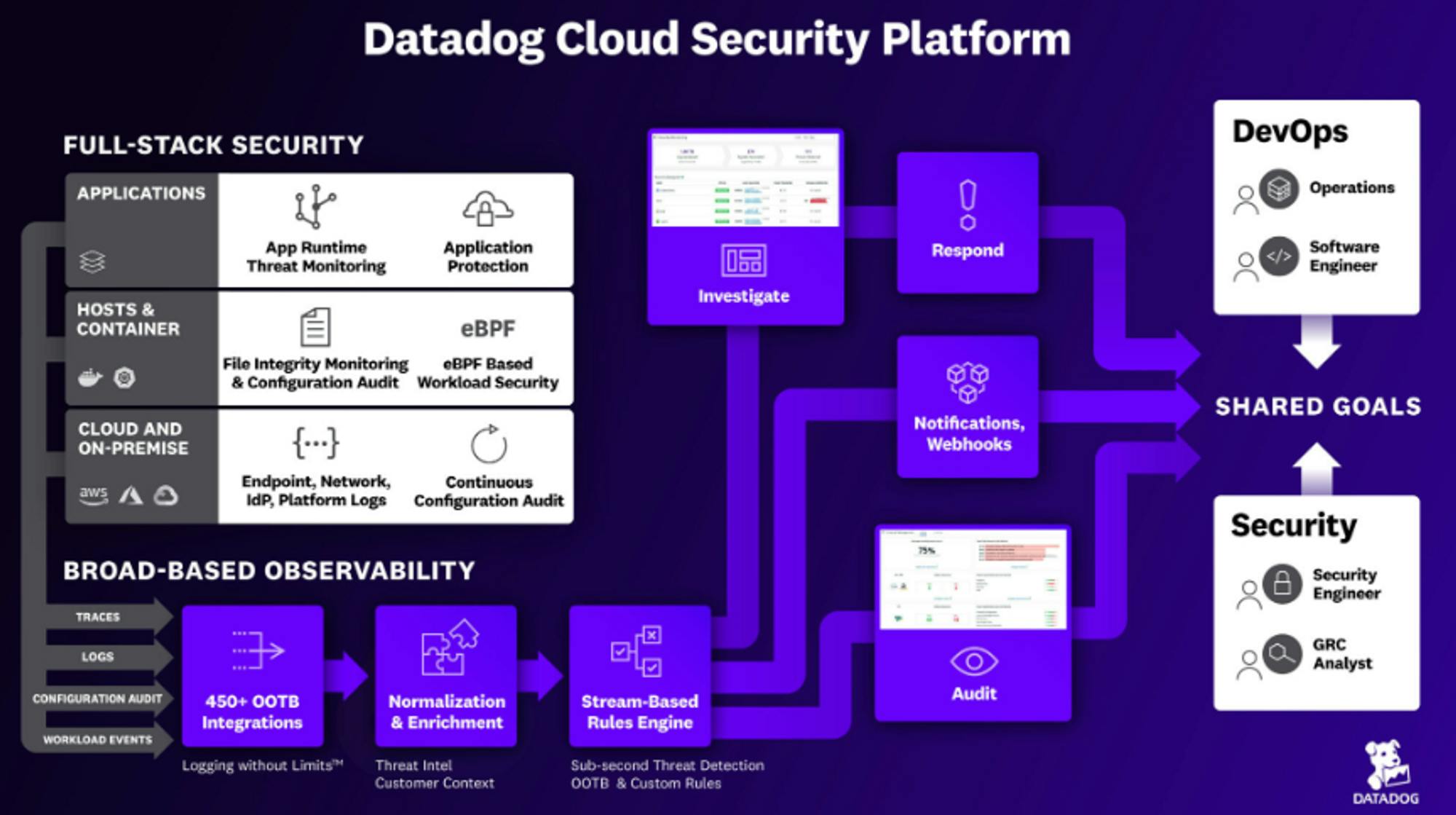
Source: Datadog
Cloud Infrastructure and Entitlement Management (CIEM)
Cloud Infrastructure and Entitlement Management (CIEM) solutions automate the detection, analysis, and mitigation of cloud infrastructure access risks to help organizations meet evolving protection requirements for cloud-native applications across virtual machines, containers, and serverless workloads.
One estimate indicates that 75% of cloud security failures are due to inadequate identity and privilege management. Traditional identity and access management (IAM) solutions are not designed to protect and control access to the rapidly changing dynamics of the cloud. CIEM addresses these challenges by improving visibility, detecting potential access risks, and remediating IAM misconfigurations. Most CIEM solutions provide a centralized dashboard to track and control access permissions to resources, services, and administrative accounts scattered across public clouds.
Okta
Okta was founded in 2009 and has since grown into a market leader in the broader identity and access management market (IAM). CIEM solutions are effectively cloud-based components of IAM including identity rule, compliance documentation, user behavior analytics (UBA), and security policies. While Okta has started to manage several of these features, dedicated cloud security vendors with CIEM solutions increasingly sit in the middle between managing entitlements and facilitating access through cloud providers.
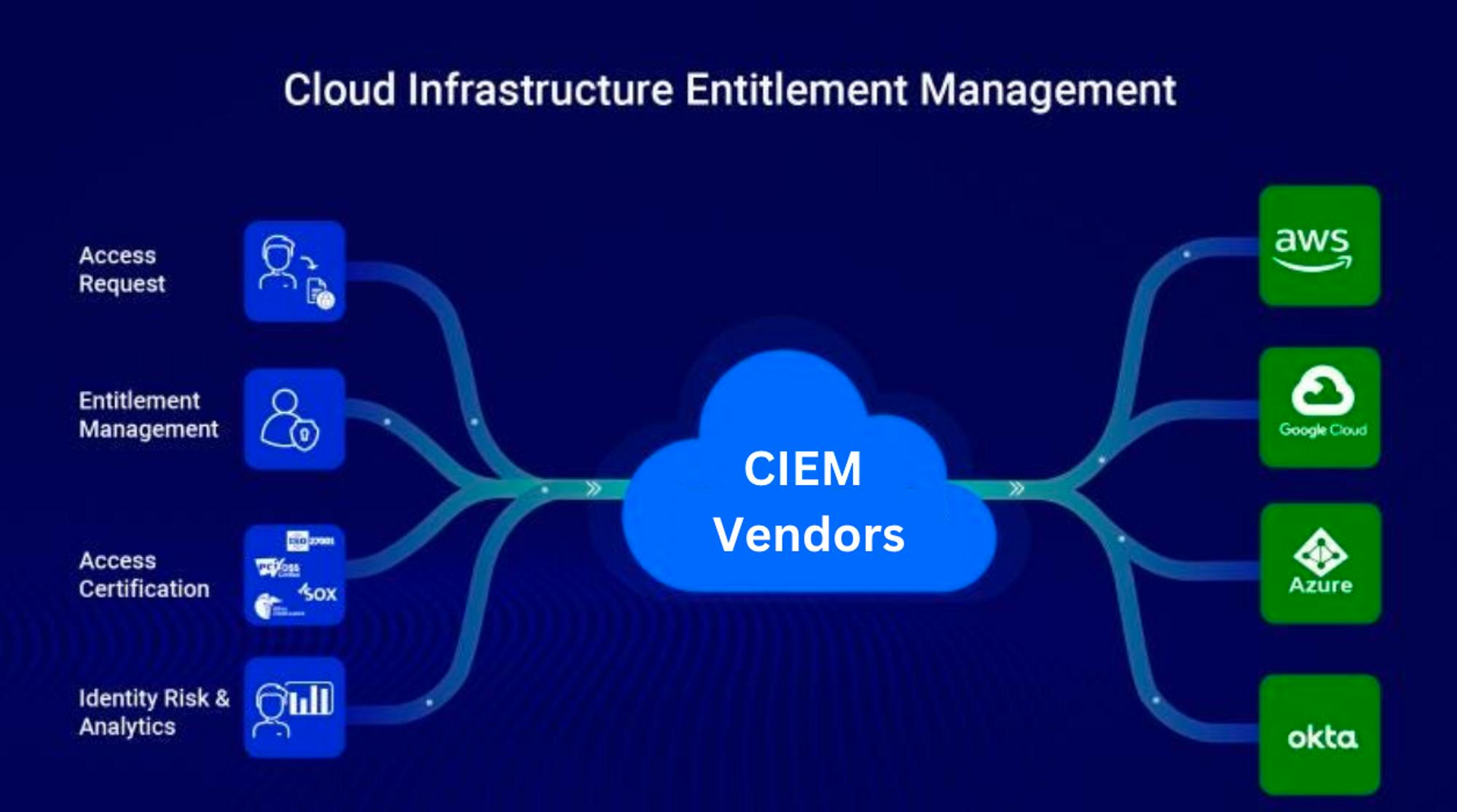
Source: SecurEnds
Companies like Palo Alto Networks, Zscaler, Saviynt, CyberArk, and SecurEnds are typically offering more dedicated CIEM solutions. In the fourth and final report in our cybersecurity series, we plan to go deeper into the identity ecosystem, and its implications for the future of security. Be sure to subscribe to get our latest reports in your inbox.
Cloud Access Security Broker (CASB)
CASB is a cloud-based security layer to enforce compliance policies between cloud resources and would-be users. As cloud computing has become more pervasive, the ability to effectively police a given network behind a firewall has become effectively impossible. Companies of all sizes have to adopt new ways of managing potential threats from internal users.
CASB is effectively a gatekeeper enabling IT teams to understand any software or infrastructure that employees might have access to. These platforms can also help prevent employees from using unapproved SaaS applications (i.e. shadow IT). Any access point to corporate systems will go through the CASB platform to ensure proper visibility and compliance.
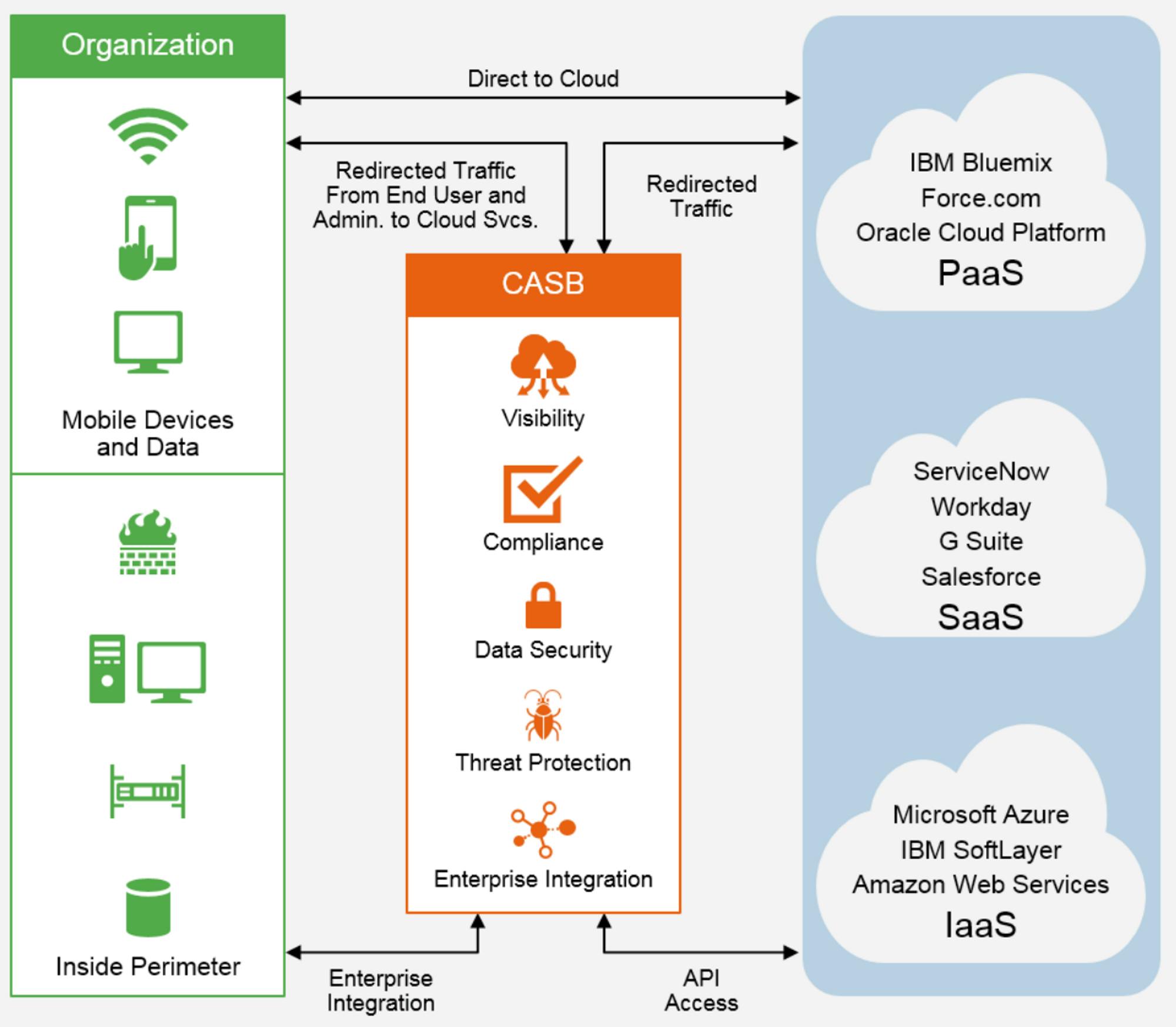
Source: Gartner
The rise of remote work and BYOD policies have increased the volume of access into corporate networks coming from devices outside an established company network. To respond to these trends, secure access service edge (SASE) policies have become more common. Some estimates indicate that by 2025, 80% of organizations will apply SASE architecture that “apply secure access no matter where their users, applications or devices are located.”
CASB products help organizations adopt zero-trust policies that sit between users and vendors to ensure cloud application and infrastructure access follows established parameters. These zero-trust networks ensure that every identity or resource access an organization’s network is property vetted, regardless of what they’re accessing.
Historically, companies deployed branch router appliances that connected their branch offices to centralized data centers. However, these legacy devices are being phased out and replaced with Software-Defined Wide Area Network (SD-WAN) products that connect remote users and branches to cloud applications and other enterprise locations by routing traffic directly to the cloud instead of first backhauling it to the data centers. SASE is the combination of SD-WAN with network security functions into a single, cloud-delivered platform.
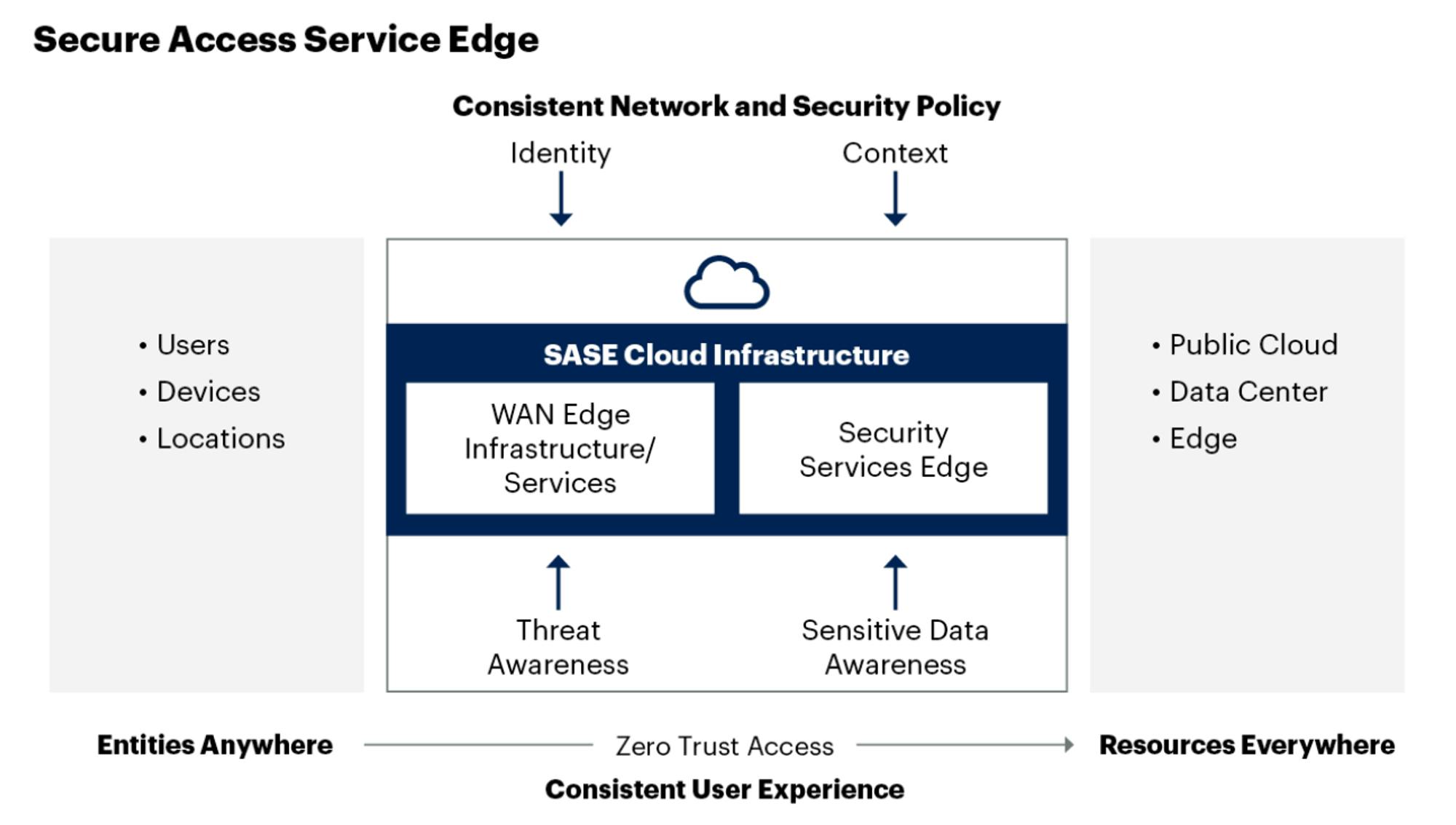
Source: Gartner
Netskope
Netskope is a network security platform that offers secure remote access, cloud-hosted application protection, and secure internet access solutions based on zero-trust principles. Netskope is riding the tailwinds from the rise of remote and hybrid work, cloud adoption, and the increasing overlap between networking and network security.
Netskope offers a number of products as part of its SASE and security service edge (SSE) platform including CASB, next-gen secure web gateway (SWG), Firewall-as-a-Service (FWaaS), and zero-trust network access (ZTNA). Netskope’s CASB solution resides between users and cloud applications like Microsoft 365, G-Suite, and Salesforce, as well as public cloud platforms such as AWS, Azure, and GCP.
Netskope also offers a database known as the Cloud Confidence Index (CCI) with 54K+ third-party cloud applications. Organizations use the CCI score to determine the threat levels present in SaaS apps and set the appropriate policies to mitigate the threats.
Illumio
Illumio has emerged as a leading platform for zero-trust and network segmentation security. As ransomware and cyber hacks continue to increase, companies need platforms to protect them. Illumio is a cloud-based platform offering data center security for workloads. The product protects an organization's network by segmenting several networks in order to prevent hacks. That way, any hackers that gain access to one aspect of a company’s network won’t immediately be able to gain access to other aspects of the same network.
The Paradigm Shift In Cloud Security
The Status Quo
Traditional on-prem security relied heavily on network access and firewalls. Security practitioners focused more on ensuring security at entry points, but had limited visibility on what was going on within their network. Today, less than 1% of organizations have visibility for at least 95% of their assets. That lack of visibility has meant that any attempts at policing access, behavior, or vulnerabilities requires significant manual work.
As a result, cybersecurity tools adopted a common framework for assessing an organization’s attack surface area. The threat intelligence lifecycle revolved around core activities like gathering data, prioritizing potential high risks or possible vulnerabilities, and creating alerts.
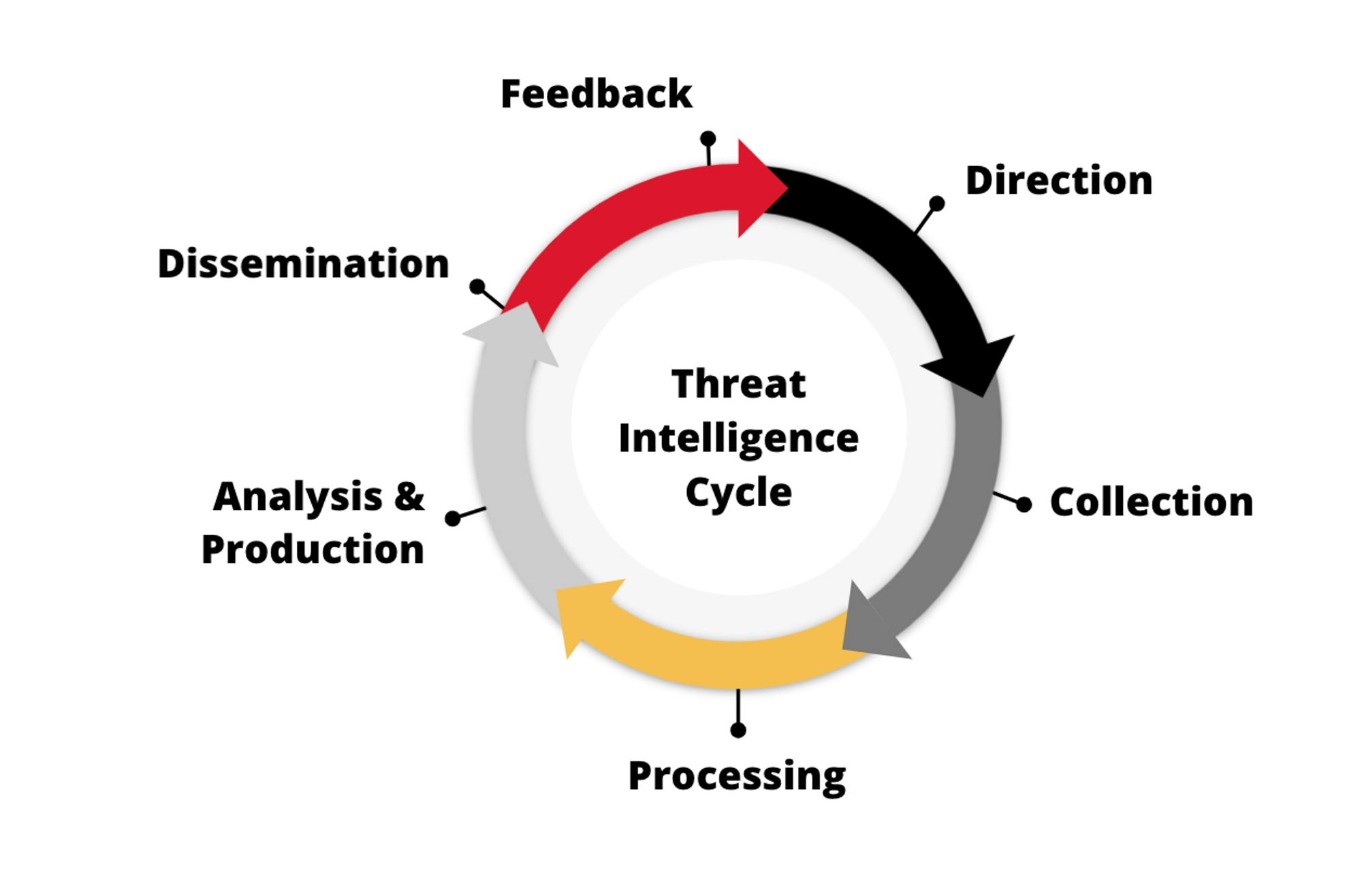
Source: ZeroFox
Because the cycle begins again after “feedback,” the entire framework has relied heavily on alerts. Whether in securing endpoints or otherwise, much of cybersecurity revolves around creating alerts (flags of possible vulnerabilities), and having security, operations, and engineering teams address them in systems like Splunk, or other SIEM platforms.
This focus on alerts has created “alert fatigue” where security teams receive 500+ alerts per day on average, with ~27-30% of them going completely unaddressed. In cybersecurity, there is a frequently-cited vision of a solution being able to provide a “single pane of glass” that would include all the alerts and context necessary to address any problems within an organization's security infrastructure. That vision has historically been a myth.
The Incremental Cloud Security Revolution
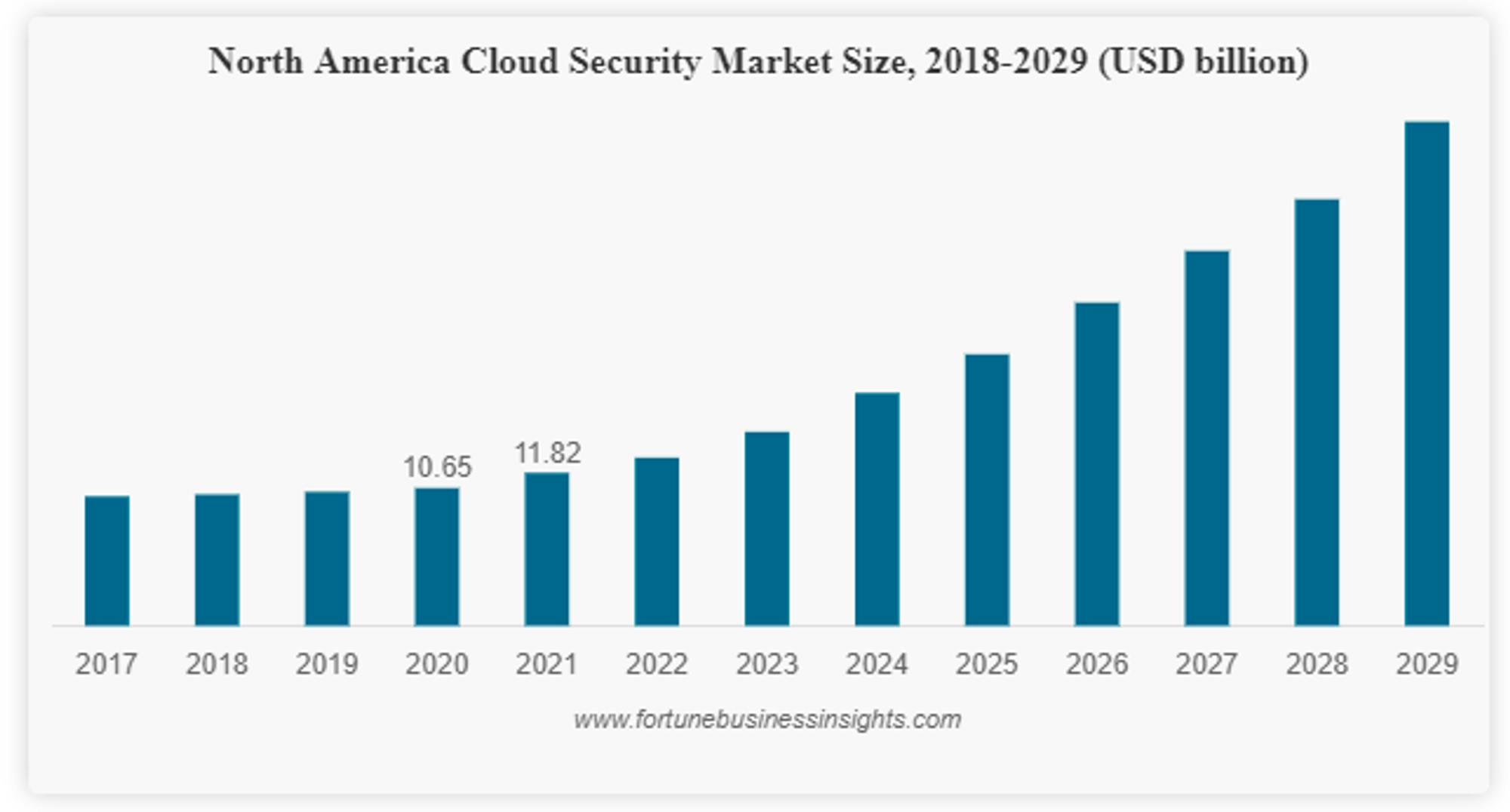
Source: Fortune Business Insights
The rise of cloud security started to meaningfully inflect in 2020, in part driven by the COVID pandemic and the increased shift to the cloud. While the cloud security market only grew ~11% from 2020 to 2021, it is expected to grow at an ~18% CAGR to over $100 billion by 2029. So how does cloud security compare to the status quo in security more broadly?
For one, the transition to cloud security has enabled more visibility, whereas historically it was all about access (e.g. who is accessing my network?). Cloud security provides more visibility into all of an organization’s assets (infrastructure, hardware, etc.). AWS, Azure, and other cloud providers have a better record of which resources have been created, and a user can query against those asset inventory lists.
Before cloud security became a large enough standalone category to attract new startups, larger organizations built internal tools like Netflix’s Security Monkey: an “open source solution for monitoring and analyzing the security of Amazon Web Services configurations.” However, these products required significant customization and still resulted in an overwhelming volume of alerts.
Companies like Wiz, Orca, Lacework, and others arose to provide a more managed solution than an open source tool, and in doing so provided more context than has historically been easy to access. By using CSPM and CWPP, users have a better understanding of their virtual machines, containers, internet-facing connections, and all the vulnerabilities that go with it.
However, at the end of the day, a security team’s primary responsibilities are to both report and remediate risk. While the existing solutions in cloud security attempt to both report and remediate around risk, they typically stop at a well-informed, albeit still overwhelming, list of alerts. That leaves much of the remediation undone.
Again, companies turned to internal tools that they could open source and hope to tackle the problem. Products like MurderBot from Riot Games or Cloud Custodian were created to respond to flagged vulnerabilities in cloud resources, but often their response was to shut down the offending resources leading to product outages.
The Paradigm Shifts Left
Developers are becoming a critical part of the security landscape. The combination of developers and security have driven the rise of DevSecOps as a category. As we wrote about in our report on The Evolution of DevOps:
“DevSecOps is becoming a major trend in the DevOps space. Another common way to articulate the trend is shift-left. If you imagine the development lifecycle laid out in a path from left to right, the status quo would put security towards the far right of the workflow – something to be reviewed right before deployment. Shift-left is the realignment of security to be an earlier part of the development lifecycle. As the pace of software development continues to accelerate, the ability for security operations teams to catch every code-level vulnerability gets much more difficult. Some sources indicate that 67% of developers have shipped code with vulnerabilities, and 84% of code bases contain one or more open source vulnerabilities. Shift-left, along with the increased emphasis on involving developers in the security process, makes the security review process more proactive, as opposed to reactive.”
Particularly in cloud security, developers are on the front lines. Developers need resources to begin any cloud-native development. They manually provision servers, databases, networks, storage, and more. There are tools that can expedite the process, like Terraform by HashiCorp, but at the end of the day security vulnerabilities are going to show up more and more in a developer’s workflow.
The best security teams recognize that developers do not have a security-first mindset and instead have to work to reduce as much friction as possible for developers to ensure their output is secure. At Netflix, the security team created “paved roads” that enabled developers to be security-minded while still being self-serve:
“The goal of the [security] automation squad is to provide consistent, actionable, self-service security guidance to developers. We aim to have a single view for developers for all actions needed to keep their applications healthy from a security standpoint. Netflix engineering invests in the concept of an Infrastructure and Security Paved Road. This provides well-integrated, secure by default central platforms to engineers at Netflix so they can focus on delivering their core business value.”
One example of a paved road at Netflix is Lemur, an open source provisioning tool for developers to get what they need, with the goal of making it so easy for developers that they choose to use the tool and get a certificate with good security parameters. Another example of this is Netflix’s API Wall (aka Wall-E), an authentication proxy that has a secure framework including everything developers need to build authentication into a new application.
The result of shift-left is that security teams need to build systems and leverage tools that enable developers to be as security-conscious as possible with as little friction as possible. Companies like Snyk and Resourcely are building tools to ensure higher quality parameters for developers to remain secure.
Provisioning, Catalog, and Context
Consider the alert fatigue that exists in security more broadly. Then, extend that to an already constrained supply of software engineers, and it's unlikely the problem will get better just by offloading the alerts onto developers instead of security operations (SecOps) teams. But the reality is that SecOps is already dependent on developers for patching the vulnerabilities that any security system finds.
In fact, 60% of data breaches are caused by vulnerabilities that security teams already knew about and had filed a ticket for. When it comes to cloud security, the biggest bottleneck is actually empowering developers to fix existing problems. So what will the future security parameters look like to address this?
Protecting The Point of Provisioning: 30% of cloud vulnerabilities are the result of misconfiguration when infrastructure is initially set up. The more effectively companies can leverage tools to ensure proper configuration, the more they can stop security vulnerabilities from being created at the outset. IAC tools like Terraform’s Open Policy Agent attempt to ensure correct policies for infrastructure configuration, but require the use of verbose language that can be easily written incorrectly, leading to vulnerabilities anyways.
Creating a Rich Catalog: Cloud providers like AWS attempt to provide context on who owns a particular infrastructure resource, how it's configured, and what it has access to. Unfortunately, in practice, the process of understanding the details around any infrastructure is an exercise in manual detective work and requires frequent follow-up. The more effectively companies can leverage tools to ensure a complete picture of an organization’s catalog of infrastructure, the more secure those resources will be.
Providing Developers With Context: Finally, the fact that developers leave ~27-30% of tickets completely unaddressed is not an indication of lazy developers. The reality is that developers lack sufficient context to easily understand and fix a particular vulnerability. The more effectively companies can leverage tools to ensure developers have quick and easy access to the necessary context for patching vulnerabilities, the more quickly developers will address those concerns.
Conclusion: The Cloud Battleground
Cloud security companies like Wiz and Orca Security have recently exploded onto the scene, having been founded in 2020 and 2019 respectively. Wiz was able to surpass $100 million in ARR within 18 months, with other cloud security companies seeing similar results in the months around COVID and beyond. Even Crowdstrike, which has expanded to include cloud-native products, has seen ~$100 million ARR in cloud security and 100%+ growth in cloud-based workloads.
In part, the ability for these companies to see such significant traction comes from the effectively “blue ocean” market for cloud security. Imagine the world of on-prem security, and all the solutions selling cybersecurity, and all the dollars being spent to secure different workloads. Then, imagine all of that effectively disappeared. In the early days of companies transitioning to the cloud that transition was so rapid that there was a very limited landscape for cloud security tools. As a result, the majority of the current cloud security tools took the old framework (gather data, prioritize signals, and trigger alerts) and simply applied it to cloud workloads.
Going forward, the proliferation of the cloud will only continue. Security threats will continue to increase in both volume, and complexity. The paradigm shift in security won’t come from simply continuing to gather data, prioritize signals, and trigger alerts. Instead, the market will likely transition from security-minded development to developer-minded security. As a result, DevSecOps will become the only framework for both development and security.
Meanwhile, the code level has become the new battleground for many would-be hackers. Software supply chain attacks happen when “a cyber threat actor infiltrates a software vendor's network and employs malicious code to compromise the software before the vendor sends it to their customers.” The number of attacks on software supply chains rose 650% in 2021 alone. Gartner predicts that by 2025, the number of organizations that have experienced attacks on their software supply chain will grow 3x to 45%. Cloud computing consists of code, containers, microservices, and databases. Whether its code at the application level, or from Infrastructure-as-a-Service, developers are now a critical part of the cloud security battle.
*One or more Contrary affiliates have invested in companies in the cloud security market, including Stytch and Rubrik which are included in the Cloud Security Market Map above.





