Actionable Summary
Cybersecurity is a clear priority for CTOs and executives: Security is a major theme in 2022. Morgan Stanley’s Annual CIO Spend survey from March 2022 reported that security software was the 2nd highest priority spend for CTOs and Executives. Morgan Stanley also predicts that endpoint security will be the second biggest beneficiary of cloud migration spending over the next twelve months.
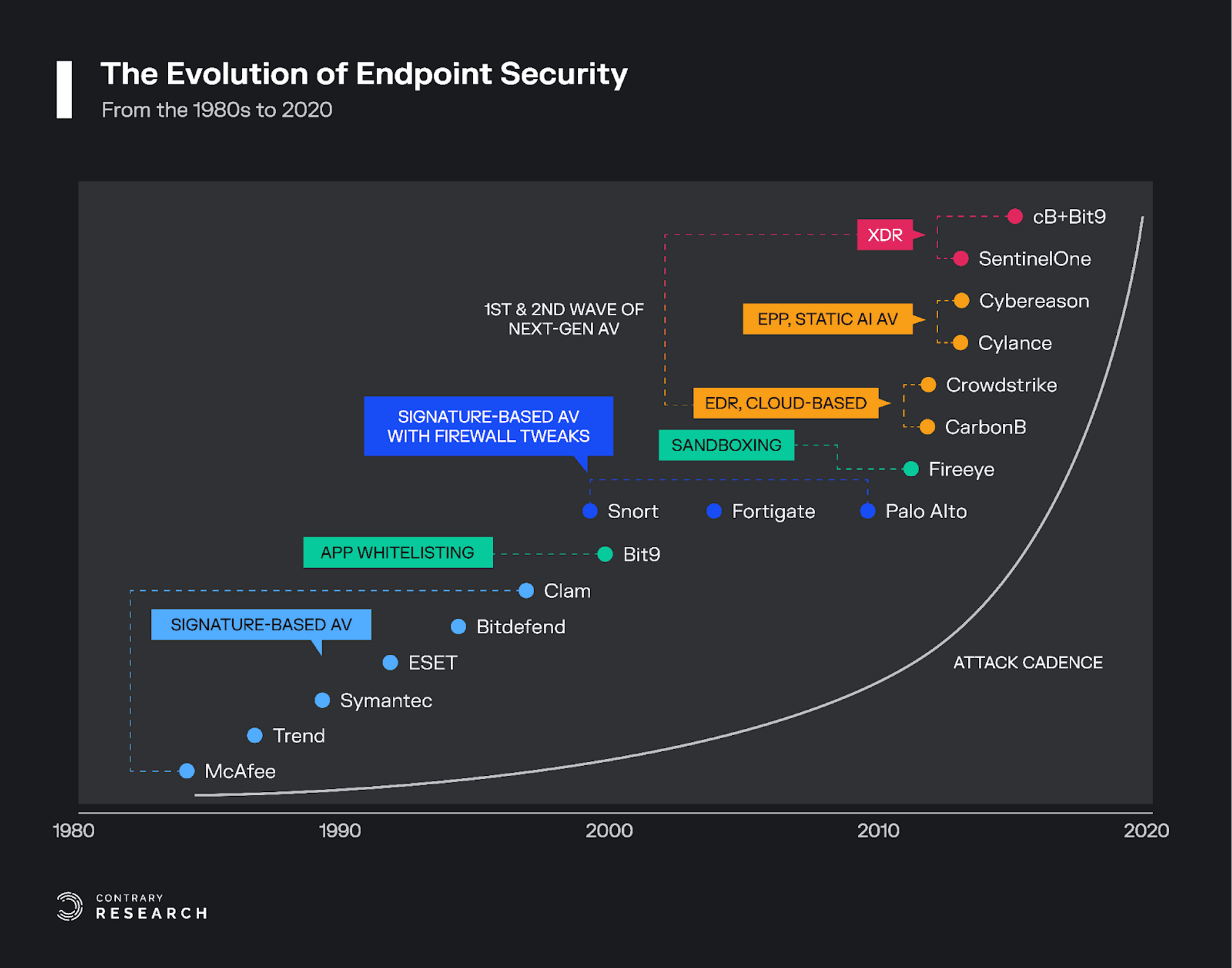
The endpoint protection market is rapidly evolving: The first cybersecurity companies in the 1980s, such as McAfee and Trend Micro, provided endpoint security services. By the 2000s, Symantec’s Norton rose to become an early pioneer in endpoint security. Today, companies like CrowdStrike have leveraged the cloud to become market leaders.
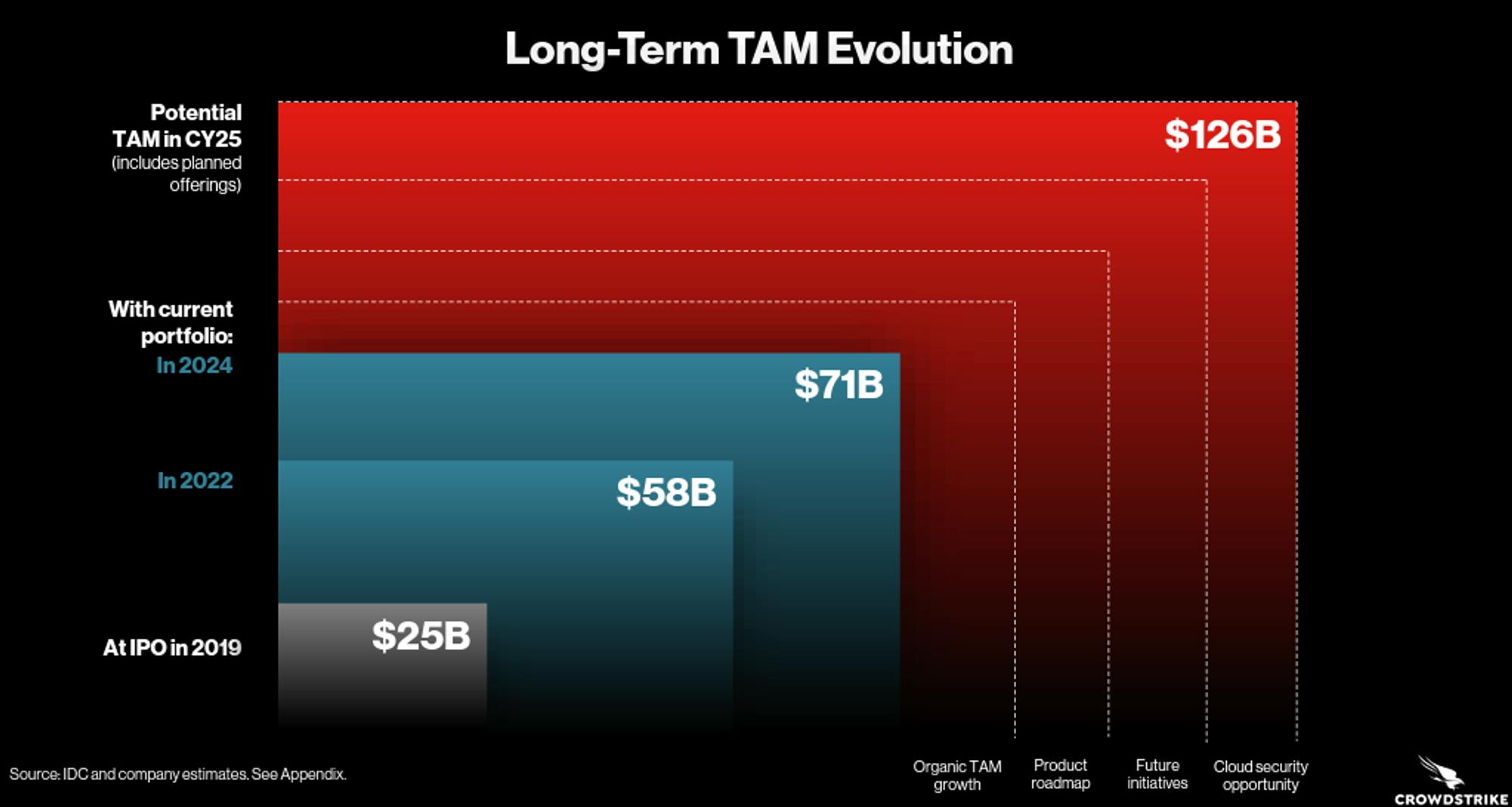
The market opportunity is large and fragmented: The largest companies within cybersecurity all provide endpoint security as a core business line. The $30 billion endpoint security market represents the largest market opportunity within security, which grew by over 29% in 2021. Over the next 5-years, IDC and CrowdStrike believe the industry can reach an almost $126 billion TAM due to the expanding number of devices and workloads moving to the cloud.
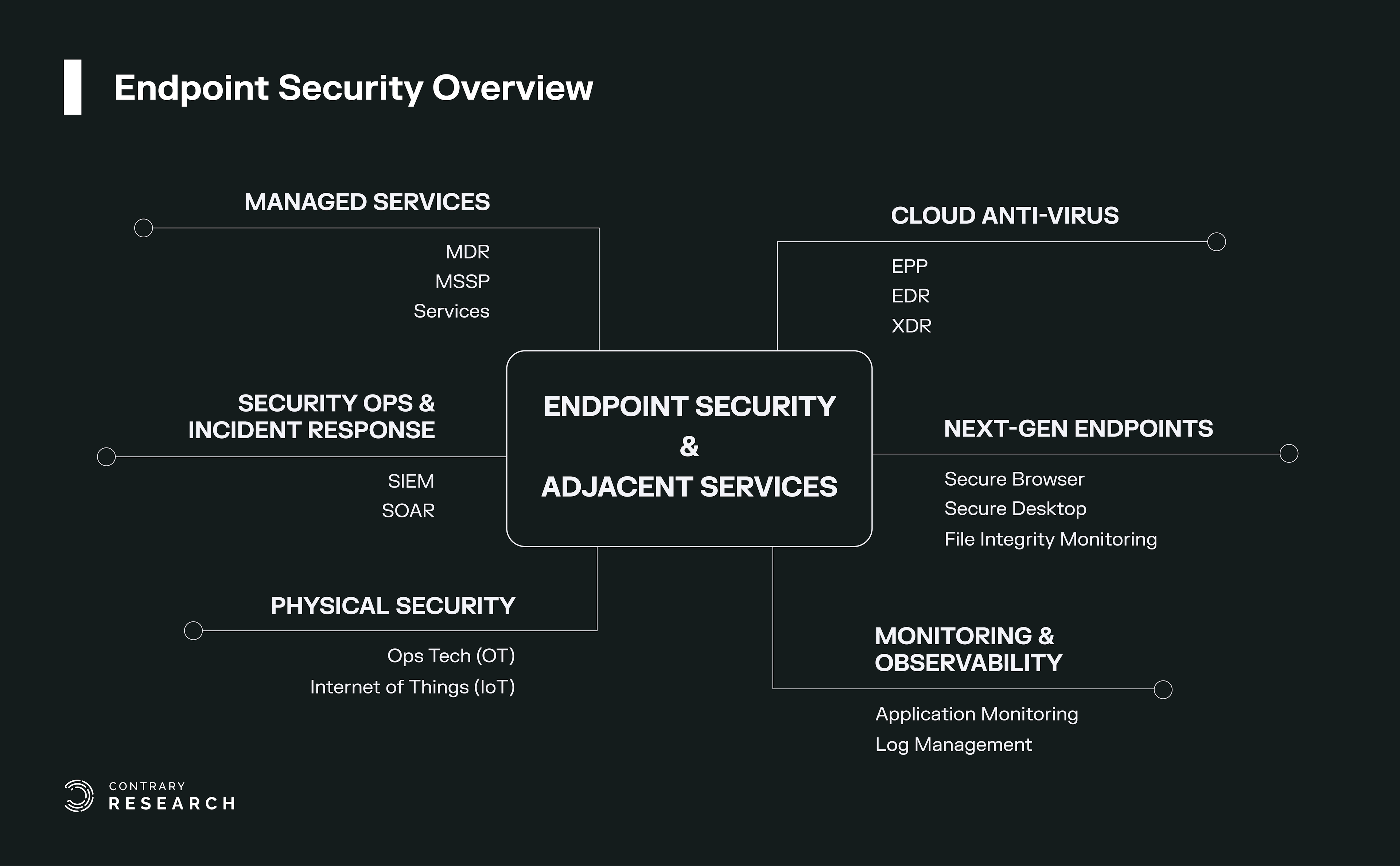
New paradigms and sectors continue to emerge: Enterprise endpoints are often the target of attack vectors against organizations. The sophistication of new attacks has given birth to adjacent endpoint sub-sectors such as MDR, SIEM, SOAR, and SecOps, while the rapid growth of newer technologies and startups has given rise to sectors such as Extended Detection and Response (XDR) and Cloud Workload Protection Platforms (CWPP). Meanwhile, Operational Technology and Industrial IoT endpoint devices are also gaining traction.
Endpoint security deal activity skyrocketed in 2021: According to Momentum Cyber’s 2021 report, endpoint security consulting and MSSP security players accounted for the largest M&A deals in 2021. Endpoint security led industry deal counts and the SecOps and Threat Intel industry experienced 171% YoY growth, the largest of any sector within security.
Endpoint protection and security operations are fundamental to understanding cybersecurity: To understand the future of cybersecurity, one needs to develop a foundational framework of the endpoint protection industry and its adjacent industries.
Source: Contrary Research
Endpoint Security: The Basics
Endpoint security is software for securing “endpoints”, i.e. entry points of end-user devices that connect to a company’s network. Endpoint devices may include desktops, laptops, smartphones, servers, workstations, IoT devices, printers, and other such devices. Over time, endpoint security has evolved from antivirus programs installed on desktop computers into platforms that provide comprehensive protection for devices, users, and the cloud.
Endpoint security is the most foundational and critical security element for an organization because it exists at the intersection between humans and machines. An endpoint is therefore a critical point of vulnerability for companies. If bad actors are able to exploit endpoints in a way that compromises a company’s devices and data, the damage to both the company and its customers can be catastrophic.
This report provides an overview of the endpoint security landscape within the modern enterprise. Endpoint security is concerned with developing solutions for protecting hardware, networks, and users.
The most established and enduring security companies built their foundations on endpoint security. However, as will be discussed in greater depth below, the oldest cyber security guards like McAfee and Symantec failed to remain dominant players, and emerging players like CrowdStrike and SentinelOne are now capturing market share from the endpoint custodians.
Endpoint security has seen the emergence of multiple adjacent industries that have emanated from protecting the enterprise. This report explores Managed Detection and Response (MDR), Managed Security Service Providers (MSSP), Security Information and Event Management (SIEM), and Security Operations (SecOps). Dominant companies and high-potential startups within each of these sectors are highlighted. Lastly, the report concludes with a discussion about the convergence and future evolution of the endpoint security industry. This convergence is most pronounced within emerging categories like Extended Detection and Response (XDR) and Cloud Workload Protection Platforms (CWPP).
Market Opportunity
The market opportunity for endpoint security is currently the largest within cybersecurity. Estimates from CrowdStrike, SentinelOne, and Fortinet peg the market size at around $25-30 billion in 2022 expanding to $40 billion in 2024. According to the IDC, the worldwide corporate market for endpoint security grew 14% in 2020 and 29% in 2021. In addition, combined revenue from key endpoint protection companies grew from $7 billion in 2019 to $10 billion in 2021. The key endpoint companies, by market share, include the likes of CrowdStrike, McAfee, and Microsoft.
There were two key catalysts for the growth of the endpoint security market in 2020 and 2021. First, the move to the cloud. With workloads moving to the cloud, a growth of managed detection response (MDR) services, and the growing adoption of IoT devices, the market opportunity for endpoint security is continuing to grow. The second catalyst was the increased number of vulnerable endpoints due to the shift to remote work, which dispersed more endpoints out of the relative security of an office, and into employees homes. Remote work forced many companies to purchase new digital equipment for employees to connect to their respective corporate networks remotely, which only further increased the number of endpoints for attackers. Looking forward, these catalysts show no signs of slowing: the endpoint security market is projected to grow to over $126 billion by 2026, according to estimates from the IDC and CrowdStrike.
Source: CrowdStrike
The Evolution of Endpoint Security
The threat of computer viruses materialized for the first time in the 1970s. By 1980, computer viruses were able to self-replicate and proliferate across networks. In the early days of the internet, everything was open, without firewalls, meaning one virus could spread to virtually every internet-connected machine across the entire web. The response to these early viruses was the birth of the first generation of cybersecurity companies.
Legacy Endpoint Security Solutions
The leading players in the first era of endpoint security included McAfee, Symantec, and Trend Micro. These early solutions provided firewall, file encryption, and infrastructure security services. The prevailing paradigm was signature-based antivirus security, which suited on-prem infrastructure. During this period, McAfee released the first consumer antivirus platform for desktop applications, which was considered cutting-edge at the time.
Original Source: SentinelOne Presentation
Signature-based detection technology worked by matching known patterns from a database. When installed, these security solutions would review the signatures of incoming documents to detect if they matched a known malicious signature in the database, which meant that signature-based antivirus solutions could only protect against threats already cataloged in their database. If there was a match, the antivirus would reject and terminate the process or file. Since these first-generation signature platforms were not cloud-based, they had to be updated periodically to protect against new threats.
Eventually, cybercriminals learned to work around signature-based security solutions by continuously changing a virus’s signature and developing new forms of malware that could evade antivirus software. Early endpoint security platforms were also on-prem, necessitating users to update to the latest version of antivirus software to detect new forms of signature malware. However, as the number of malicious programs grew, so did the size of the signature database, which led to escalating consumption of disk space, CPU, and memory by on-device antivirus programs.
Legacy players in endpoint security built and relied on these businesses as profit drivers for decades, and were slow to adapt to the rise of the cloud and mobile. Partially, this was a result of poor leadership. For example, after a decade as the industry leader, McAfee experienced several high-profile executive departures, a revenue exaggeration scandal, and went on to have five different CEOs in the early 2000’s. Symantec also lost some key leaders around 2013, who were instrumental in the company's early years.
As a result, many of the legacy players saw limited internal innovation, few startup acquisitions, and failed to maintain their monopoly in the endpoint market. By the time they started to adapt to the new world, companies like CrowdStrike had already started capturing market share. For more on the history of endpoint security, see the explainers on this topic from Trellix, Convequity, and SentinelOne.
Despite all this, legacy players have managed to hold on to large customer install bases over the past decade. According to the 2019 IDC security report, for instance, Trend Micro was leading the endpoint security market with ~11% market share. However, over the past decade, legacy players have seen their market share decline, and revenue growth slow. Meanwhile, modern EDR companies like CrowdStrike have experienced rapid growth. From 2019 to 2021, CrowdStrike increased its market share from 5.8% to 12.6%. As of November 2022, CrowdStrike reported ARR of over $2 billion, representing 59% year-over-year growth.
The Disruptors: Modern Endpoint Players
By 2011, emerging companies, like CrowdStrike, saw the shortcomings of signature-based antivirus and began using cloud solutions. These next-generation platforms incorporated signature-based detection dynamically on the cloud, rather than statically on-prem. Cloud-based security solutions had the advantage of improved bandwidth, and allowed for software updates to be easily pushed to devices anytime, rather than having to wait for the end of a quarter to buy new software.
Emerging companies leveraged faster computing and storage of the cloud to build better endpoint security antivirus products, giving rise to a new category of endpoint security solutions: endpoint detection and response (EDR). An EDR is a cloud-native endpoint security solution that continuously monitors end-user devices to detect and respond to cyber threats like ransomware and malware. EDR platforms utilize a single, lightweight agent that can be installed on a device easily via download. These platforms require less memory and storage on-device because most of the database of known threats is stored on the cloud. As a result, modern endpoint protection solutions are able to provide a more holistic solution to protect against a broader set of cyber attacks such as data loss, phishing, fileless attacks, signatureless malware, etc. than legacy solutions which are static and on-prem.
At this stage, the modern endpoint security stack can largely be categorized into six buckets. This report covers these categories in greater depth below, with a discussion of representative players.
Endpoint Detection and Response (EDR)
Managed Detection and Response (MDR)
Managed Security Services Provider (MSSP)
Security Information & Event Management (SIEM)
Security Orchestration and Automated Response (SOAR)
Security Operations (SecOps)

Source: Contrary Research
The Endpoint Landscape
Endpoint Detection & Response (EDR)
Today’s advanced antivirus solutions have converged around Endpoint Detection and Response (EDR) and Endpoint Protection Platforms (EPP) after decades of the popularity of legacy signature antivirus. EPP was the first iteration, before the industry settled on EDR. While both terminologies are similar in meaning, they represent different technology stacks.
EPP required heavier agents, and could detect and eliminate threats, but couldn't capture the bigger picture of the threat landscape on a device. The focus of EPPs was to detect breaches and block attacks on a device at the first point of entry. However, the average dwelling time for an attacker (i.e how long a hacker intrudes into a network before being discovered) was more than 56 days in 2019. Therefore, there was a gap in these EPP solutions. There needed to be more protection that could deal with an attacker even if they had penetrated a network without being caught.
EPP soon evolved into EDR solutions to solve this problem. EDR platforms were built on cloud-native architectures to be more holistic, providing advanced threat prevention, monitoring, detection, and remediation capabilities. EDR uses a lightweight agent that sends telemetry data to the cloud for analysis, and SecOps (Security Operations) teams can then remotely confirm the threat and eliminate it. An EDR endpoint agent on a device can perform actions such as taking action against hacks, deleting corrupt files, and returning a system to its previous state with some assistance from SecOps teams. This is the core reason for the "detection and response" element within EDR as compared to EPP.
EDR platforms also incorporate behavioral machine learning algorithms such as UEBA (User End Behavioral Analysis), Network Traffic Analysis (NTA), and AI/ML algorithms to increase threat detection capabilities. EDRs are designed to identify much more sophisticated attacks, such as polymorphic and fileless malware, than traditional antivirus. They are able to perform continuous monitoring on a fleet of devices, and constantly gather telemetry data.
The vendors that provide EDR endpoint security solutions can be broadly categorized into two buckets. The first category is cloud-native EDR platforms that include CrowdStrike, SentinelOne, and Cybereason. The second category are large technology incumbents who provide endpoint solutions as part of a larger enterprise offering. They include Microsoft Defender, Palo Alto Networks Cortex, Blackberry, Fortinet, Sophos Intercept, Cynet, and Deep Instinct. With regard to market leadership, the IDC ranks CrowdStrike’s solution as a leader in product offerings. For a comparison of various offerings, see this list of reviews published by Gartner Peer Insights.
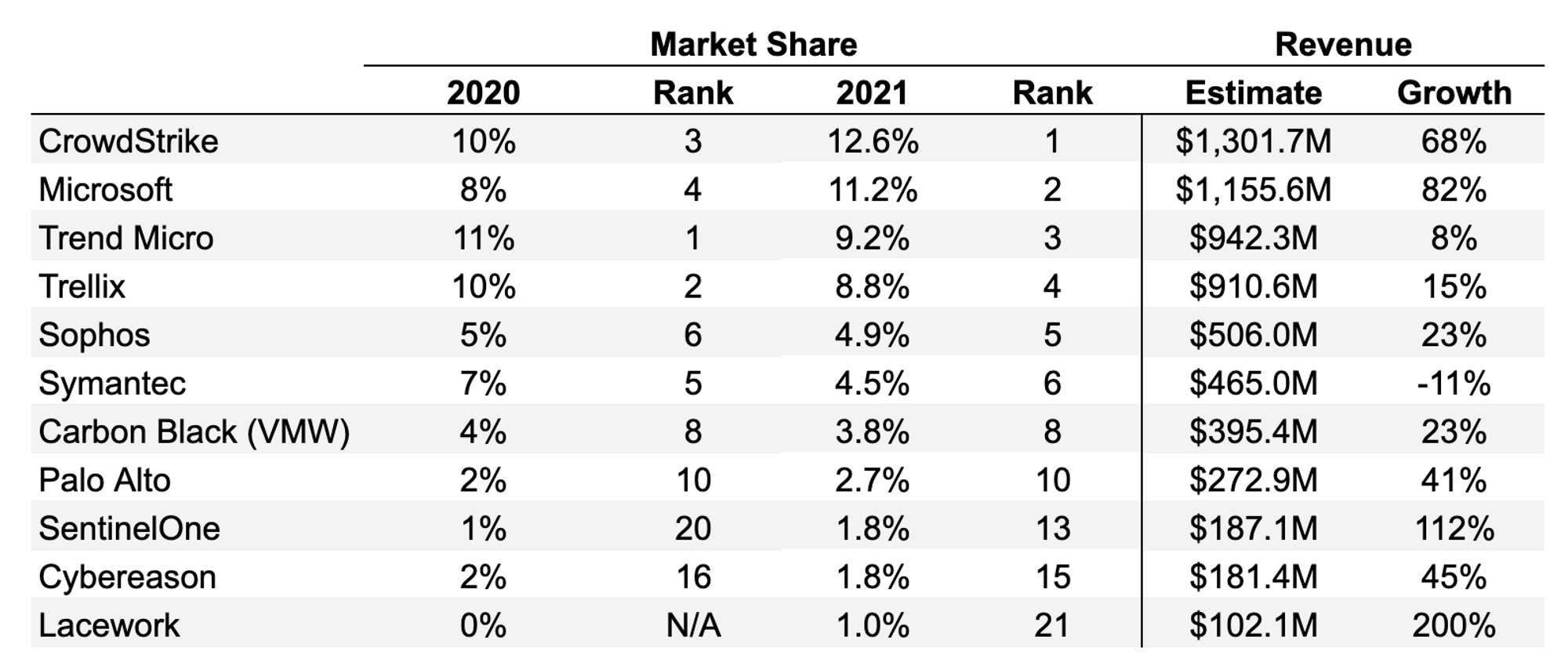
Source: IDC
CrowdStrike
CrowdStrike was founded in 2011. It is widely regarded as the first mover because it was one of the first security companies that introduced a cloud-based, lightweight agent (i.e. an architecture where the monitoring software does not require a component on the monitored endpoint). George Kuntz, the CEO of CrowdStrike, had worked at McAfee for more than 7 years prior to co-founding CrowdStrike, and had seen the flaws of the traditional antivirus platforms.
CrowdStrike’s platform, “Falcon” consumes only 35MB of storage space compared to over 5GB required for the legacy signature-based antivirus solutions. Falcon uses machine learning to learn user behavior, block attacks, and delete corrupted files or malware. It can then share solutions to that malware or hack across all other endpoints on CrowdStrike’s network. As a result, every CrowdStrike platform becomes more intelligent because they are constantly learning newer threat techniques. This builds an important network effect..
CrowdStrike has been one of the most successful cybersecurity companies over the past decade. It generated over $2.3 billion in annual recurring revenue during its 2022 fiscal year, representing a 54% year-over-year growth and over $700 million in positive operating cash flow over the last twelve months as of November 2022. As growth from its initial tailwinds begins to decelerate, the next phase of growth for CrowdStrike will involve moving into adjacent markets. The company has begun offering new services such as zero-trust security services, cloud workload protection platform (CWPP), and identity security through the acquisition of Preempt, SecureCircle, and Humio. Muji, at Hhhypergrowth, had a blog post outlining all the major insights from their annual Falcon conference.
Over the past decade, the company has evolved to become a major platform by providing adjacent services in addition to its initial core offering. It has transitioned from being just a point solution in endpoint security to becoming more of a fully integrated IT company.
SentinelOne
SentinelOne was founded in 2013. SentinelOne provides EDR services to SMBs, but uniquely with more emphasis on security automation and using behavioral AI in their solutions. SentinelOne is one of the fastest-growing endpoint companies, competing directly with CrowdStrike. SentinelOne uses a singularity XDR Platform that ingests, correlates, and queries petabytes of structured and unstructured data from a myriad of ever-expanding disparate external and internal sources. SentinelOne uses a static AI that when downloaded, normalizes and establishes a baseline on the user's system.
One key distinction is that SentinelOne’s product can be used both on cloud and on-prem. SentinelOne has also been involved in M&A with the acquisition of Scalyr which allowed it to expand its product into a security data lake. In addition, the acquisition of Attivo networks allowed SentinelOne to enter the identity access and data storage market. SentinelOne generated over $300 million in LTM revenue as of November 2022, though the company is still burning through cash, with LTM negative operating cash flow of $134 million as of November 2022. SentinelOne remains an important company to watch in this category.
Cybereason
Cybereason is an endpoint security platform that offers a variety of EDR, security monitoring, and managed detection services. The company was originally founded by former cyber security experts from the Israel Defense Forces. Cybereason’s MalOps engine correlates data between multiple endpoints like firewalls and SIEM, allowing security teams to identify threats quickly and more accurately than traditional EDR solutions. They also provide managed detection and response (MDR) services, which are outsourced cybersecurity services for SMBs.
In July 2021, Cybereason raised $275 million in Series F funding at a valuation of roughly $3 billion. The company has also received attention, having been named a “Visionary” in the 2021 Gartner Magic Quadrant for Endpoint Protection Platforms and a High Performer in the MDR Report conducted by Forrester. Despite this success, Cybreason introduced its EDR platform much later than Crowdstrike, Microsoft, or SentinelOne did, only launching its solution in 2017. As a result, it hasn’t yet seen the same degree of success as earlier entrants. To learn more about Cybereason, you can read Contrary Research’s full report on the company.
Tanium
Tanium offers a unified IT service management endpoint platform for companies to simplify endpoint security and configuration compliance. Tanium is one of the more established cybersecurity companies, having been founded back in 2007. The Tanium solution can be deployed on-prem or in the cloud. The platform aims to unify security and IT operations teams with a single view of critical endpoint data in real time. It encompasses everything from asset and threat discovery, client management, and compliance management to threat-hunting capabilities.
One key takeaway about Tanium is that the majority of its technology is not used directly to detect and protect users against hacks, in contrast with Crowdstrike which does. Instead, Tanium primarily focuses on IT infrastructure management, monitoring or tracking for misconfigurations, patch management, and asset monitoring of IT devices to ensure they are well-equipped to handle the actual hack. They ensure companies are compliant with standard regulations and patch against any vulnerabilities. For more on Tanium, Steven Sinofsky of a16z wrote an overview on the company, which sheds more light on the Tanium platform.
Deep Instinct
Deep Instinct was founded in 2015. It applies AI deep learning frameworks to cybersecurity endpoints. Its deep learning technology specifically protects against zero-day threats and APT attacks with high accuracy. Deep Instinct protects the enterprise’s endpoints such as mobile devices or infrastructure, whether or not they’re connected to the internet.
Deep Instinct’s product solution reportedly predicts and prevents known, unknown, and zero-day threats in <20 milliseconds, 750x faster than the fastest ransomware can encrypt. Deep Instinct has >99% zero-day accuracy and promises a <0.1% false-positive rate. This has the ability to push the frontier of the endpoint security market.
By applying deep learning technology to cybersecurity, enterprises can now gain protection against unknown and evasive cyber-attacks from any source. According to Forrester Consulting's Total Economic Impact study on Deep Instinct's Advanced Endpoint Security Solution, an organization could experience benefits of $3.5 million over three years versus costs of $600K, adding up to a net present value (NPV) of $2.9 million and an ROI of 446%. The ability to bring down the threat detection rate to 20ms powered by several hundred megabytes of deep learning models on a normal CPU machine is an important milestone for endpoint security.
Managed Detection and Response (MDR)
MDR can be thought of as the human extension of EDR platforms. MDRs are external cybersecurity services that provide advanced 24/7 skills and services through security professionals like security analysts, engineers, or researchers. These professionals provide a higher level of expertise, security analytics, proactive threat hunting, and incident response to situations at the host or network level.
MDRs emerged as a result of small and medium-sized businesses’ inability to afford to host their full-stack security operations center (SOC) or an IT Security department. The industry is further driven by a shortage of security professionals which makes MDR pivotal especially when an organization faces a new type of cyber attack and it needs an expert to assist in nullifying that threat.
The key difference between MDR and EDR lies in who is doing the underlying monitoring, detection, and response functions. When outsourcing this to a security provider, then it is an MDR service. When done internally, it is an EDR platform. MDR services rely on more-direct communications with a company's IT operations team.
The human component of security will continue to play an essential role in the future of cybersecurity. The only caveat is that if AI capabilities within XDR solutions continue to improve exponentially, there is always a chance MDR could be replaced by XDR platforms. However, there is significant evidence suggests that is still quite far off.
For example, In CrowdStrike’s FYQ1 ‘23 quarterly earnings call, CrowdStrike mentioned that its MDR business was showing the strongest growth amongst all its modules. The CEO was quoted as saying that “customers want to complement their EDR solutions with an MDR component that provides them with advice.” According to the 2022 IDC Survey report, CTOs were asked “How will your organization's planned spending [budget] on the following IT services change for 2022?” and approximately 45% of companies intended to spend more on MDRs in 2022 compared to 2021.
Key players in MDR include CrowdStrike, Deloitte, Palo Alto Networks, eSentire, Arctic Wolf,Red Canary, and Critical Start.
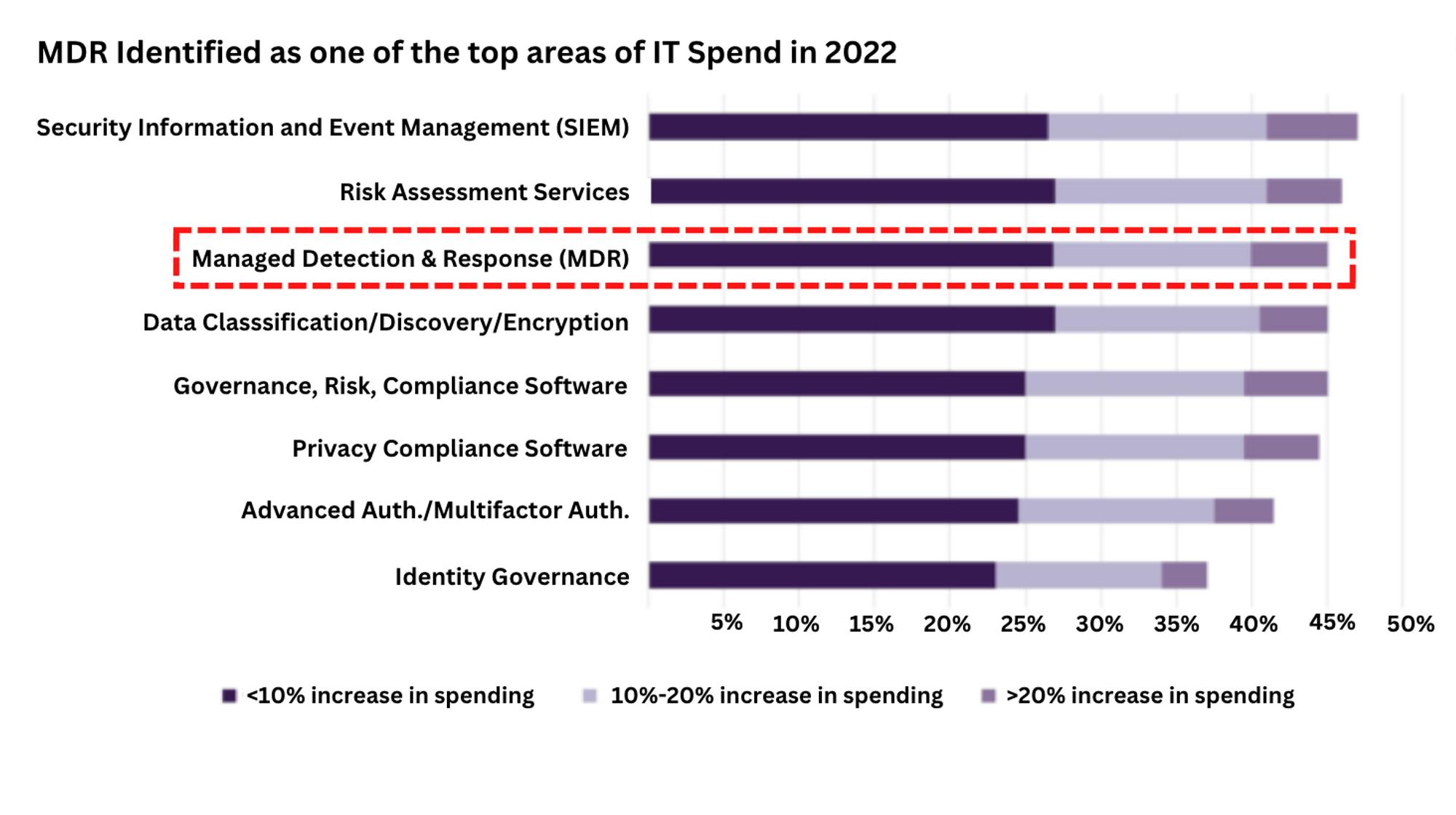
Source: Truist Securities and IDC
Critical Start
Critical Start is an MDR focused on helping customers improve security capability. They help organizations of all sizes determine their security readiness condition using its framework, the Defendable Network. Critical Start delivers managed security services, incident response, a professional services response, and a research unit. Critical Start’s platform integrates with multiple vendors in endpoint (EDR) like CrowdStrike, and security information and event management (SIEM) platforms like Splunk to allow them to get increased visibility into monitoring a company's network.
eSentire
eSentire is an emerging Canadian MDR service provider. Its MDR service approach is tailored toward zero trust segmentation, policy-based enforcement, and automation solution. They provide manual monitoring of customers' networks to detect and block cyberattacks in real time. The features include real-time deep-packet inspection, human-assisted machine learning, behavior-based anomaly detection, signature-based intrusion detection and prevention, and frequent analyst communications. The company’s product combines machine learning XDR technology, 24/7 threat hunting, and security operations services to mitigate business attacks. The company believes its ease of deployment is a competitive advantage, with a mean time to contain active cybersecurity threats in less than 15 minutes.
Managed Security Services Provider (MSSP)
The next evolution of MDR is an MSSP. MSSPs are similar to MDR in that they provide outsourced cybersecurity services to companies. However, MSSPs are focused on more operational and lower-level security tasks which can augment or replace an organization’s internal security team.
An MSSP operates a security operations center (SOC) which provides round-the-clock security monitoring, log data aggregation and security incident support. The MSSP market has become a vital part of the cybersecurity ecosystem primarily as enterprises face an in-house security skills shortage, while cyber attacks are intensifying. According to the Cybersecurity Ventures jobs report, at the end of 2021 there were approximately 3.5 million unfilled cybersecurity jobs around the world, with 500,000 of them in the United States.
To overcome the dilemma, many CSOs see MSSPs as a way of gaining access to specialized security expertise and 24/7 monitoring capabilities while reducing operational overheads. One key driver for the sector is cost reduction — companies will opt for MSSPs since they lower the total cost of ownership for staff and enable them to stay up to date on compliance with regulatory requirements.
There are a number of key differences between MDR and MSSP. MDR platform providers are focused on helping organizations be proactive to threats, meanwhile, MSSPs are designed to be reactive when a breach has occurred. Unlike MSSPs, MDR services focus on advanced detection, response, and threat hunting rather than security alert monitoring.
The MSSP market remains highly fragmented, with no single vendor controlling greater than a 5% market share, according to estimates in the report “Cybersecurity 2022 and Beyond” by Truist Securities. This fragmentation is primarily due to the low barrier to entry required within the industry. The key players in this market worth highlighting are Arctic Wolf, Optiv, IBM, Verizon, Wipro, TCS, and Infosys.
Arctic Wolf
Arctic Wolf is currently the largest provider of MDR and MSSP cloud monitoring services. The platform offers solutions such as continuous security monitoring and security protection. It directs customer network traffic through the company's secure cloud infrastructure where it is analyzed and correlated with external data sources. These product features include threat detection and response, and risk management services. Arctic Wolf is one of the leading providers within the industry, and continues to release new technologies that support its clientele within SecOps.
Security Information & Event Management (SIEM)
SIEM is a centralized technology for continuously gathering security logs and correlating disparate events from networks, systems, and device logs to generate real-time monitoring and alerts. SIEM assists organizations to recognize potential security threats and vulnerabilities before an attack causes harm to a business. SIEM actually started out as a compliance tool rather than an actual threat protection software, before being applied as a security solution.
With the ever-growing complexity of the enterprise technology stack, SIEM tools help security operations teams with monitoring platforms by identifying and categorizing security events, logs, and data across the enterprise. According to a 2021 IDC Security SOC Tools survey, some of the top challenges with SIEM platforms revolve around staffing, data ingestion, and expertise. This is the area where MSSPs and MDRs, as discussed above, utilize SIEM tools that assist them with log monitoring, vulnerability scanning, and orchestration tasks involving aggregating information. Next-gen SIEM platforms that have more advanced data ingestion capabilities and advanced features around log aggregation include emerging startups like Panther Labs, Exabeam, Securonix, Demisto (owned by Palo Alto Networks) and Hunters AI.
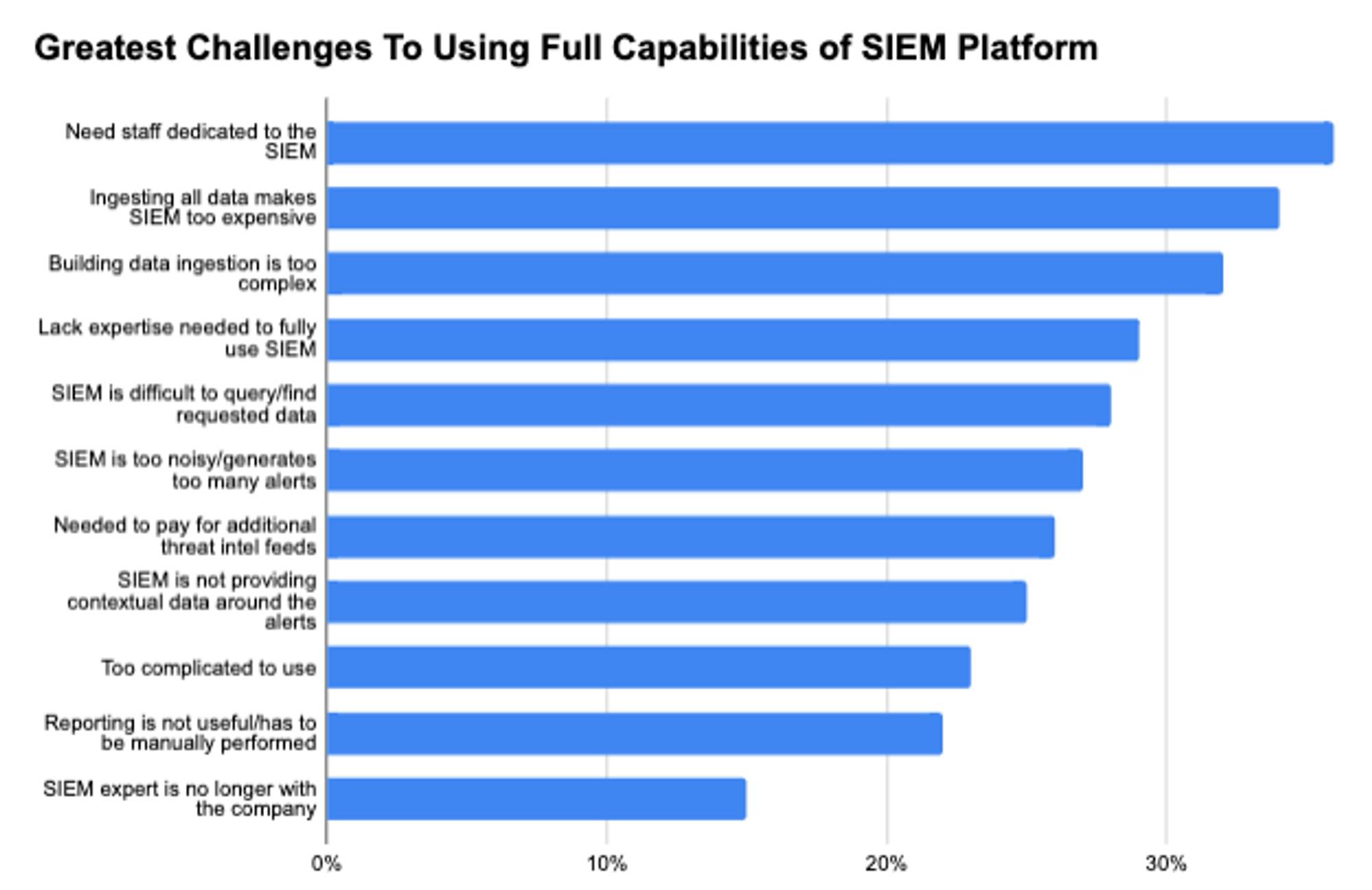
Source: IDC
Splunk
Splunk is a software platform used to search, analyze, and visualize IT Infrastructure data gathered from websites, applications, sensors, devices etc. Splunk was founded in 2003, and it was one of the first companies to give IT teams the ability to aggregate and visualize data from a wide variety of sources, before having its IPO in 2012. As a result, it had become the leader of the SIEM space for many years and developed a pricing power amongst large enterprises. Today, Splunk has become one of the most expensive platforms within an enterprise budget.
In 2020, Gartner ranked Splunk as the number one vendor on the IDC Worldwide SIEM Market Share Report. The platform costs upwards of hundreds and millions of dollars for the average enterprise, depending on how much data is consumed. Splunk’s pricing has been widely criticized by a variety of customers, as seen by customer reviews, due to the way the platform logs and ingests data. As a result of its leadership position for several years, Splunk has been seen as largely complacent. Emerging players like Panther Labs and Hunters AI are focused on taking portions of the IT budget that was previously going to Splunk. There are articles, like “The Great Splunkbundling” and several others, that convey how much disruption is happening within the SIEM market.
Panther
Panther Labs is a cloud-native threat detection platform for SIEM. Panther uses artificial intelligence to centralize, normalize, and analyze security data to enable cybersecurity teams to detect, investigate, and monitor security threats and misconfigurations at scale.
Companies like Panther Labs have largely emerged as a result of leveraging the modern architectures of Snowflake’s compute and storage, which significantly reduces the cost of data storage. The volume of data has grown exponentially over the past few years, which makes platforms like Splunk increasingly expensive. Customers are realizing they can use platforms like Panther, where their architecture is built on the storage layer of the three major cloud providers, and they can leverage the speed of Snowflake. Platforms like Splunk were built in the early 2000s, and have not been able to easily replace their legacy architecture to match modern data infrastructure for cheaper storage. As a result, Panther’s speed and cheaper storage have increasingly appealed to customers. To learn more about Panther Labs’ architecture and platform, read more in our memo.
Exabeam
Exabeam provides threat detection using analytics around user behavior. Exabeam’s platform is cloud-based, and incorporates User Entity Behavior Analytics (UEBA), SIEM log data, and analytics into one platform to enhance its threat detection capabilities.
The solution tracks employees' activities on a network using existing log data and then employs machine learning, state full user tracking, automated user session assembly, and additive risk scoring to create user profiles. It also sends out security alerts when anomalous and suspicious behaviors have been detected. Exabeam’s SIEM product has been highly rated by professionals including in the 2021 Gartner Magic Quadrant for SIEM. It was the highest-rated product in the Leaders category for its product sophistication. A key reason for the company’s success is because most SIEMs are designed to provide functionality, not results. With Exabeam’s packaged use cases and content, security teams can manage each step in Exabeam’s Threat Detection, Investigation, and Response (TDIR) workflow with automation and additional context to achieve repeatable outcomes.
Security Orchestration and Automated Response (SOAR)
SOAR refers to technologies that enable organizations to streamline security operations. SOAR tools help with collecting inputs monitored by the SIEM and assist in prioritizing incident response alerts. SOAR brings automation and orchestration into manual and repetitive tasks for security operation teams.
The constant alerts that security teams receive on a daily basis are growing at an increasing rate. According to a November 2021 IDC Security report, security staff get hundreds of alerts every day depending on the organization. SecOps staff spend an average of 30 minutes for each actionable alert, while 32 minutes are lost chasing each false lead. Therefore, efficiency and effectiveness have become paramount. SOAR is a triaging service that helps to collect data and automatically respond to lower-level security events or false positive alerts. It leaves high-level threats to security professionals freeing up time for IT teams to focus on more important priorities.
SIEM products help to gain a bird’s-eye view across an organization, but the process of responding to alerts remains very manual. The ongoing shortage of IT security talent and enterprises' difficulty in managing large numbers of security products has heightened the need for SOAR tools.
To summarize the differences between SIEM and SOARs. SIEM solves for visibility and monitoring, while SOAR solves for taking automated actions and remediation. SIEM consolidates and correlates log data. SOAR creates a system and process for collecting data from SIEM to define, prioritize, and automate incident response activities and workflows.
Key players in this category include Splunk Enterprise Security, Sumo Logic Cloud SIEM, Elastic SIEM, FireEye Helix, Cyware, ReliaQuest, and Swimlane, Tines.
Security Operations (SecOps)
SecOps is a centralized process responsible for managing security technology, inquiries, infrastructure, and applications needed for an enterprise. SecOps merges security processes, and broader operational systems, like ServiceNow, together. The security operations team could be internal or external, to the company. The key role of SecOps is to gather telemetry data and continuously monitor log data across an organization's networks, applications, and devices. This collection of disparate data is managed through the team’s security operations center (SOC) to identify the highest priority security alerts and risks. Tools used by the SOC scan the network 24/7 to flag any abnormalities or suspicious activities that have been flagged by the SOAR and SIEM systems.
Key players in SecOps include Awake, Exabeam, and Darktrace. Software for application monitoring including Datadog, New Relic, and Sentry, are also sometimes utilized by SecOps teams.
Securonix
Securonix is an emerging SecOps tool. It provides a cloud-native security analytics and operations platform designed to ingest security management with risk intelligence. The company's platform combines log management, user and entity behavior analytics (UEBA), SIEM, EDR, and SOAR into a complete platform that can be used by security operation teams. Securonix was built with an open and modular architecture to support diverse hybrid IT infrastructures. The platform allows for flexibility in deployment, integrations, and data storage. Customers can gain control and transparency into their data usage and utilize a split architecture solution where they keep data within their own cloud solution.
Expel
Expel provides a SOC-as-a-Service platform that provides security monitoring and response for multi-cloud environments. Expel utilizes security signals from its customers, so organizations can get more value from their existing security investments. It connects to customer’s systems remotely through APIs, not agents, so its SOC can start monitoring a customer’s environment in a matter of hours, letting its internal teams focus on more strategic security priorities.
Expel gives customers 24x7 coverage for cloud applications,infrastructure, networks, and endpoints. The company was named a Leader in the Forrester Wave MDR Q1 2021 as well as a Leader in the 2021 IDC MarketScape U.S. Detection and Response Service Vendor Assessment. Expel’s strategy is based on an automation-forward approach that accelerates response and remediation times. Over the last two years, the company has scaled its platform to handle over an 82% increase in security events a day and doubled the number of technology partners, and integrations.
The Future of Endpoint Security
The endpoint security market is rapidly evolving and converging towards multiple sectors over the next decade. These areas are XDR, cloud workload protection, and security at the edge using Industrial IoT.
Extended Detection and Response (XDR)
XDR can be viewed as the technology that aims to aggregate and converge different areas of endpoint security which have been discussed earlier in this report. Gartner coined the definition for XDR as a “SaaS-based, vendor-specific security threat detection and incident response tool that natively integrates multiple security products into a cohesive security operations system that unifies all licensed components.”
This definition refers to a centralized platform that is able to take a unified approach to respond to threats across an organization. The challenge of managing siloed, disaggregated security applications and increasing false positive alerts is a problem faced by an already short-staffed SOC team. XDR solves these problems. XDR extends visibility and protection control beyond just the endpoints but includes other areas such as the network firewall, cloud, SaaS applications, and emails. The objective of an XDR is to continuously gather data on a 24/7 basis from these points and continuously feed it into a machine learning model. Once a model is trained, it can automate and respond to threats, thereby reducing the number of alerts managed by SOC teams.
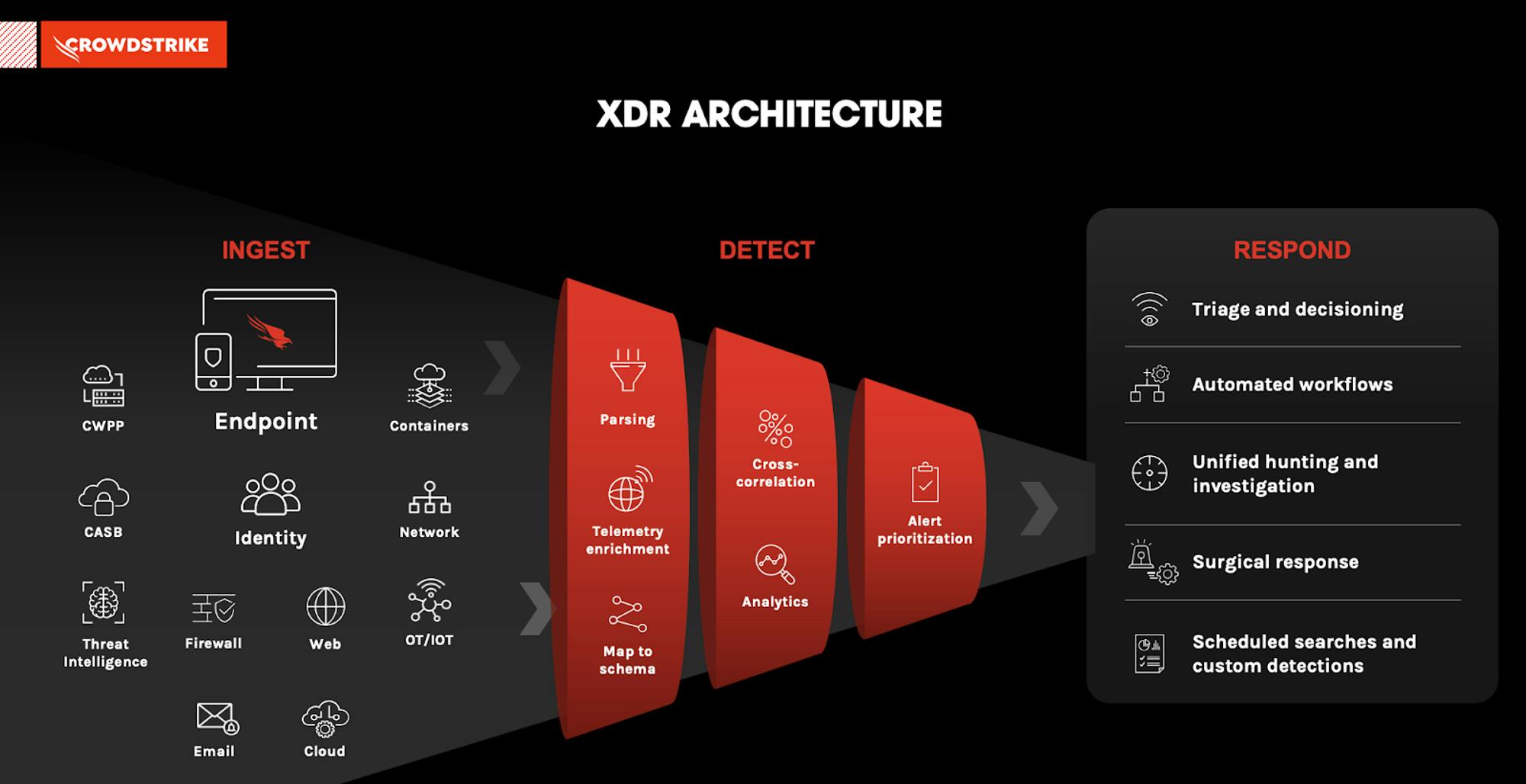
Source: CrowdStrike
XDR technology has three key components: ingest, detect and respond.
Ingest: First, Integration or ingestion is the merging of disparate telemetry sources using APIs to absorb data from all the devices discussed above, including data from emails, desktops, containers, networks, monitoring tools such as SIEM, and third-party software applications.
Detect: Secondly, after all of this data from a wide pool of sources has been ingested, parsed and mapped into a schema. Most of the data is analyzed using machine learning that is embedded into the architecture. The AI normalizes and correlates all the telemetry data to find outliers. XDR platforms are able to learn from threats proactively and develop methods to combat threats with speed and efficiency. It then helps to prioritize alerts to the Security operation (SecOps) teams.
Respond: Lastly, an embedded agent is able to respond to and remediate any attacks on the platform or triage cases to the SecOps teams based on pre-built workflows. It's able to take immediate action to block, contain, and roll back threats. XDR brings together different components of EDR, MDR, MSSP, SIEM, and Security Operations into one platform. The ultimate goal is to increase the productivity of their already short-staffed IT security teams and increase the sophistication of threat detection platforms. As discussed in our initial cybersecurity report, XDR is one step toward the ongoing aggregation and consolidation of the cybersecurity ecosystem. Key XDR players include CrowdStrike, SentinelOne, Anomali, Cynet, and FireEye XDR. Most importantly, it's important to note that XDR continues to be a vision that endpoint security aspires toward and it will continue to take time for the industry to achieve that full “XDR” platform.
Security Converging with Data Infrastructure
Security is increasingly becoming a data problem. There will likely be more convergence between cybersecurity and data infrastructure companies. For example, one recent development in this space is Amazon Web Services (AWS) just announced Amazon Security Lake in what looks like a major development for the security industry. Snowflake similarly announced its cybersecurity workload. Also, on the other end of the spectrum, we’ve seen Crowdstrike acquiring Humio and SentinelOne acquiring Scalyr. These are a few examples of the convergence between security and data infrastructure features and platforms.
The major theme here is companies requiring a centralized data lake or platform that is able to combine security data, feeds, and logs with data from the rest of a business like HR, marketing, etc. Companies want a single data lake for the whole company. The industry has realized the importance of being able to analyze and correlate security data in a broader company context. For example, in the case of a website breach, having data about DevOps apps like GitHub can provide more context to the identity security team to understand user log-in permissions, and who accessed what. The more data you have, the more signals you can review to perform a thorough investigation into a breach, or prevent issues before they occur.
A trend that is emanating from this convergence between security and data infrastructure is the rise of next-gen SIEM platforms. As discussed earlier in the report, platforms like Panther Labs, Securonix, and Hunters AI are starting to displace components of the traditional SIEM budget for established products like Splunk. During the Hadoop era, or pre-cloud, storing security data has historically been costly, slow, and required selection of what to keep. However, due to the rise of modern cloud infrastructure and the separation of pricing between storage and compute, security platforms can provide data-first solutions without worrying about exorbitant costs.
Today, companies are able to leverage cheap storage on the data lake, and a company only pays for compute time to query security data when analyzing an incident that has occurred. Several new companies are starting to adopt this approach, including the likes of Dropbox, DoorDash, TripActions and Figma. To learn more about the history of data infrastructure, and how companies like Snowflake are leveraging their platforms to extend into cybersecurity, read our deep dive.
Cloud Workload Protection Platforms (CWPP)
More endpoints and workloads are moving to the cloud. In recent years, we have seen endpoint protection players begin to provide more solutions geared toward solving cloud-based security threats. For example, CrowdStrike’s CWPP Solutions or Palo Alto’s cloud workload solutions.
Cloud workload protection is the process of monitoring for and managing threats on cloud workloads. It is about protecting a range of workloads on the cloud (microservices applications, containers, virtual servers, and Kubernetes). According to ETRs survey results in May 2022, Kubernetes and container security have seen a dramatic increase in adoption over the past year. This is primarily due to developers looking for cheaper and more efficient ways to build and deploy software in such a way that reduces server virtualization.
Cloud workload security goes deeper into securing the virtual machine, and its performance including infrastructure, software supply chain, system tools, system libraries, and runtime against cyber attacks. It allows for further security for container images, hosts, runtimes, registries, and orchestration platforms.
CWPP provides full visibility into workload and container events. It's impossible to detect, stop or respond to something if it can’t be seen. Once a virtual machine or container is launched, even if the image is configured properly and verified, it can be compromised. CWPPs ensure these machines are protected throughout the software lifecycle of continuous integration/continuous delivery (CI/CD) workflows. As cloud adoption continues to increase, endpoint security solutions will provide more security at the application level.
Security at the Edge: Operational Technology and IoT
Security at the edge is creating another avenue for growth for endpoint security. Operational Technology (OT) is responsible for protecting industrial infrastructure, equipment, and assets. Industrial Control Systems (ICS) comprise systems that are used to control and secure industrial technologies. Ransomware attacks in OT environments are increasing in frequency as ransomware attackers recognize the value of targeting critical infrastructure that holds significant value with low tolerance to downtime risks, including many manufacturing and energy companies. These attackers capitalize on that low tolerance in an effort to more consistently extract ransom payments from victims.
Of all the industrial sectors in 2021, ransomware groups targeted the manufacturing industry more than any other — nearly twice as much as the other industrial groups combined, according to Dragos’ 2021 ICS OT Cybersecurity Year in Review. Even if the exposed OT data is relatively old, the typical life span of cyber-physical systems ranges from twenty to thirty years, resulting in leaks being relevant for reconnaissance efforts for decades—much longer than exposed information on IT infrastructure
IoT Security
According to the 2022 IoT Analytics report, the number of connected IoT devices is expected to grow by 18% to 14.4 billion globally in 2022. The rise in connected devices and sensor technologies is serving to expand the endpoint attack surface for cyber attackers. This has led to organizations demanding better asset visibility and asset control. A 2021 survey of 16K+ IT security professionals found that 80% of IoT applications and 71% of mobile applications are still not tested for vulnerabilities. Key areas of IoT security include penetration testing, end-to-end encryption, digital certificates for device authentication, updates and code signing, agentless device scanning, and IoT network micro-segmentation.
The key tailwind driving IoT security is that IoT devices are being deployed beyond the network perimeter. As a result, traditional endpoint products do not always have visibility over them. IoT devices have been vectors for distributed denial-of-service (DDoS) attacks that have affected major companies in recent years. According to the IDC’s IoT forecast, there will be approximately 42 billion connected devices by 2025, but many of these devices won’t have adequate defenses.
Endpoint companies like Tanium and CrowdStrike have the opportunity to deploy software agents on IoT endpoints, securing all traffic in and out of the devices through security gateways, and aggregating all the IoT data into the cloud or data centers. The key OT security players include Dragos, Claroty, and Tenable.ot, Star Lab, Palitronica Palisade, Armis, Regulus, Bastille, and Karamba Security
Claroty, for example, is an industrial OT security company that helps customers protect, and manage their OT, IoT, and IIoT assets. The company’s platform connects seamlessly with customers’ existing infrastructure and programs while providing a full range of industrial cybersecurity controls for visibility, threat detection, risk, and vulnerability management, and secure remote access—all with a significantly reduced total cost of ownership.
Dragos is another example. Dragos is a threat detection platform within OT security. Dragos is an industrial control system (ICS) that delivers deep visibility into network assets. Key features include network mapping of OT devices, threat detection using behavioral analysis, threat operations service, and incident response. They also have advanced asset discovery and identification, to map industrial assets with a high level of fidelity and distinguish them by a wide variety of attributes specific to an asset type. Dragos primarily provides Industrial Internet of Things (IIOT) services
The Endpoint is the Starting Point
Endpoint security is one of the largest and most fragmented parts of the cybersecurity market. It is usually the entry point for hackers to get into an organization, and has become a critical component of the enterprise. The migration to the cloud has compounded the challenges of endpoint security for organizations while simultaneously improving the technology stack of endpoint security solutions.
Over time, endpoint security technology has evolved from legacy signature-based antivirus into endpoint detection, and eventually became unified as XDR. As a result of how quickly the technology continues to improve, large incumbents like Trend Micro and McAfee have been increasingly unseated, and emerging players like CrowdStrike and SentinelOne are quickly capturing market share from these leading players. This has led to the creation of adjacent markets like cloud workload protection, and Industrial IoT for the endpoint protection industry. Companies that can keep pace with the technology, and how hackers continue to change their tactics, will emerge to be long-term winners in this market.
The next frontier in security? Protecting the cloud. Be sure to subscribe so you don’t miss our next entry in our cybersecurity series, which will dive into cloud and network security.