Thesis
Enterprise infrastructure is breaking under its own weight. The shift to hybrid work, cloud-native applications, and bring-your-own-device (BYOD) policies has dissolved the traditional network perimeter. As of 2025, 78% of employers anticipate hybrid arrangements becoming permanent by 2026. Meanwhile, 90% of organizations are projected to adopt hybrid cloud strategies by 2027, forcing IT and security teams to manage access, performance, and threat surfaces across a growing sprawl of devices, applications, and geographies.
At the same time, security architectures have become deeply fragmented. In 2025, enterprises managed an average of 83 security tools from 29 vendors. Many teams faced alert fatigue, policy conflicts, and visibility gaps across systems. Fragmented security is no longer just inefficient; it’s dangerous. For example, one former employee of Cash App, a mobile payment service, retained access credentials to Cash App even after termination. Months later, the employee exfiltrated brokerage data from over 8 million customers. The company failed to detect the breach for four months, triggering a class-action lawsuit. That failure wasn’t caused by a zero-day exploit, but rather by an inability to centrally revoke access and monitor user activity across systems.
These conditions are accelerating the shift to Secure Access Service Edge (SASE), a cloud-delivered architecture that combines networking and security functions. SASE relies on Software Defined Wide Area Networking (SD-WAN), which uses software to manage and route traffic across multiple connections to improve performance and reliability. The platform also integrates firewall as a service, secure web gateways, and zero-trust access into a single solution. In 2025, 54% of adopters reported stronger security, 52% reported easier management, and nearly half reported better performance and cost reduction as benefits of switching to SASE. Single-vendor deployments are expected to account for 90% of the market by 2029. In many enterprises, enforcing something as basic as a user access policy still requires stitching together a dozen systems, introducing delays, blind spots, and opportunities for breach.
Cato, also known as Cato Networks, was purpose-built to eliminate complexity in network security. Its cloud-native platform unifies networking and security into a single software layer. It’s delivered through more than 80 globally distributed points of presence (PoPs) connected via Tier-1 carriers, as of 2025. Unlike vendors that rely on the public internet, Cato operates its own global backbone, ensuring consistent policy enforcement, low latency, and real-time scalability across users, offices, and cloud workloads. Enterprises can replace legacy tools like VPNs, firewalls, and SD-WAN appliances with a unified control plane. In an environment where every additional tool adds operational friction and risk, Cato functions as a managed backbone for the modern enterprise, re-architecting the internet around security rather than adapting security to the internet.
Founding Story

Source: Calcalist
Cato was founded in 2015 by Shlomo Kramer (CEO) and Gur Shatz (former COO and CTO, now board member). The two Israeli cybersecurity entrepreneurs shared a belief that enterprise networks were overdue for change and had experienced challenges with existing networks firsthand.
Kramer, also known as the “Godfather of Cybersecurity”, had already helped define two eras of security infrastructure. After completing degrees in mathematics and computer science at the Hebrew University of Jerusalem, he served in the Israeli army intelligence, where he met Gil Shwed, with whom he co-founded Check Point Software Technologies in 1993. Check Point’s first firewall, shipped on a floppy disk, was one of the earliest commercial products to define and enforce security policy at the network edge. Kramer went on to co-found Imperva in 2002 to protect application and data layers. By the time Cato was conceived, he had also backed firms like Trusteer and Gong, and served six years on Palo Alto’s board as it scaled into billions in revenue.
Prior to beginning his career, Shatz graduated from Tel Aviv College with a degree in computer science. He went on to work under Kramer at Imperva as VP of engineering and director of product development before co-founding Incapsula, a cloud-based security and web acceleration company. His experience building a distributed, high-performance cloud edge made him deeply familiar with the operational tradeoffs involved. Incapsula was acquired in 2014, and Shatz walked away realizing that scaling had required layer upon layer of compensating complexity.
In early 2015, the pair began brainstorming ideas for their next project. At the time, few believed that cloud-native architectures could deliver both enterprise-grade security and carrier-grade availability. The dominant belief among incumbents was that telecommunication companies (telcos) would drive the transition to software-defined networking through Network Function Virtualization (NFV): a stopgap approach built on legacy infrastructure. Kramer and Shatz quietly bet against this consensus, believing NFV was a transitional idea that would fail to meet the demands of globally distributed workforces, SaaS adoption, and zero-trust security models. From day one, that contrarian bet shaped the architecture of this next project: a global private backbone, single-pass security engine, and control over the full data and control planes.
Rather than pitch investors or chase a prototype, they focused first on validation. They hired a research firm to run interviews with enterprise IT leaders, deployed sales teams with slide decks, and tested early messaging through what Shatz described as a “non-refutable presentation.” These probes confirmed that IT leaders wanted simplicity, control, and global reach, but were not finding it in the incumbent stack.
What followed was one of the more difficult builds of Kramer’s career. Delivering converged networking and security over a private global backbone required not just rethinking system architecture but delivering the performance of a telecom-grade network while handling live, sensitive traffic. Shatz pushed for a culture of operational rigor, where every production issue became a design input and every failure a feedback loop. When Gartner formally defined the category, Secure Access Service Edge (SASE), in 2019, it largely described what Cato had already built.
The team scaled gradually. In 2017, Tomer Wald joined as CFO, and Alon Alter, who had helped scale Incapsula’s revenue from $1 million to tens of millions, became Chief Business Officer. In 2025, Karl Soderlund was brought in as Global Channel Chief after leading partner expansion at Zscaler and Palo Alto Networks. Shatz stepped away from day-to-day operations in 2023 but continues to serve on the board.
The company continues to pursue its founding ambition to become, in Kramer’s words, “the AWS of IT security.” The name Cato, inspired by the Pink Panther character Cato Fong, who kept Inspector Clouseau on alert, reflects that vision: a cloud-native platform designed to help enterprises stay ready, responsive, and secure.
Product
The Rise of SASE
The modern enterprise network began with a simple structure: local area networks (LANs) confined to individual offices. As businesses expanded across geographies, these isolated systems needed to communicate, giving rise to wide area networks (WANs). In the 1990s and early 2000s, enterprises built WANs through international private leased circuits or relied on telecommunications carriers to provision dedicated point-to-point infrastructure. Telcos such as Verizon, Cisco, and AT&T dominated this era, delivering connectivity via Multiprotocol Label Switching (MPLS). MPLS offered high availability and centralized routing control. It was tailored for a hub-and-spoke world where branch offices accessed applications in centralized data centers. However, MPLS was rigid and slow to deploy, making it ill-suited to handle cloud adoption, remote work, or traffic destined for SaaS applications.
In the 2010s, as SaaS became a foundational part of enterprise IT and users began working beyond the branch, the shortcomings of MPLS became glaring. Routing traffic from remote locations back to headquarters for security inspection introduced latency and eroded user experience. The response was Software Defined Wide Area Networking (SD-WAN), which decoupled routing from physical circuits. It enabled organizations to combine broadband, LTE, and MPLS links and manage them through software-defined policies. This phase was led by startups such as Viptela, CloudGenix, and Silver Peak, each bringing innovative overlay architectures that gave enterprises agility without relying on telco provisioning. As adoption increased, these pioneers were acquired by legacy vendors. Cisco acquired Viptela, Palo Alto Networks acquired CloudGenix, and HPE acquired Silver Peak. This marked the transition of SD-WAN from disruptive upstart to enterprise staple.
Despite this progress, SD-WAN remained incomplete. It solved for transport optimization but left security fragmented. Enterprises still needed to cobble together a mix of firewalls, VPNs, secure web gateways (SWGs), and cloud access security brokers (CASBs) to protect traffic, resulting in architectural sprawl and operational overhead. This fragmentation became a critical bottleneck during the COVID-19 pandemic, when remote work surged and centralized architectures such as MPLS and VPNs buckled under the strain.
In 2019, Gartner introduced Secure Access Service Edge (SASE) as a blueprint for rethinking enterprise infrastructure. SASE collapsed networking and security into a single cloud-delivered platform. It integrated SD-WAN, zero trust network access (ZTNA), SWG, CASB, firewall-as-a-service (FWaaS), and policy enforcement into a unified system designed for a perimeter-less world.
In the SASE era, vendors have taken markedly different approaches. Zscaler took a proxy-first approach, routing all traffic through its global inspection nodes to enforce access policies in the cloud. Palo Alto Networks pursued a portfolio strategy, acquiring point solutions such as CloudGenix for SD-WAN and layering them with its existing firewall and cloud security products under the Prisma brand. Fortinet leaned into its hardware roots, delivering high-performance edge security via application-specific integrated circuits optimized for branch deployment.
These divergences in architecture matter. While legacy players have tried to retrofit cloud-native capabilities onto on-prem architectures or integrate acquired assets, Cato was built for convergence from the start. Just as ERP systems evolved from monolithic on-prem software to cloud-native platforms that now incorporate AI and real-time orchestration, SASE represents a similar shift in enterprise networking. As identity becomes the new perimeter and IT teams seek programmable control over performance and security, the market is coalescing around full-stack platforms rather than fragmented portfolios. In this context, SASE is not merely the next step beyond SD-WAN. It is the foundation for a distributed, policy-driven, secure infrastructure model.
Cato SASE Cloud Platform Overview
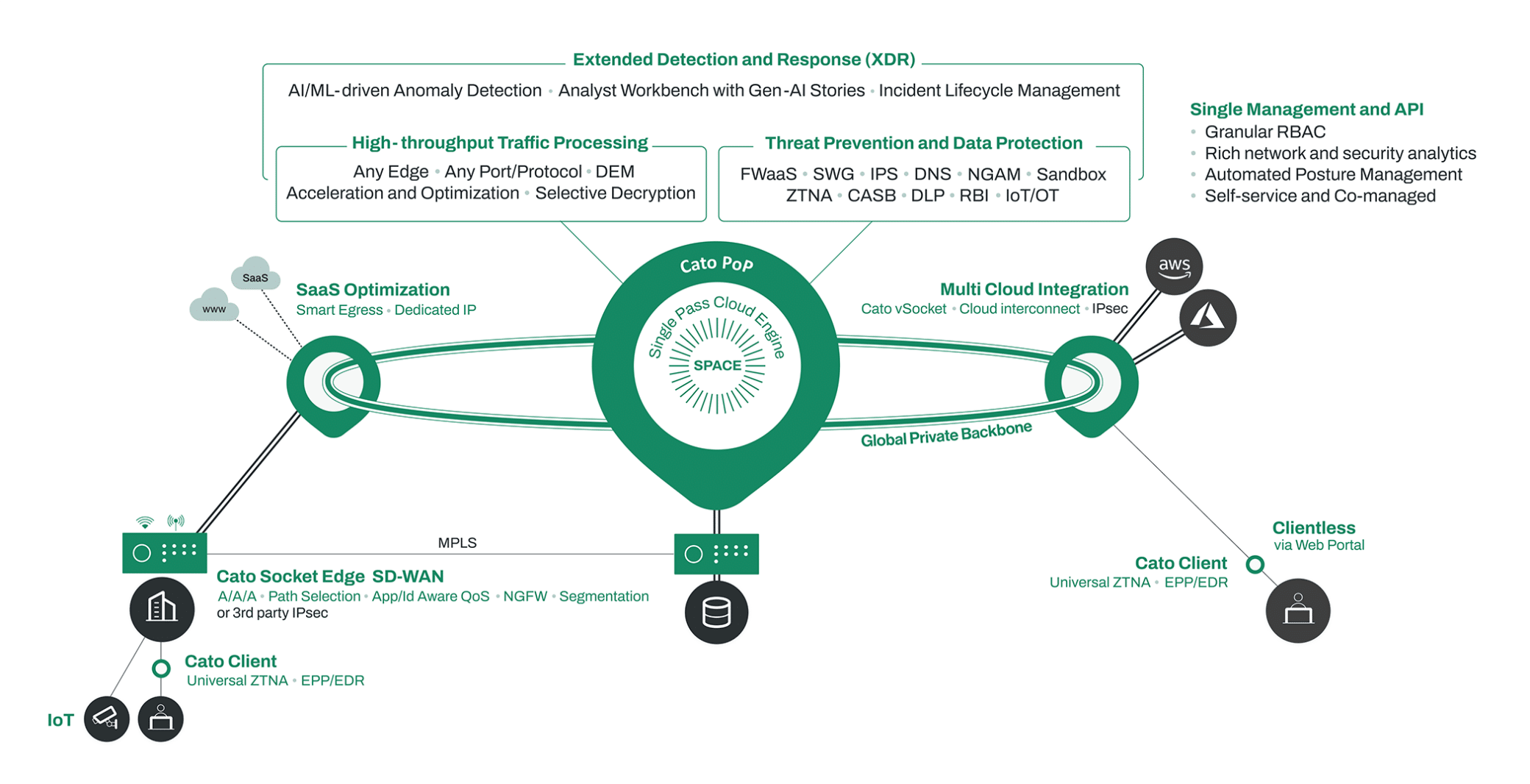
Source: Cato Networks
Cato Networks delivers a SASE platform that replaces the complexity and fragmentation of legacy IT infrastructure with a unified, cloud-delivered architecture, which Cato calls flexible, resilient, and globally distributed.
Platform Architecture
Core Components
At the heart of the platform is the Single Pass Cloud Engine (SPACE), an inspection engine that processes traffic just once to enforce all security policies. SPACE is the customs checkpoint of Cato’s network: a single, intelligent gate where every packet is evaluated and tagged for safety, priority, and destination. This eliminates the latency and management burden of chaining together tools like firewalls, malware gateways, and ZTNA proxies. All decisions are made in a single analytical pass, with enriched context from device, identity, and application metadata.
All data flows through Cato’s Global SASE Cloud Backbone, a private network of Points of Presence, built on bare-metal infrastructure and tightly integrated with Tier-1 ISPs. Unlike cloud networks riding on shared highways, Cato owns the roads and optimizes the routes in real time.
Design Principles
Cato’s platform is structured around principles designed to solve persistent enterprise IT pain points:
360-Degree Visibility & Control: Legacy security stacks leave gaps between remote users, cloud apps, and branch firewalls. Cato replaces those blind spots with a single layer of inspection and logging.
Autonomous Platform Lifecycle: Software updates are deployed across all edges - cloud, client, and appliance, without patches, version checks, or reboot windows.
Automated Security Posture Management: The system detects path degradation, traffic congestion, or service outages in real time and reroutes traffic instantly.
Flexible & Gradual Deployment: Adding new locations or users requires no hardware shipment or on-site expertise. Provisioning is zero-touch, and remote sites can be live within minutes via Cato Sockets or Clients.
AI and Machine Learning

Source: Cato Networks
Cato embeds machine learning across its platform to eliminate repetitive security and operations tasks. Hundreds of threat intelligence feeds are ingested and scored every two hours. Suspect indicators of compromise (IoCs) are tested in safe environments, ranked by correlation and freshness.
Pattern-agnostic detection engines evaluate new domains and traffic flows using statistical modeling. This enables Cato to stop threats that haven’t been seen before, including fileless attacks and polymorphic malware. The platform also identifies rogue SaaS use or unmanaged devices by behavioral fingerprinting. Meanwhile, machine learning flags infrastructure anomalies like PoP degradation or excessive retransmits, enabling automated failover and route correction.
Platform Capabilities
Connection
Source: Cato Networks
Cato’s connection capabilities begin with its global private backbone, a secure, service-level agreement (SLA)-backed network. All enterprise traffic, whether from offices, remote workers, cloud workloads, or data centers, is encrypted and routed through this backbone.
The backbone continuously optimizes traffic paths based on real-time network conditions such as latency, jitter, and packet loss. Performance-sensitive applications like Voice over Internet Protocol (VoIP), video conferencing, and enterprise resource planning (ERP) benefit most, especially when routed through the PoP closest to the cloud service in use.
Digital Experience Monitoring (DEM) adds visibility into how applications perform across locations, devices, and network paths. By monitoring performance continuously without additional software agents, IT can detect and address issues proactively.
Cato’s edge device, the Cato Socket, links office locations to its network using any available internet connection, such as fiber or 4G/5G. It keeps connections reliable by automatically switching between paths if one goes down, copying data packets on unstable connections to prevent loss, and routing traffic based on the specific needs of each application. Many organizations use the Socket to replace MPLS circuits, combining multiple internet links to increase bandwidth and resilience while reducing cost and complexity.
For example, Forvis replaced costly, complex MPLS infrastructure with Cato’s cloud-native backbone and SD-WAN. The result was operational efficiency, scalability, and consistency across global locations, critical during its merger of Dixon Hughes Goodman and BKD. Remote access was rapidly deployed to 5.4K staff using Cato Sockets and secure clientless access, supporting hybrid work and minimizing M&A friction.
In public cloud environments, Cato offers vSocket, a virtual instance of the same edge functionality. It integrates workloads in Amazon Web Services (AWS), Microsoft Azure, and Google Cloud directly into the Cato network, improving cloud performance by avoiding unnecessary backhaul through on-premises infrastructure.
For remote and hybrid workers, Cato provides a lightweight, cross-platform client that enforces enterprise security policies through the nearest PoP. Alternatively, a browser-based portal enables secure access for unmanaged or third-party devices with no installation. This flexibility allows teams to quickly connect new users or temporary collaborators without compromising visibility or control.
Organizations that maintain existing firewalls or routers can connect them to the platform using Internet Protocol Security (IPSec) tunnels. This allows for phased transitions, particularly in newly acquired locations or legacy environments, without requiring immediate hardware replacement.
Protect
Source: Cato Networks
Cato’s security stack consolidates multiple enforcement layers, including firewalling, SWG, ZTNA, anti-malware, data loss prevention (DLP), cloud access security broker (CASB), and more, into a single inspection engine.
Traffic policies are enforced in real time by SPACE, which continuously inspects traffic flows across identity, content, device, and behavior. Web hygiene is handled by the SWG and domain name system (DNS) filtering layers, which block phishing domains, risky content, and malware delivery attempts. The intrusion prevention system (IPS) and next-gen anti-malware engines use heuristics and threat intelligence to stop lateral movement and payloads, including zero-day threats.
To reduce the risk of attacks from unmanaged or contractor devices, Cato uses Remote Browser Isolation (RBI), which opens web sessions in a secure cloud environment instead of on the user’s device. For SaaS applications, its built-in CASB tracks the use of unsanctioned apps and applies specific controls to each one. Meanwhile, DLP scans content to stop sensitive data from being leaked across cloud apps, employee devices, and BYOD environments. Policy configuration is centralized in the Cato Management Application and applied uniformly.
Detection

Source: Cato Networks
Cato detects threats by analyzing signals from the network, endpoints, and external tools like Microsoft Defender for Endpoint. These are funneled into a central data lake, where machine learning models flag anomalies in user behavior, device posture, and traffic patterns.
At the heart of this process is Cato’s Extended Detection and Response (XDR) engine. It surfaces high-fidelity incidents early, often before a threat escalates into compromise. Instead of delivering raw alerts, Cato generates structured “incident stories” that identify what happened, which systems were impacted, and what remediation steps are needed. These narratives are accessible through a built-in analyst workbench, where security teams can inspect timelines, raw events, and suggested next actions.
Because all traffic is inspected by default and telemetry is captured across user locations, new offices or remote users automatically benefit from the same level of threat visibility, without requiring additional configuration or agent deployment.
Organizations without a full security operations center can offload detection and response to Cato’s Managed XDR (MXDR) service. This provides 24/7 monitoring, threat triage, and actionable remediation from Cato or certified partners.
Run
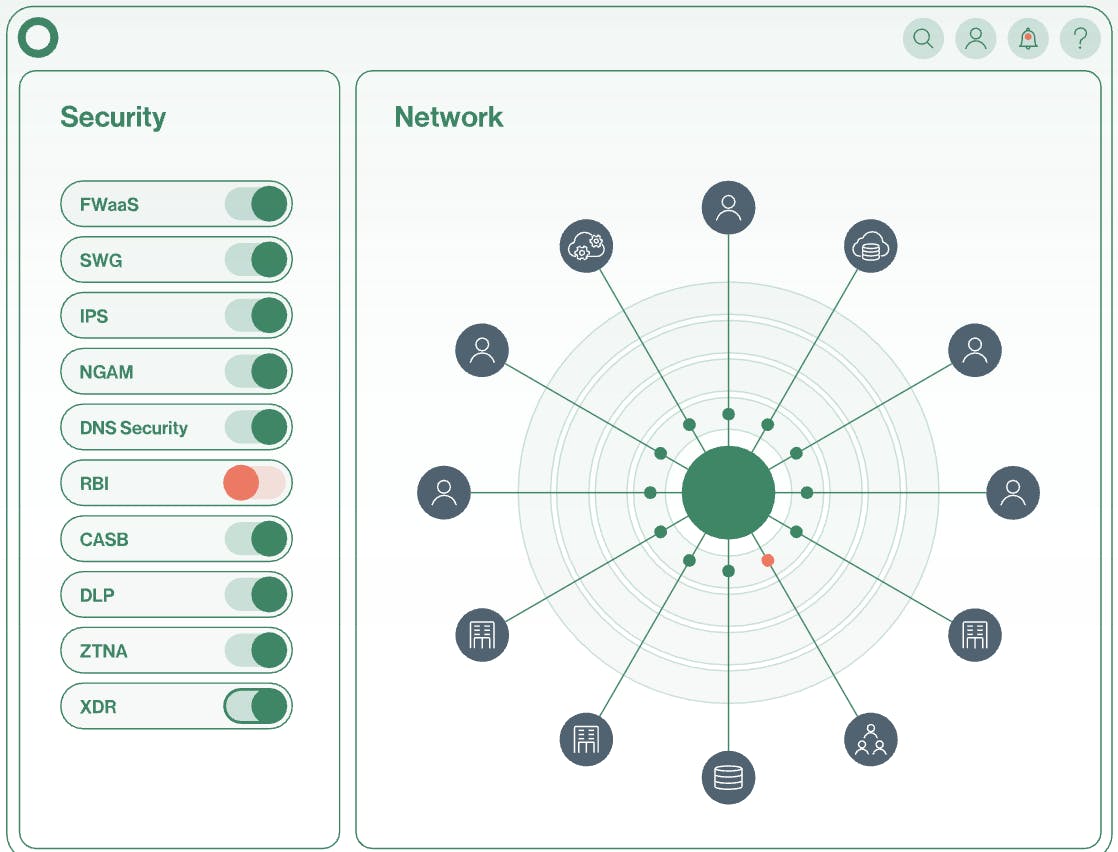
Source: Cato Networks
Cato centralizes network and security operations in the Cato Management Application, a single-pane-of-glass interface where administrators configure policies, monitor performance, and investigate security events in real time. Dashboards are customizable, and all system data, from endpoint to cloud, is accessible through one UI.
Cato also exposes a universal API for workflow automation and system integration. Teams can ingest Cato telemetry into SIEM tools like Splunk, auto-generate tickets in systems like ServiceNow or Jira, and programmatically provision users, sites, and policies. Formal integrations are available for identity providers, endpoint tools, and IT service platforms.
Market
Customer
Cato Networks serves both mid-market and enterprise organizations across industries where IT environments are globally distributed, regulatory requirements are high, and legacy architectures struggle to keep pace with modern workloads. Its customer base spans financial services, healthcare, manufacturing, retail, and technology services.
Financial Services: Cato helps financial institutions enforce security policies across distributed offices and remote employees, while meeting industry-specific compliance requirements like PCI and GDPR. The platform supports identity-based access, encrypted traffic inspection, and centralized control, making it easier to audit and manage risk across multiple jurisdictions.
Healthcare: Cato enables healthcare providers to securely connect hundreds of clinical sites, often with no on-site IT staff. It supports HIPAA compliance while improving access to cloud-hosted applications and telehealth platforms. Fullerton Health used Cato to unify over 550 locations across nine countries.
Manufacturing: Cato supports manufacturers navigating M&A activity, global supply chains, and hybrid workforces. The platform accelerates site integration, improves visibility across regions, and reduces dependence on MPLS or vendor-specific hardware. Element Solutions Inc. adopted Cato to reduce integration timelines and shift IT resources to higher-leverage work.
Retail: Retailers use Cato to manage connectivity across distributed stores, data centers, and e-commerce operations. The platform provides real-time visibility, secure partner onboarding, and centralized network policy enforcement. Its lightweight deployment model makes it well suited for small-footprint retail sites.
Technology Services: IT and Business Process Outsourcing (BPO) providers use Cato to improve performance for voice and collaboration tools used by remote agents. The platform’s global private backbone and traffic optimization tools help meet SLAs, particularly in latency-sensitive environments. Inspiro used Cato to address chronic VoIP and latency issues across its call centers.
Market Size
Cato operates in the SASE market, which integrates networking (SD-WAN) and security (Security Service Edge, or SSE). The global SASE market is projected to grow from $12.9 billion in 2025 to $32.6 billion by 2030, reflecting a CAGR of 20.3%. Growth is fueled by hybrid work, cloud migration, and regulatory pressure for unified security frameworks. By 2028, 50% of new SASE deployments are expected to come from single-vendor platforms, up from 25% in 2024.
Large enterprises account for roughly 65% of current SASE spend, but small and midsize businesses represent the fastest-growing segment, expanding at a 29% CAGR versus a global average of 20%. Cato’s footprint reflects this dual demand, with customers across the U.S., Europe, Israel, and emerging markets in Asia-Pacific and Latin America.
Competition
Competitive Landscape
The SASE market is comprised of both established businesses and newer enterprises. Zscaler leads with 21% of total market share and 34% of the Security Service Edge (SSE) segment. Cisco, Palo Alto Networks, Broadcom, Fortinet, and Netskope round out the top six, together accounting for 72% of market share.
These vendors dominate through bundled portfolios sold into existing enterprise relationships. But their architectures, assembled through acquisition, introduce latency, operational complexity, and inconsistent policy enforcement. Security data often lives in silos. Networking runs over public cloud infrastructure, adding cost and degrading performance.
Built from the ground up, Cato offers a single data and policy layer, optimized for hybrid work, secure remote access, and global site-to-site networking. As the market splits between stitched portfolios and purpose-built platforms, Cato is betting the latter will define SASE’s future.
Competitors
Versa Networks
Founded in 2012, Versa Networks offers a SASE platform designed to support flexible deployment models: cloud-hosted, on-premise, or hybrid. The company combines networking and security into a single architecture, providing SD-WAN, ZTNA, SWG, FWaaS, and analytics. Versa is particularly focused on enabling telecom and service providers to build managed offerings. Versa has raised $316.3 million as of July 2025, including a $120 million Series E led by BlackRock. Other investors include Sequoia Capital and Artis Ventures. The company was valued at $875 million as of its funding round in 2022.
Versa offers more control and multi-tenancy than Cato, recently launching Sovereign SASE, which allows customers to host the SASE stack on their own infrastructure for regulatory compliance. While this flexibility appeals to governments and telecoms, it adds complexity. Cato instead runs a global, single-vendor cloud-native backbone with uniform software at every PoP, enabling faster setup and more consistent performance across enterprise environments.
Zscaler
Founded in 2007 by Jay Chaudhry and K. Kailas, Zscaler is a publicly traded cloud security company built around the Zero Trust model. Its core product, the Zero Trust Exchange, enables secure access between users and applications without relying on a traditional perimeter. Zscaler focuses on SSE functions, including SWG, CASB, and ZTNA. The company raised $171 million before its 2018 IPO, including a $110 million Series B led by TPG Growth. Other investors included Lightspeed Venture Partners. As of July 2025, Zscaler has a market cap of $47 billion.
Compared to Cato Networks, Zscaler operates through public cloud points of presence and focuses heavily on security features. Recent product releases, such as AI-powered app segmentation, highlight Zscaler’s commitment to eliminating lateral movement and securing B2B communications. Cato, by contrast, focuses on full-stack SASE, pairing orchestration and networking maturity with a unified architecture.
Palo Alto Networks
Palo Alto Networks, founded in 2005 by Nir Zuk, is one of the largest cybersecurity firms globally. Its SASE offering, Prisma Access, is part of a broader portfolio of security offerings including next-generation firewalls (NGFWs), the Prisma Cloud platform, and the Cortex suite for AI-driven threat detection and security operations. As of July 2025, PANW has raised $65 million from investors like Icon Ventures, Sequoia Capital, Lehman Holdings, and Greylock before its IPO. It now trades at a market cap of $132 billion.
Palo Alto is an example of what Cato calls “portfolio-ization”, bundling multiple acquisitions under one brand rather than building a unified architecture. PANW relies on public cloud partners (e.g., Google Cloud) for Prisma’s scalability. It’s April 2025, AI Runtime Security update extends automated threat detection across its suite, but reinforces the modular nature of its product strategy. Cato aims to differentiate by eliminating integration complexity across SD-WAN, SSE, and routing in a single-pass architecture.
Cisco
Founded in 1984 by Stanford engineers Sandy Lerner and Leonard Bosack, Cisco built its reputation as the dominant provider of enterprise networking equipment. It now offers SASE capabilities through Cisco Umbrella and Cisco Secure Access, layered on top of its extensive hardware footprint and SD-WAN offerings (e.g., Catalyst SD-WAN). Cisco has raised $2.5 million as of 2025, with backing from investors such as Kleiner Perkins and Western Technology Investment. It holds a market cap of $217 billion as of April 2025.
Cisco is retrofitting its installed base for SASE compatibility, notably through its Catalyst SD-WAN + Secure Access integration, introduced in February 2025. This hybrid approach supports customers with on-premise needs who are not ready for a full cloud transition. Cato takes a different approach — in March 2025, it launched a cloud-based LAN firewall designed to segment office networks without requiring physical appliances or manual software updates.
Business Model
Cato Networks earns revenue primarily through subscriptions priced by user count and bandwidth needs. It charges service revenue from implementation, support, and training. While pricing is not publicly disclosed, unverified sources suggest pricing models range from per-user and bandwidth-based tiers to flat enterprise-wide plans and usage-based billing for variable workloads.
Cato manages a proprietary cloud-native backbone anchored by over 80 PoPs worldwide as of 2025, which translates into higher capital and operational expenditures to maintain global performance and reliability standards.
Additional cost centers include R&D investments to support unified networking and security innovation, such as efforts from Cato's in-house Cyber Threats Research Lab (Cato CTRL). Sales and marketing expenses may also be significant, with resources devoted to building out a channel-driven go-to-market strategy through Managed Service Providers (MSPs) and Value-Added Resellers (VARs).
Over the long term, Cato’s structural cost base will continue to be shaped by three primary forces: expanding its PoP footprint to meet enterprise demand across new geographies, ongoing product development to remain competitive in the SASE category, and partner enablement programs designed to support its indirect sales model.
Traction
Cato Networks has demonstrated sustained growth across customer count, revenue, and partner engagement since its early commercial years. In 2019, the company recorded a 220% year-over-year increase in bookings, supporting an installed base of over 450 enterprise customers. By 2021, its valuation doubled to $2.5 billion following nearly 100% revenue growth, with deployments expanding to over 1.1K organizations managing 300K remote users. This momentum was reinforced by a 92% increase in deal registrations and a 41% rise in contributing channel partners.
Adoption accelerated into 2022. Cato surpassed $100 million in ARR, grew to 1.6K enterprise customers, and expanded its footprint to 520K ZTNA users across more than 150 countries. That year saw a 70% jump in registered new customer deals and the addition of Porsche Motorsport as a notable partner.
By 2023, Cato exceeded 2.2K enterprise customers, with large enterprise adoption outpacing overall growth. Its revenue increased by 59%, with new customers including Carlsberg Group, Häfele, and the Porsche Formula E team. It was also recognized as a Challenger in the Gartner Magic Quadrant.
In 2024, Cato’s ARR surpassed $250 million with 46% YoY growth and a customer base exceeding 2.5K enterprises. Key customers include O-I Glass and Vitesco Technologies. It launched the MSASE Partner Platform and expanded its network via a partnership with e& in the UAE. As of early 2025, Cato has deepened its go-to-market motion through a strategic collaboration with Spectrotel to deliver managed SASE services.
In mid-2025, Cato raised a $359 million Series G, and a third of the round (~$120 million) was secondary, providing long-time employees liquidity and preserving the company’s runway. While Cato has postponed its anticipated IPO beyond 2025, it continues to strengthen its board, adding Eyal Waldman (founder, Mellanox) and Gili Iohan (partner at ION, former CFO of cyber firm Veronis).
Valuation
Cato Networks has raised $1.1 billion across multiple venture rounds since its founding, including a $359 million Series G round in mid-2025. That round brought the company’s valuation to over $4.8 billion. The Series G round was led by ION Crossover Partners and Vitruvian Partners, with participation from Lightspeed Venture Partners, Adams Street Partners, and Acrew Capital. Previous backers include SoftBank Vision Fund 2, Greylock, Swisscom Ventures, Singtel Innov8, and Sixty Degree Capital.
Cato’s fundraising trajectory stands out against the backdrop of a tightening cybersecurity investment market. In 2023, total cybersecurity VC funding fell to $8.7 billion despite a 14% increase in deal volume. Cato was one of the few companies, alongside SandboxAQ, Wiz, and Netskope, to raise among the largest rounds that year.
Key Opportunities
Enterprise IT Consolidation is Driving SASE Standardization
Enterprise buyers are reaching a breaking point with fragmented network and security stacks. Managing multiple point solutions across firewalls, VPNs, SD-WANs, and CASBs introduces operational overhead and inconsistent policy enforcement. Increasingly, organizations are turning to SASE architectures to converge networking and security into a single platform.
This shift has been driven by the need for agility, adaptability, and resilience in order to support distributed workforces and evolving threat landscapes. Industry-wide, analyst reports and telco RFPs suggest that SASE has approached a “tipping point” in enterprise adoption. SASE’s trajectory has been similar to that of other platform transitions, such as server virtualization or public cloud.
Already, 60% of enterprises are expected to phase out MPLS by 2025 in favor of SD-WAN and SASE alternatives. As this change accelerates, especially among Fortune 1000 companies, Cato stands to benefit from the infrastructure refresh cycle that favors cloud-native platforms over legacy hardware.
Telco Distribution as a Force Multiplier
SASE adoption has increasingly been driven through managed service channels. Telecom operators and global MSPs are embedding SASE into their portfolios to meet enterprise demand for fully managed connectivity and security. This creates a significant distribution opportunity for Cato.
Major providers like Windstream, Horizon Telecom, and e& in the UAE have already partnered with Cato to deploy and operate SASE infrastructure in-region. Others, like AireSpring, resell Cato’s services in over 190 countries. These partnerships let carriers provide managed underlay connectivity and layer Cato’s SASE on top, giving them a competitive alternative to bundling services from fragmented vendors.
If additional global carriers such as AT&T or BT adopt Cato as their default SASE vendor, Cato could benefit from significantly accelerated go-to-market motion via carrier-standardized deployments. Cato’s MSASE Partner Platform allows partners full control over licensing and billing, aligning channel incentives with Cato’s recurring revenue model.
Regulatory Tailwinds and the Rise of Sovereign SASE
Cross-border data regulations are putting pressure on multinational enterprises to localize their traffic and comply with data residency laws. Legislation such as the GDPR and other sovereign data frameworks is pushing network and security teams to ensure where traffic is inspected and stored.
SASE platforms are uniquely equipped to address this shift. Cato’s global private backbone and distributed cloud-native PoPs allow enterprises to steer traffic through specific jurisdictions and enforce unified policies, including network-level data loss prevention and access controls. Its deployment of localized instances, such as the UAE node launched with e&, gives enterprises regional compliance while maintaining global visibility.
Cato has also proactively pursued compliance with industry-specific standards like PCI DSS 4.0, helping regulated customers in finance, healthcare, and e-commerce sectors meet baseline security expectations. This compliance posture may also help customers lower premiums or qualify for cyber insurance, which increasingly demands proof of modern security controls across data classification, multi-factor authentication, and real-time threat prevention.
Converged SLAs and Outcome-Based Procurement
Enterprises are shifting away from piecemeal infrastructure procurement toward service-level agreements (SLAs) tied to business outcomes. Rather than buying firewalls, routers, and monitoring tools separately, buyers now prioritize guarantees around uptime, latency, and threat blocking, particularly in global, hybrid environments.
Legacy architectures split accountability across multiple vendors, creating ambiguity when performance issues arise. Cato offers end-to-end SLA coverage by controlling both the network and security stack from edge to core.
As more enterprises write RFPs that demand measurable improvements, such as latency thresholds or total threat containment, Cato’s single-vendor approach positions it well. Customers like ESI cite the value of consolidated observability and response. For companies prioritizing rapid site deployments, high security efficacy, and reduced downtime, outcome-focused SLAs could make Cato an increasingly attractive alternative to traditional telco-security stacks.
Key Risks
Generative AI-Enabled Threats
Generative AI is dramatically lowering the barrier to entry for cyberattacks. A researcher from Cato CTRL, Cato’s threat intelligence team, demonstrated how an LLM could be manipulated into developing malware using a fictional narrative that bypassed standard AI safeguards. In this test, the researcher, who had no prior experience in writing malicious code, used an "immersive world" strategy to train the LLM into creating a working infostealer that could extract browser credentials from Google Chrome.
Cato’s Chief Security Strategist Etay Maor warned that these methods create a new class of “zero-knowledge threat actors,” individuals with no technical expertise capable of launching enterprise-grade attacks. Government-backed groups are already experimenting with this dynamic. Google’s Threat Analysis Group observed state-affiliated actors from China, Iran, North Korea, and Russia using AI for reconnaissance, payload design, and scripting. If these threats escalate, enterprise demand for SASE platforms may grow, but so too will scrutiny over whether Cato can respond to increasingly AI-driven adversaries faster than its competitors.
Competitive Feature Depth and Budget Disparity
Cato faces growing pressure from better-resourced rivals expanding their product breadth. Palo Alto Networks’ Prisma Access integrates Cloud Identity Engine and Cloud Access Security Broker (CASB) features, capabilities not currently offered by Cato. Customers rate Prisma Access higher in advanced policy control and threat prevention, suggesting that enterprise buyers may favor deeper security stacks over integrated simplicity.
This feature gap is compounded by resource disparity. Palo Alto’s R&D budget reached $1.9 billion in the year ending January 2025, far exceeding what private competitors like Cato can likely allocate. Zscaler and Cisco are also accelerating investments in autonomous threat response and AI-driven analytics. Without a step-change in platform capability or product velocity, Cato risks being boxed out of large enterprise deals by incumbents with broader portfolios and deeper budgets.
Summary
Cato Networks operates in the Secure Access Service Edge (SASE) market, offering a vertically integrated platform that unifies networking and security into a single software layer. It targets infrastructure complexity driven by hybrid work and cloud adoption. As of July 2024, it has surpassed $250 million in ARR with more than 2.5K enterprise customers and a valuation of over $4.8 billion. The key question is whether Cato’s single-vendor approach can keep up with product expansion and enterprise requirements at scale.






