Thesis
This widespread acceleration in cloud adoption implies that more applications are built on the cloud than ever before. The share of corporate data stored in the cloud continues to grow, with one estimate forecasting that by 2025, over 95% of new digital workloads will be deployed on cloud-native platforms, up from 30% in 2021. Companies must ensure that they are able to monitor and protect their workloads in the cloud.
Security information and event management (SIEM) is one of the key tools that help companies capture data and recognize potential security threats. Traditional SIEM platforms like Splunk, Sumo Logic, and Elastic were built on legacy architecture decades ago before the cloud became mainstream and data grew exponentially. As a result, these platforms have structural issues around high deployment costs, operational overhead, restrictive data types, lack of speed, and inability to scale like modern cloud-native platforms.
Panther is a cloud-native threat detection platform for SIEM. Panther is built on a cloud data lake and runs its compute engine on Snowflake. As a result of its modern architecture, the company has faster deployment times, absorbs a wide variety of data types, and scales more easily on multi-clouds. Traditional SIEM platforms like Splunk can cost over $1 million per year in full deployment, yet they lack many of the functionalities that are needed for a modern SIEM tool. Panther’s product vision is to provide a lower-cost solution that is quicker to deploy.
Founding Story
Panther was founded in 2018 by Jack Naglieri (CEO). Jack was previously the manager of security engineering at Airbnb and Yahoo, where he witnessed firsthand the increasing volume of security data, the challenges of securing a cloud environment and detecting attacks at scale. As Naglieri and his team continued to evaluate SIEM applications, it became clear that no product on the market could manage their requirements.
This compelled Naglieri and his team to create StreamAlert, an open-source real-time data analysis framework addressing flexibility, scale, and cost at Airbnb. While StreamAlert saw adoption by cloud-first security teams, many customers struggled to use StreamAlert’s interface and to manage the overhead of open-source tools. To make StreamAlert more accessible and scalable, Jack set his sights on disrupting legacy SIEM vendors by founding Panther. The company’s goal is to build a platform that could support a wider range of use cases that security teams commonly struggle with.
Product
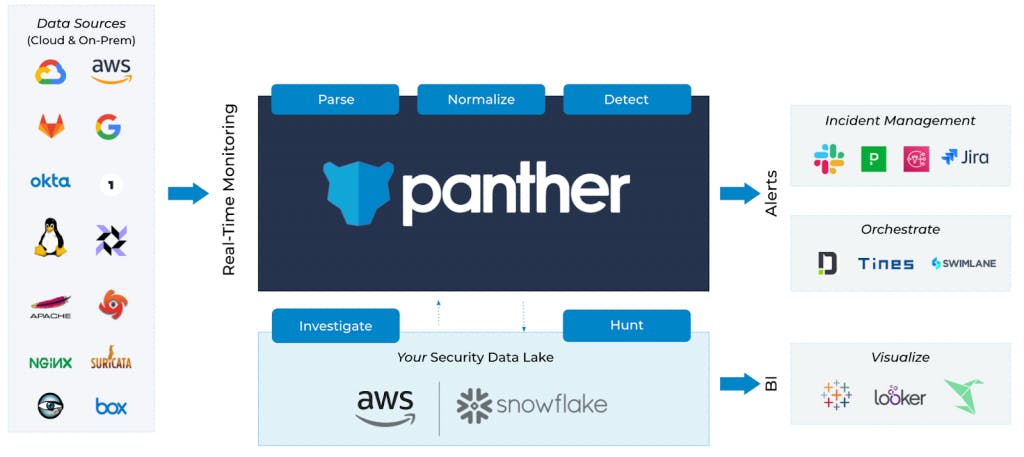
Panther provides tools that centralize, normalize, and analyze security data to enable cybersecurity teams to detect, investigate, and monitor security threats and misconfigurations at scale. As organizations deploy solutions to monitor their security landscape they amass large amounts of security data. Panther’s platform transforms terabytes of raw logs per day into a structured security data lake to power real-time detection, swift incident response, and thorough investigations.
The company’s core product architecture is built on the storage layer of the three major cloud providers. The ability to use Amazon S3 bucket has helped to lower the cost of storing large amounts of data, and allows Panther to focus on its strengths within data analytics. A modern SIEM platform like Panther consolidates the security data across the enterprise and provides analytics and meaningful information to an organization’s security operations center (SOC).
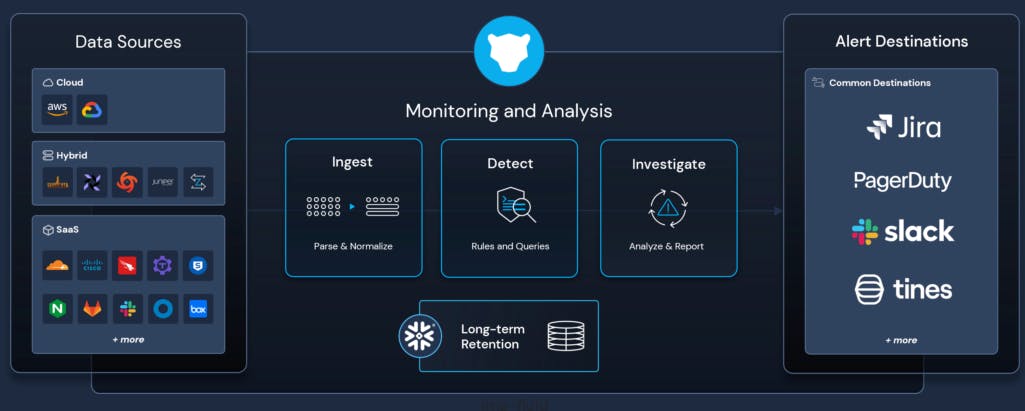
Source: Panther
Data Ingestion
Panther starts by ingesting security data and logs from across a customer’s systems. This can include application usage, cloud storage, security infrastructure, developer tools, or any number of data that could be indicative of security vulnerabilities.
Data Normalization
Once that data is collected, it is parsed into a cloud storage provider like AWS or GCP. Panther will analyze and normalize this raw data into a structure that enables them to write rules and store the information in a data lake. Some of this security data is loaded and stored for long-term retention on Snowflake’s data lake. Customers have the ability to conduct real-time analysis using Python or SQL.
Data Analysis
Once that data is accessible and ready for analytics, a customer’s SOC team can begin automating that process. Panther performs analysis on this data to detect if there is anything suspicious. Panther allows security teams to write code to customize the kinds of information they want to be tracked and alerted on through a process called Detection-as-Code. Panther allows customers to use Python for writing detection rules such as determining how data should be categorized and how the SOC team will receive alerts. If those rules flag different signals, alerts will be sent to the team. The team has the ability to use SQL to analyze the data for future investigations as well.
Panther performs most of this analysis through a core tool built for SOC teams. The underlying foundation of Panther’s product is built around serverless architecture and cloud data storage. Panther has an open security data lake architecture built around Snowflake that decouples compute from storage. This allows organizations to manage and retain large amounts of data for much longer. Companies can also perform highly performant analyses of data. Panther is built to be developer-friendly with a quick start open-source guideline so customers can get started easily.
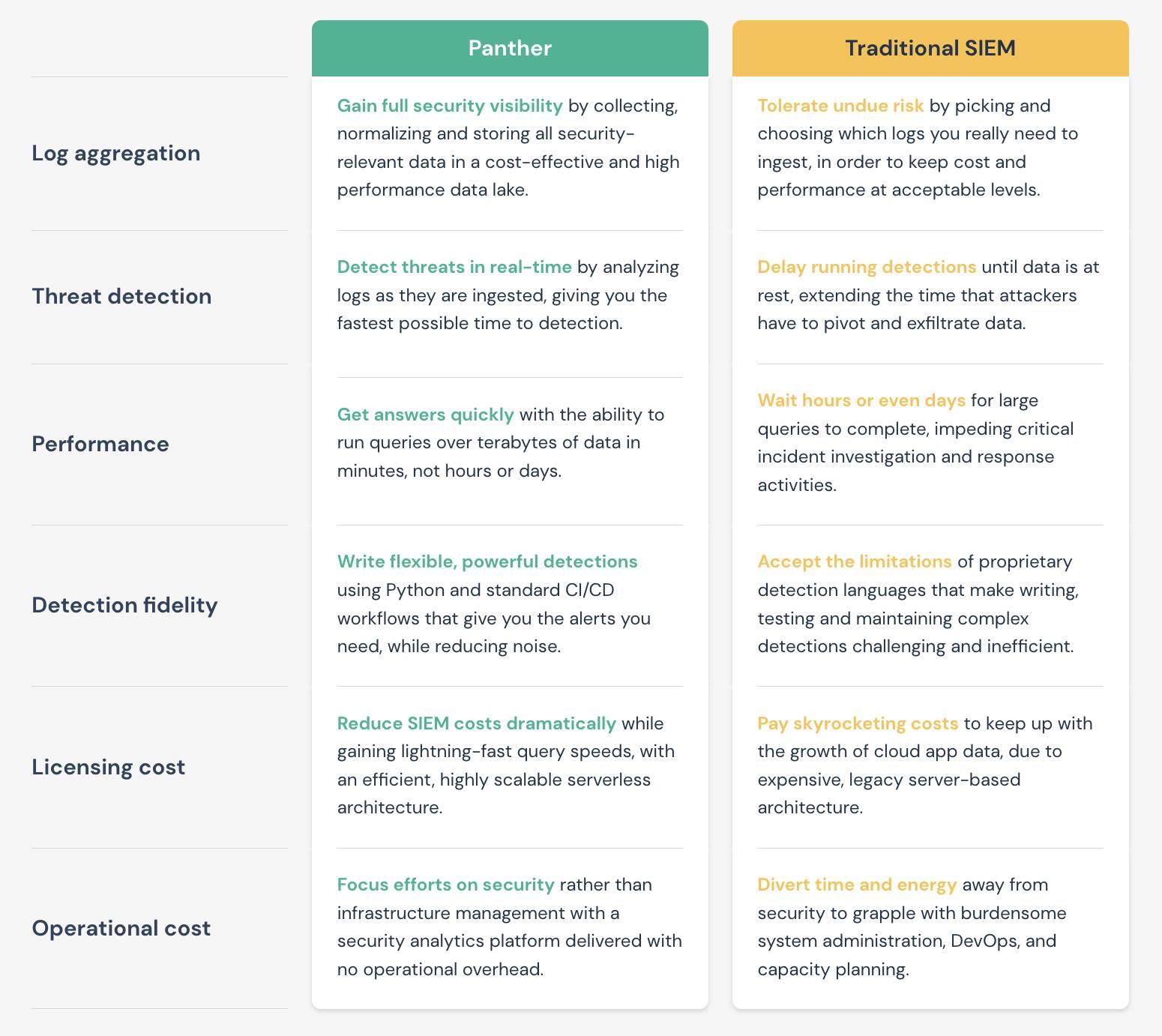
Product Differentiation
Source: Panther
Traditional SIEM architectures have often struggled with providing value from alerts because they aren’t customizable and require specific skill sets to maintain. These tools lack context and actionable data as they are focused on storing aggregated data for compliance reasons and over time become expensive to store and query.
Panther’s key differentiator comes from its open-source tool built around serverless architecture. The product has a self-serve community edition so customers can easily get up to speed on the product using popular technologies like Python to create complex detections, and SQL to perform analytics.
80% of the world’s data will be unstructured by 2025. Unstructured data makes it difficult for teams to search and analyze at scale. As the volume of data in the cloud exploded, Panther built its platform to manage unstructured data at scale. Most security tools leave data normalization for the user to handle, making it difficult for security analysts to understand relationships between malicious indicators and events over time. Panther’s security data lake unlocks enterprises’ security data and provides them with the ability to leverage SQL and Python to query against on a centralized platform.
Source: Panther
Panther’s unified platform ties these features together:
Continuous Monitoring: The product continually receives and analyzes security logs from clouds, networks, and endpoints across an organization.
Analysis: There are over 100+ built-in policies that help security to write Python or SQL to analyze security logs and data.
Notifications: The platform is able to alert teams with actionable messages within existing workflow tools like Jira, Asana, Slack, and PagerDuty.
Automatic Remediation: Panther’s product can automatically correct misconfigured resources.
Flexible Deployment: Panther can be deployed as a stand-alone SaaS application or within your cloud or on Snowflake.
Market
Customer
Panther’s focus is primarily on cloud-native organizations with leaner teams looking to adopt best practices in managing their unstructured security data. Notable customers of Panther as of September 2023 include Dropbox, Gusto, Asana, Snyk, HubSpot, Loom, and Coinbase.

Source: Panther
Market Size
The SIEM market is large and fragmented, estimated to grow from $4.0 billion in 2022 to over $11.6 billion by 2030 (14.5% CAGR 2023-2030). Key drivers include the rise of new data sources coming into the enterprise from new SaaS applications being implemented, Bring your own device (BYOD) policies, and the expanding threat surface that requires more firewalls in the company to be monitored. Existing SIEM platforms revolve around gathering large amounts of data, and as any enterprise grows they generate more data from more applications and use cases. The combination of network firewalls and monitoring systems in the enterprise have led to an explosion of alerts that security teams are trying to manage, often leading to alert fatigue.
Traditional SIEM platforms like Splunk can cost over $1 million per year in full deployment, yet they lack many of the functionalities that are needed for a modern SIEM tool. Traditional SIEM platforms are expensive both in terms of licensing costs and operational burdens on security teams as they require specialized onboarding, time-consuming deployment and fine-tuning, and offer inflexible reporting. Despite the pain, SIEM is still by far the most prevalent technology used for security event management. Over 18% of security practitioners indicated it took more than 12 months to deploy and implement their SIEM solution, and 24% said the biggest challenge with their SIEM platform was receiving too many alerts. 46% said the high cost of a traditional SIEM relative to its capabilities does not align with their organization.
Competition
Panther competes with vendors like Splunk and newer cloud-native players such as Hunters, Elastic, Sumo Logic, and Exabeam. It also indirectly competes against endpoint detection vendors like SentinelOne and Palo Alto Networks Cortex.
Splunk: Splunk was recognized as a leader in the Gartner Magic Quadrant for SIEM in 2022, and had the largest market share in the SIEM space at 22% as of 2020. Despite its prevalence in the market, Splunk has a number of limitations. For one, using Splunk requires knowledge of the Splunk security language which doesn’t give security engineers the ability to write or query its own custom detections. Splunk’s pricing is also a significant concern to users given the linear growth in cost as data volumes grow. Splunk was founded in 2003 and IPOed in 2012. It has a market cap of $21 billion as of September 2023.
Hunters: Hunters is a next-gen solution that also utilizes Snowflake as a customer and partner. Hunters is a vendor positioned as an Extended Detection and Response (XDR) product while Panther is a SIEM. The importance of security analytics and data as Panther’s security data lake concept and ability to visualize actionable data into business intelligence tools like Tableau and Looker are not available to XDR without significant data pipelines and ETL tools. Panther’s key differentiator from Hunters is that it has an open-source component and utilizes an open-source security data lake architecture. It was founded in 2018 and has raised a total of $118.4 million in funding. It raised a $68 million Series C in January 2023 at an undisclosed valuation.
Sumo Logic: Sumo Logic is available for on-premise, multi-cloud, and hybrid cloud, but like Splunk, it uses a proprietary detection syntax. The ease of use and programmability of its querying interface is Sumo’s competitive edge, but due to its cost, users have to make tradeoffs around what to log and for how long as well. Sumo Logic was founded in 2010 and went public in 2020 at a market cap of approximately $2.2 billion before being acquired in 2023 by Francisco Partners at a valuation of $1.7 billion.
Exabeam: Exabeam was founded in 2013. It raised a Series F in June 2021 at a $2.4 billion valuation, bringing its total funding to $391 million. It was also recognized as a leader in the Gartner Magic Quadrant for SIEM in 2022. The company’s product is unique in that they have a product designed for SIEM and XDR. Exabeam has a different pricing model, focused on pricing per user versus Panther’s model of pricing for every data Panther’s platform ingests.
Traction
Panther was named Snowflake’s cybersecurity partner of the year in 2021. Panther has amassed a number of notable cloud-native partners and customers. As of September 2023, notable customers include Coinbase, Dropbox, Gusto, Discord, and Snyk. Panther’s customers grew by 300% year-over-year in 2021.
Valuation
In December 2021, Panther raised a $120 million Series B led by Coatue at a $1.4 billion valuation. As of September 2023, Panther has raised a total of $140.5 million in total funding, including the Series B which was its latest round. Notable investors include Coatue, Lightspeed, ICONIQ Growth, S28 Capital, and Snowflake Ventures
Cybersecurity startups received $4.3 billion in venture funding for the first half of 2023, a 60% drop from the $10.8 billion in the first half of 2022. Panther’s valuation as as of its 2021 Series B was likely elevated, as with many rounds raised from 2020 to 2022. Many cybersecurity startups are facing down rounds or acquisitions in 2023. As a point of reference, Sumo Logic was acquired for $1.7 billion in May 2023.
Key Opportunities
Expanding to Become an XDR Platform
As Panther adds functionality to its platform, it could expand to compete more with XDR providers, which would complement its existing SIEM platform. XDR collects and correlates data across email, endpoints, servers, cloud workloads, and networks to provide more context into advanced threats. These threats can be investigated, and remediated to prevent data loss and security breaches.
Today, Panther is primarily focused on flagging threats and sending them off to SOC teams. These teams have to use a different provider like SentinelOne to prevent malware attacks, for example. However, if Panther could integrate an agent or agent-less solution that is also able to block attacks, respond to threats, and remediate a system once it has been infected with a virus, that would increase their addressable market opportunity.
Evolving into a SOAR Platform
Security Orchestration Automation and Response (SOAR) is the next evolution of SIEMs. These SOAR technologies enable organizations to collect advanced security data from a SIEM platform, and then provide an automated incident response workflow. SOAR platforms scan constantly for threats and provide formalized remediation to vulnerabilities in a work environment.
Panther already helps companies collect security data, but it can take that a step further by helping organizations automate their security processes, policies, and configuration when responding to threats. As enterprises continue to increase their spending on security solutions they’re looking for comprehensive security visibility, Panther has an opportunity to create additional features that incorporate more orchestration and integration between security products.
Key Risks
SIEM vs. XDR
SIEM, as a threat detection standard, is being contested by companies offering XDR like SentinelOne. XDR provides behavioral analytics and network intelligence. XDR differentiates itself from SIEM by requiring very little code while still providing analytics and a unified single pane monitoring the security stack.
The SIEM market is in flux as XDR vendors like SentinelOne and Crowdstrike start to offer integrated automated incident response software, posing direct challenges to SIEM vendors. XDR can extend SIEM by tapping into SIEM data and combining it with data from other point solutions, like Okta, that integrate with the XDR platform. A critical question for CTOs will be whether they need SIEM if they’ve already adopted an XDR solution.
Vendor / Partner Lock-in
Panther was released exclusively to AWS customers, added support for Google Cloud in early 2022, and only began support for Microsoft Azure in Q4 2022. Panther’s security data lake technology is built on Snowflake and is dependent on its platform. However, Snowflake uses Hunters for their internal use cases. Panther has expanded its integration ecosystem at the application layer, but it will have to continue to expand to support Azure and Kubernetes workloads.
Established Competition
Competition is fierce in the SIEM market. Most vendors are differentiated by specific use cases (cloud vs. on-premise, data volumes, and specific workloads). Panther’s focus is primarily on cloud-native organizations with leaner teams looking to adopt best practices in managing their unstructured security data. While Panther is cost-effective in terms of resources and management costs, it is likely not as strong a fit for larger organizations with hybrid or on-premise environments.
Summary
Traditional SIEM tools were thought of as a check-the-box security measure to manage their security alerts. But as data volumes and alerts have exploded the industry has noted a shortage of security professionals. As a result, modern SIEM platforms like Panther are attempting to better manage the security landscape. The tools enterprises are deploying in their SOCs are fragmented, and typically not optimized for the amount of enterprise data. The average large enterprise can sometimes spend as much as $6 million a year managing its security operations from staffing to implementing new technologies. Panther is focused on becoming a central player in those systems.