Thesis
In 2024, 67% of the world’s more than 8 billion people use the internet to fulfill daily needs across work and entertainment. Despite the massive adoption of the internet, however, security is not guaranteed. In the US, for instance, over 880K Americans reported falling victim to a cyberattack in 2023, leading to potential losses exceeding $12.5 billion. This figure represents a 22% increase in losses suffered, compared to 2022. While individual records of personal data can be leaked through phishing attacks and malware, data breaches, or coordinated attacks to breach entire data centers containing sensitive personal information, can also cause millions of records to be leaked at once.
For instance, Facebook has faced multiple major data breaches since 2013, including a breach in April 2018 that caused 50-90 million users’ data to be exploited and sold by a third-party firm, Cambridge Analytica. This incident caused Facebook to pay a historic $5 billion fine for violation of data security and poor data protection practices. Another case from December 2023 saw the New York-based online real estate education platform Real Estate Wealth Network lose 1.5 billion customer records to hackers, amounting to 1.2 terabytes of data that included sensitive information like homeowner’s association liens and tax IDs, which cybercriminals could exploit to carry out social engineering attacks and commit financial fraud. The urgency to prevent data breaches comes as IBM researchers found that the average cost of a data breach in July 2024 jumped to $4.9 million from $4.5 million in July 2023 — a 10% spike in just one year.
Traditional incumbents, however, approach preventing data breaches with an outdated method. They rely on predefined rules and signatures that cannot identify new threats, lack visibility of the entire network, scan codebases slowly, and generate many false positives and negatives, leading to unnecessary disruptions and failure to detect actual threats.
That’s where Semgrep comes in. Semgrep is an application security platform that helps technology companies secure their applications at the development stage. Its products allow engineering teams to scan code quickly, remove false positives, and secure code according to custom rules with AI. Semgrep’s mission is to help shape the future of software analysis and security with secure code guardrails.
Founding Story
Semgrep was founded in 2017 by three MIT graduates: Isaac Evans (CEO), Drew Dennison (CTO), and Luke O'Malley (CPO). Evans and Dennison were college roommates at MIT, and O'Malley joined in December 2017 as Head of Product to form the founding team. Their diverse backgrounds include significant experience at companies like Palantir, MIT computer science research labs, and roles within Fortune 500 companies. During Evans and Dennison’s time from August 2016 to June 2017 as Entrepreneurs in Residence at Redpoint Ventures, they explored concepts inspired by their extensive coding experiences.
One of their ideas was to develop an application to help small companies secure their code. Evans and Dennison identified that top tech companies have the talent and resources to embed security at the code level and enforce uniform coding standards, but many other organizations lack the necessary tools and expertise to achieve the same level of security.
Initially launched as r2c in 2017, the company faced challenges in building a rules-based security engine specifically tailored for developers. The turning point came in 2019 when Evans hired Yoann Padioleau, a former Facebook engineer. Upon joining the team, Padioleau introduced them to sgrep, a tool he had built as part of pfff, a program analysis library developed at Facebook in 2009. At a hackathon shortly after, Padioleau demonstrated how sgrep could be enhanced by adding support for modern programming languages like Python, transforming it into a functional application security tool for developers.
Recognizing the potential of sgrep to fulfill their vision, the team forked it from pfff for further development and eventually renamed it to Semgrep. The open-source version of Semgrep (Semgrep OSS) was released at the end of 2020. As of April 2023, Semgrep’s open-source tool has grown to over 2 million users worldwide.
Product
Semgrep Open-Source Engine
At the core of Semgrep’s product line is its free, open-source engine—a lightweight static analysis tool that is reportedly both fast and efficient. Unlike the traditional "grep" command, which searches for exact strings or regular expressions within files, Semgrep understands the context and meaning behind the code—hence the term "semantic grep."
For instance, using grep to search for "2" will only result in instances where the exact string "2" appears. However, Semgrep can identify code like: x = 1; y = x + 1.
The product would recognize that y ultimately equals 2. This semantic understanding allows Semgrep to find patterns and potential issues that simple text searches would miss.
In addition to accurate query results, Semgrep also delivers scans that outperform other open-source tools. It focuses on single-file analysis, so the control flow graph—the representation of all possible paths through a program—never exceeds the size of a single file. As the tool tracks the flow of potentially harmful data through the entire program using taint analysis, it collects taint summaries incrementally and stitches them together.
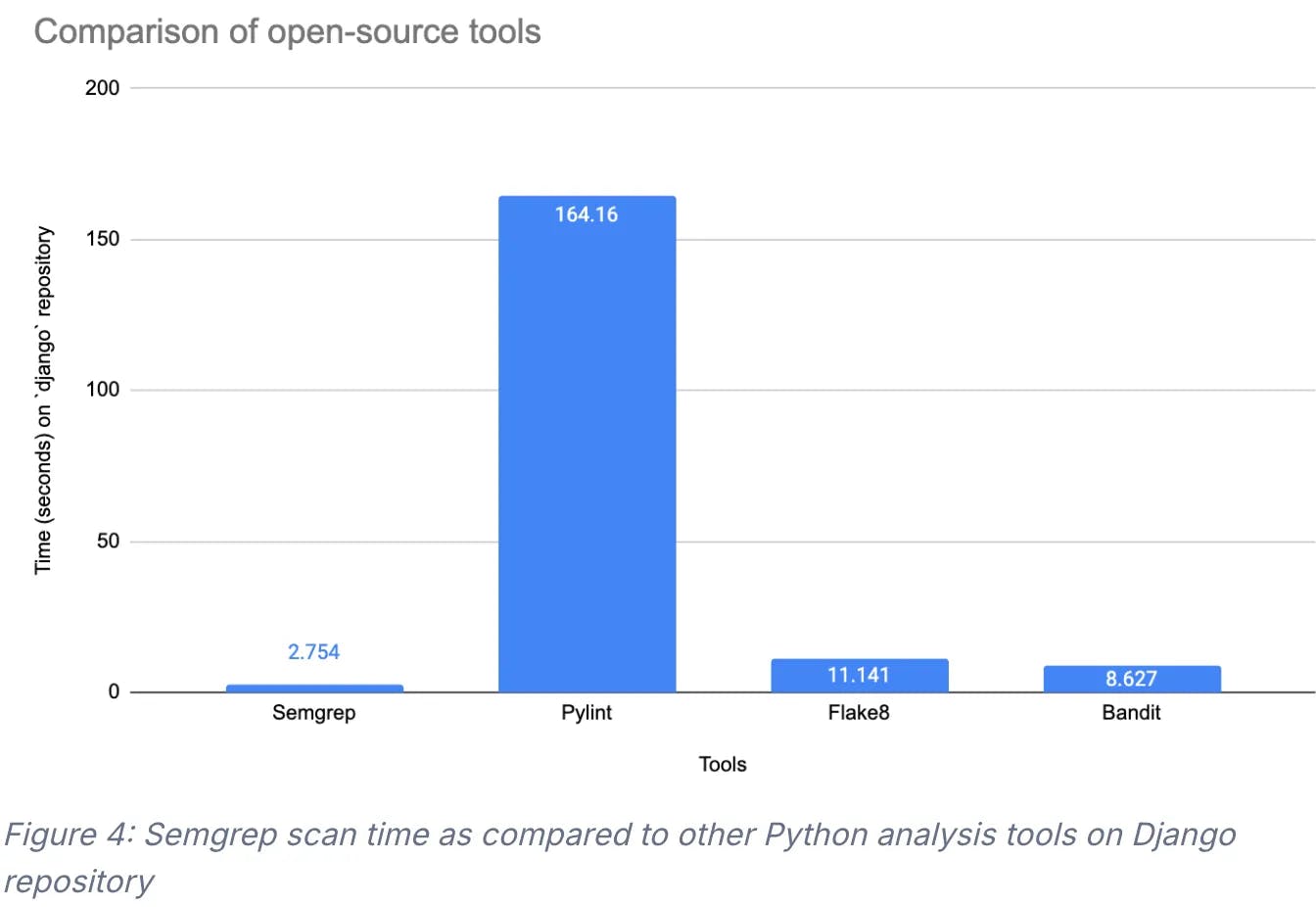
Source: Semgrep
Lastly, implementing Semgrep community rules, or code guidelines written by Semgrep’s developer community, eliminates the need to wrestle with abstract syntax trees (the hierarchical structure of code) or complex regular expressions later on in development. These rules simplify the process of scanning code for patterns, making it more accessible and less time-consuming.
Over time, as developers continued to validate Semgrep's open-source capabilities, it led to the project gaining over 10K stars on GitHub and being used for 30 million scans in 2022. As a result, the team continued to evolve the product engine into mature products for the enterprise.
Semgrep Code
Semgrep Code allows organizations to deploy, manage, and monitor Semgrep at scale, leveraging both community and Pro rules to surface issues in the codebase. The main differences between this paid product and the free, entry-level OSS product, are that Semgrep Code, via its Pro Engine, supports over 40 languages, offers 900+ professional security rules that are updated weekly, eliminates 95% of false positives from scans, and leverages AI to address key security issues.
Semgrep Code’s significant improvements can partly be attributed to its Pro engine, which is specifically designed for interfile analysis. While the lighter-weight, open-source version of Semgrep focuses on analyzing one file at a time—which might cause it to miss vulnerabilities that span multiple files—the Pro engine can analyze across multiple files.
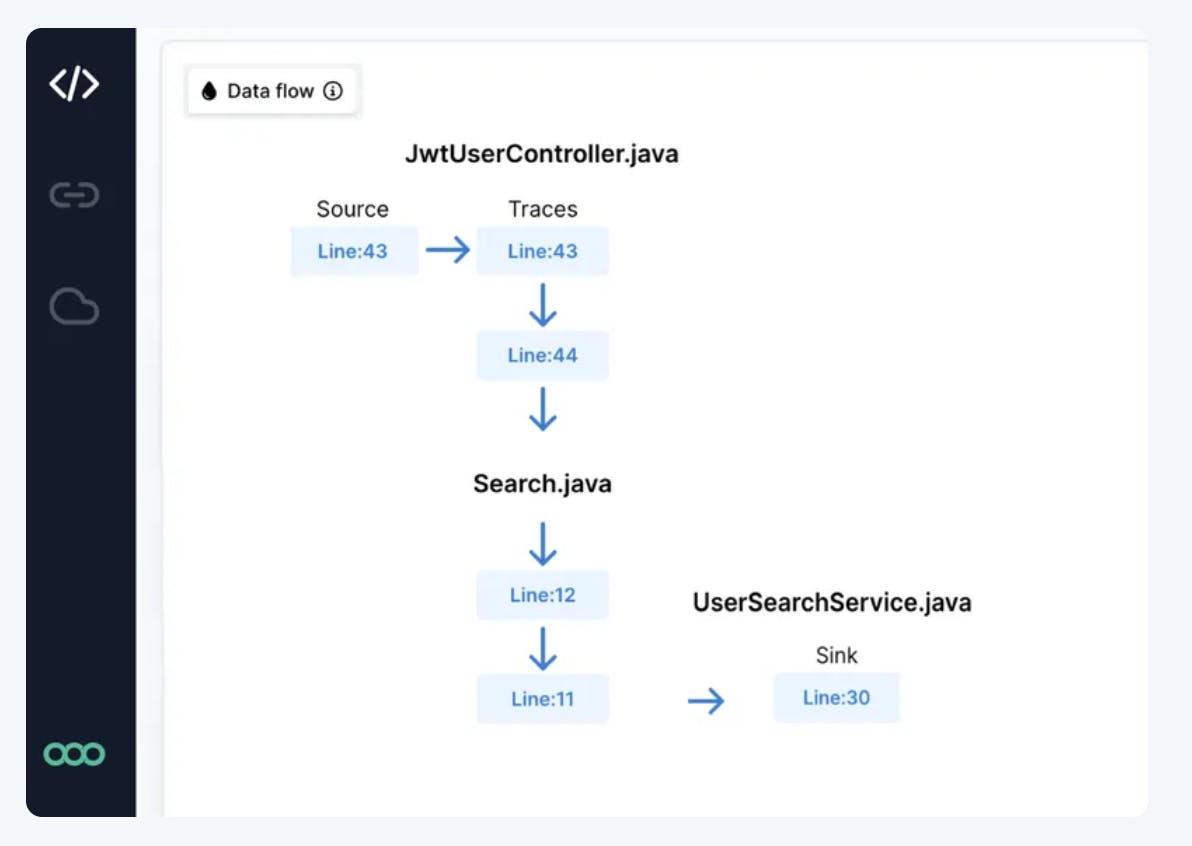
Source: Semgrep
Additionally, the Pro engine offers interprocedural analysis, including advanced dataflow analysis methods such as taint analysis (tracking the flow of potentially harmful data through the code), constant propagation (determining values that can be computed at compile time), and type inference (automatically detect an expression’s type).
Semgrep Assistant
Launched in March 2024, Semgrep Assistant can provide real-time remediation as accurate, urgent vulnerabilities are identified. As developers code, they receive Semgrep findings from the Assistant and can address vulnerabilities before they become embedded in the codebase. Built on top of OpenAI’s GPT-4, Semgrep Assistant provides auto-triage findings and auto-fix code capabilities while being context-aware. As of March 2024, the product’s custom rule-writing feature was currently in beta.
Hallucination, or AI models outputting incorrect information, is largely eliminated from Semgrep Assistant by augmenting GPT-4 with more application security (AppSec) guardrails. For instance, specific advice from the Assistant is possible by recognizing the category of code a developer asks via metadata from Semgrep rules. Auto-fix suggestions by the Assistant are not directly from GPT-4 but corrected semantically with a chain of questions to ensure the fix is free from syntax errors, intra-file incompatibilities, and more. To take Assistant’s abilities even further, Semgrep’s team is even experimenting with prompting it to write Semgrep rules or using it to increase data quality across applications.
Semgrep AppSec Platform
Semgrep’s AppSec Platform allows Semgrep Code to work effectively at scale. This platform provides teams with a holistic view of their development processes, allowing them to automate, manage, and enforce code standards across the organization for code, supply chain, and secrets.
A key advantage of the Semgrep AppSec Platform is its ability to engage developers directly within their existing workflows. Developers can work on code changes without disrupting their feature development velocity because the platform displays pull request discussions exactly where they need them. Its diff-aware scans focus on issues in current code changes rather than accumulating past issues, enabling developers to concentrate on what is immediately relevant.
Source: Semgrep
The platform allows for quick deployment of scans across the entire organization, integrating seamlessly with tools like GitHub, GitLab, and other source code management (SCM) and continuous integration (CI) systems. Security teams also gain granular control over how detected issues are handled. They can specify which issues are monitored by security, which ones notify developers within their workflow, and which critical bugs block code merges. Managing findings is streamlined through the platform's user interface, where teams can filter results by project, severity, branch, or specific rules. Integration with communication tools like Slack and email ensures that important alerts about critical findings reach the right people promptly.
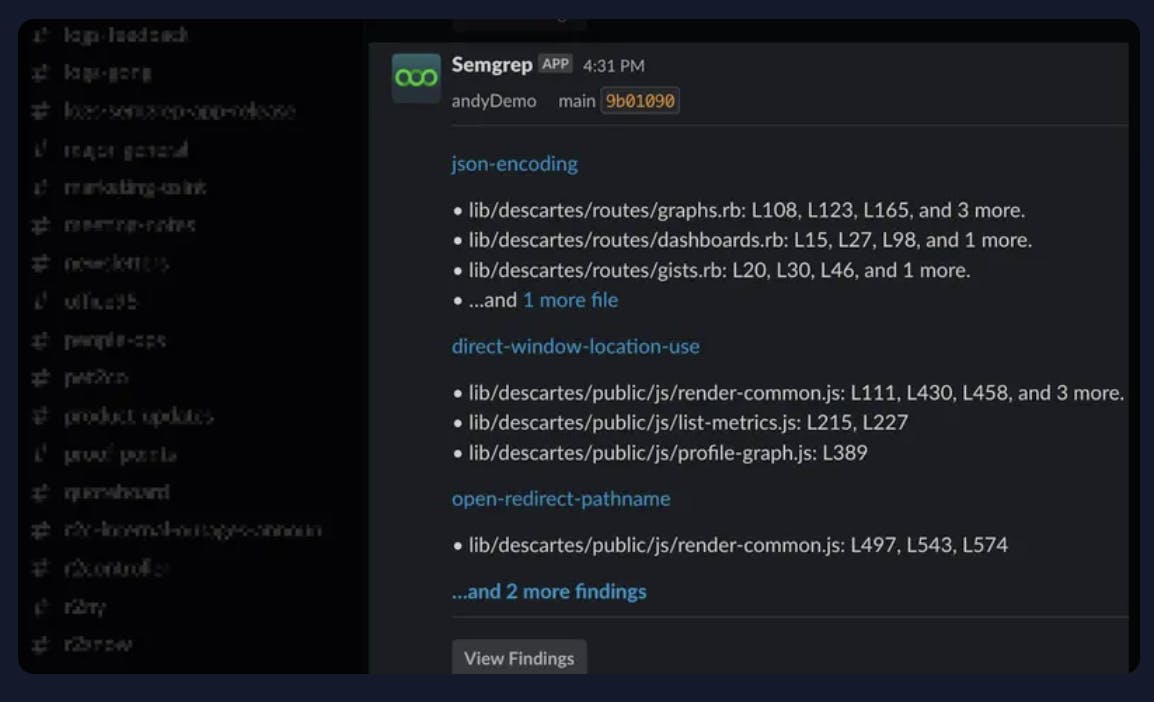
Source: Semgrep
Semgrep Supply Chain
Semgrep Supply Chain focuses on securing third-party dependencies by reducing false positives from vulnerability scanning by 98%. It achieves this using reachability analysis, or an assessment that determines whether a vulnerability is truly reachable from the code.
A reachable vulnerability refers to a section of code within an application that can be immediately exploited. By focusing on just reachable vulnerabilities, Semgrep Supply Chain helps developers prioritize the most pressing issues, reducing less important alerts. One report found in March 2024 that compared to its competitors Dependabot and Snyk, Semgrep outperformed both companies in the number of false positives its Supply Chain product produced.
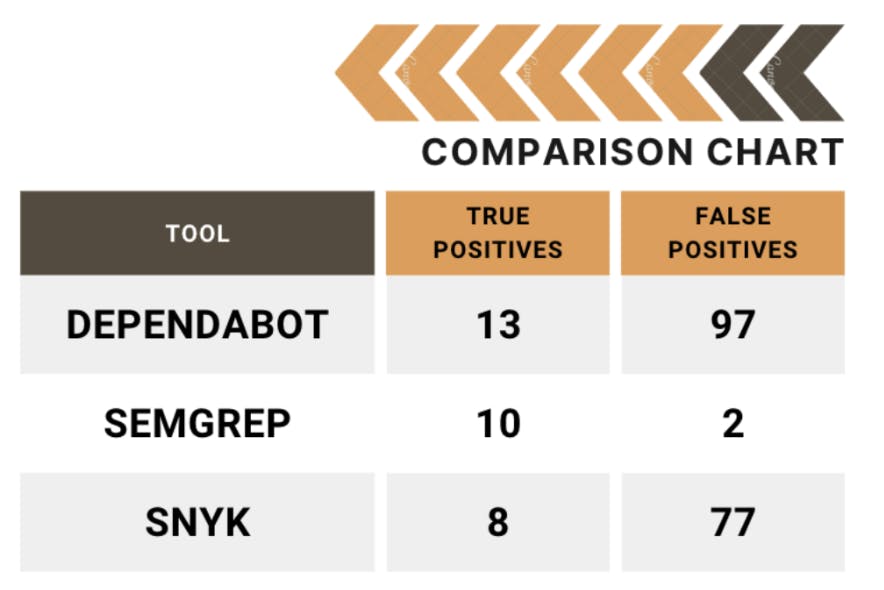
Source: Doyensec
Semgrep has built the foundation of its Supply Chain tool through a rule-writing approach. In-house rules are written by Semgrep’s team for every Common Vulnerabilities and Exposures (CVE) published by users. Specific rules are then activated when a team's code uses the same vulnerable functionality. This means that every dependency vulnerability identified is traced back to the exact line of code that uses the vulnerable component.
For example, Lyft implemented Semgrep Supply Chain to identify and prioritize the dependency updates that mattered most to their development. They previously struggled with noisy results from another SCA product, which made it difficult to surface actionable findings to developers. With Semgrep's reachability analysis, Lyft reduced scan noise by 95%. When the critical Log4Shell vulnerability was announced, Lyft’s security team was able to identify and remediate all instances immediately.
Semgrep Secrets
Semgrep Secrets enables developer teams to detect sensitive information leaks, such as API keys and passwords, with precision across files and surface them for remediation. Traditional scanners that leverage regex (pattern matching) and entropy analysis (detecting randomness) can generate numerous false positives, resulting in a lack of prioritization of results and missed coverage. These shortfalls make it challenging for developers to identify any real issues.
By contrast, Semgrep Secrets leverages its open-source and Pro engines to automatically warn of likely secrets leaks using semantic analysis. The dataflow engine understands what credentials exist and how they're being used within the code, providing a more accurate detection mechanism. This approach prioritizes valid credentials and reduces false positives, allowing developers to focus on critical issues.
To illustrate how Semgrep's semantic analysis goes beyond merely detecting sensitive leaks and actually understands how data is used in your code, consider this example.
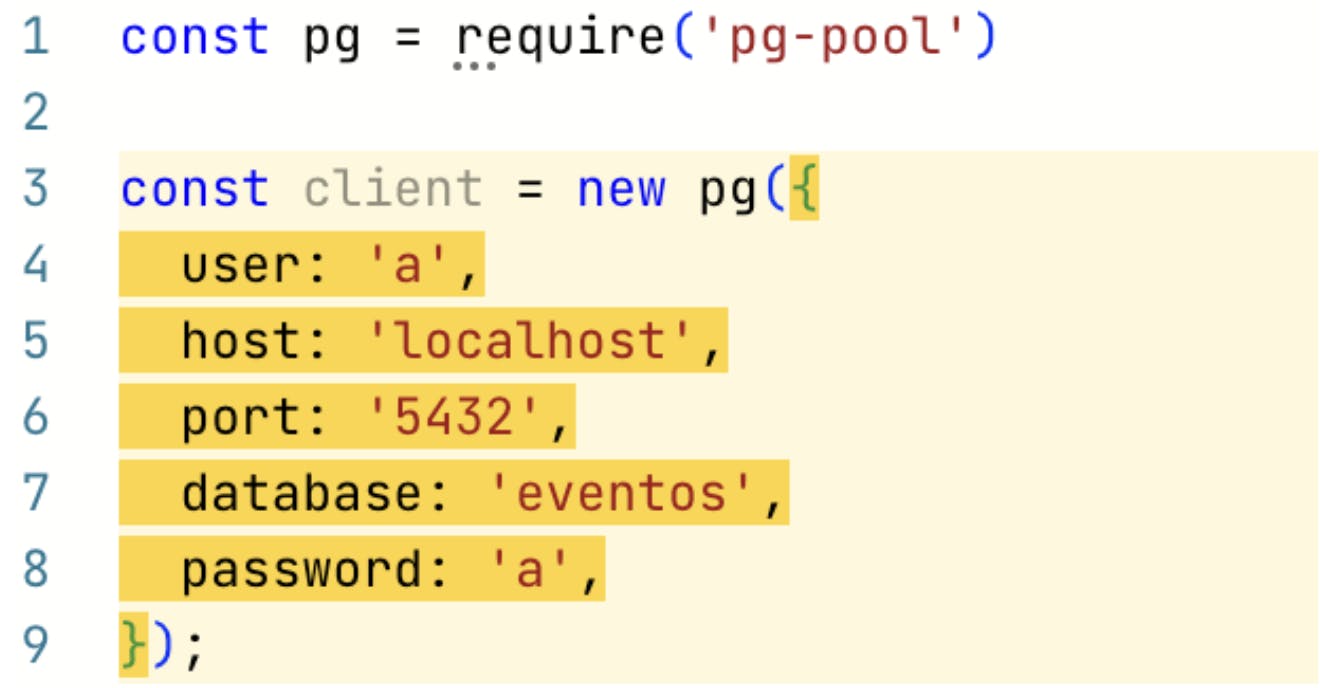
Source: Semgrep
In the given lines of code, Semgrep identifies a hardcoded password on Line 8. Most scanners would catch this because they search for common keywords like "password" using regular expressions (patterns that match specific text).
However, simply searching for the word "password" can produce a lot of irrelevant alerts—what developers call "noise." This word might appear in comments, variable names, or test code where it is not actually a security issue. Many organizations that Semgrep serves have ended up disabling these generic checks entirely because of the overwhelming number of false positives.
Semgrep Secrets, however, understands the context of the code to help teams prioritize even these generic alerts. In this example, Semgrep recognizes that 'pg-pool' on Line 8 is a common PostgreSQL connection library. It can convey that not only is there a hardcoded credential on Line 8, but it's also part of a database connection being established on Line 3. For security teams, hardcoded database credentials are a high priority. Semgrep Secrets allows teams to filter down to these similar specific, critical results and even bring these findings directly into developer workflows as comments on pull requests.
Lastly, teams can write custom rules to detect secrets specific to their internal services. This flexibility ensures that Semgrep Secrets can adapt to the unique security standards of different organizations.
Market
Customer
Semgrep primarily serves development and security teams within both small and large startup technology companies. Semgrep’s ideal customers are typically late-stage tech companies, as they prioritize scaling and possess the financial resources to invest in Semgrep’s enterprise products. As these companies grow, they are likely to continue using Semgrep’s offerings, thereby contributing to consistent revenue growth for the company. As of March 2025, notable customers such as Lyft, Snowflake, and Figma exemplify Semgrep’s ideal profile, representing late-stage, high-growth tech companies.
Compared to large enterprises, startups present a more accessible market for Semgrep, as they need to ensure application security but often lack the budget to employ dedicated AppSec teams. Startups also typically have less complex codebases and development structures, which makes onboarding to Semgrep more efficient. To accommodate the needs of startups, Semgrep offers flexible options, including free access to its full-featured products for teams under 10 members. As these teams grow, they can customize their solutions through separate pricing for Semgrep Code, Supply Chain, and Secrets products.
Market Size
The global cybersecurity market was valued at $185.7 billion in 2024 and is expected to grow to $271.9 billion by 2029, reflecting a 7.9% CAGR over this period. Semgrep specifically operates in the application security (AppSec) market, which was valued at $7.4 billion in 2024 and is estimated to grow to $13.6 billion by 2029, reflecting a CAGR of 12.9%. As of 2024, the US was a sizable majority of the market, generating over $3 billion in revenue annually and taking up 40.5% of total global market share.
Competition
Legacy Players
Microsoft Purview
Founded in 1975, Microsoft is a global technology leader known for its software and hardware products. With Microsoft Purview, the company offers enterprises a suite of cybersecurity services, including data security, compliance and risk management, data governance, and audit capabilities. Microsoft Purview enhances application security scanning by providing visibility into an organization's data landscape and identifying sensitive data across applications, databases, and cloud services. By leveraging Purview's data discovery and classification capabilities, businesses can proactively detect vulnerabilities and compliance risks in their applications.
Purview integrates well with customers deeply invested in Microsoft’s ecosystem, particularly those using Microsoft 365 and Azure. However, organizations often face challenges with Purview’s complexity in implementation and management. Scalability issues can arise as businesses grow, and integrating Purview with third-party tools and systems can be problematic.
HCL AppScan
HCL Technologies, founded in 1976, is a global IT services and consulting firm. In 2018, HCL acquired AppScan from IBM, a tool originally developed to provide security testing solutions. As of March 2025, AppScan has several core offerings. For Scanning, HCL offers AppScan Standard, Enterprise, Cloud, and 360. These products find and mitigate vulnerabilities in code, offered at different levels. For Testing and Remediation, HCL offers AppScan Source, Supply Chain, and CodeSweep. These products enable static analysis testing and triage, code testing, and code remediation to resolve vulnerabilities early in development.
HCL AppScan helps organizations secure their applications by scanning application code and runtime behavior to identify security vulnerabilities. It works by analyzing source code, binaries, and web-based applications through techniques such as static analysis (SAST), dynamic analysis (DAST), and interactive testing (IAST). AppScan detects common issues like injection flaws, cross-site scripting (XSS), and insecure authentication methods, and provides developers with actionable findings to fix these problems early in the development lifecycle.
Users of AppScan have reported slow scanning, especially during exploration, due to navigating large, complex applications. Configuring and managing AppScan, especially with modern client-side technologies, is complex and time-consuming, making it less accessible to non-expert users. Some users have also noted a decline in product quality over time.
Black Duck
Black Duck, established in 1986 as Synopsys, is known for electronic design automation and semiconductor IP but has expanded into software security services in the last decade. The company helps organizations identify and manage open-source software risks. It scans application codebases to detect open-source components, tracking licenses, security vulnerabilities, and compliance risks. By comparing code against a regularly updated database of open-source projects, Black Duck highlights known vulnerabilities and licensing conflicts. It then provides developers with detailed reports and recommendations, enabling them to remediate security issues and ensure compliance with open-source licensing requirements.
Black Duck’s security offerings include fAST Dynamic, which is a dynamic analysis tool that detects vulnerabilities in running web applications without needing source code access. fAST Dynamic users have reported performance issues dealing with highly complex applications. Its Static Application Security Testing (SAST) tool conducts in-depth manual tests to identify security vulnerabilities in source code, boasting a low false-positive rate and good integration capabilities. However, its SAST tool faces criticism for slow scanning times and a difficult setup process. Users have also experienced inconsistent alarms and false positives, which can disrupt development operations. Implementing the tool comprehensively across all applications can be expensive, posing a barrier for some organizations.
Earlier Entrants
Checkmarx
Checkmarx, founded in 2006, serves large enterprises mainly by securing their application development from code to cloud. As of March 2025, its clientele included companies across industries like finance, automotive, aviation, and technology, such as Citi Bank, Ford, Airbus, and Apple. The company’s investors include Insight Partners and Salesforce Ventures. In April 2020, the company was acquired by Hellman & Friedman, TPG Capital, and Insight Partners through a $1.15 billion LBO.
While Checkmarx also offers SAST, DAST (application testing), and Supply Chain SCA (application security) products similar to Semgrep, the two companies’ offerings differ significantly due to the clientele they target. Checkmarx primarily caters to large Fortune 500 companies, often emphasizing security over speed, whereas Semgrep focuses on both speed and security, appealing to fast-growing tech companies. This difference is evident when comparing their products.
For Checkmarx SAST/DAST vs. Semgrep Code, one key distinction is language support; startups frequently adopt new languages and technologies, leading Semgrep to support over 40 languages compared to Checkmarx’s 23. In terms of scan speed, Semgrep offers fast scans, completing all types in under five minutes, whereas Checkmarx can take hours for large scans. Furthermore, Semgrep rules are straightforward, resembling source code, while Checkmarx’s rules are more complex and require familiarity with their proprietary library and C# for customization.
In comparing Checkmarx SCA to Semgrep Supply Chain, Semgrep reportedly excels in minimizing false positives, achieving a reduction of 80-95% in false positives, while Checkmarx does not disclose an official false-positive rate. Additionally, Semgrep facilitates developer feedback through pull request comments, allowing security teams to quickly gain more accurate insights, a feature not present in Checkmarx. However, Checkmarx offers automatic remediation capabilities to patch dependencies, a feature Semgrep currently lacks.
Lastly, when comparing Checkmarx SCA to Semgrep Secrets, Semgrep employs semantic analysis to grasp the context of the code, surpassing basic regex and entropy analysis, thereby reducing noise and enhancing true positive detection. Checkmarx’s SCA product does not include this feature.
Snyk
Snyk was founded in 2015 and specializes in automatically fixing vulnerabilities in code, open source dependencies, containers, and infrastructure as code. As of March 2025, Synk served a number of large enterprises across different industries from manufacturing to music streaming.
Snyk offers products like Snyk Open Source and Snyk Code, which have gained significant traction with over 2.2 million users worldwide. As of March 2025, the company’s funding exceeded $1 billion from investors like Google Ventures, Accel, and Tiger Global Management. However, in key areas like accuracy, remediation, and user experience, Semgrep’s product supposedly proves to be superior.
In terms of accuracy, Snyk produces a significant amount of false positives that can waste time and erode confidence. In contrast, Semgrep delivers up to a 98% reduction in false positives. Regarding code remediation, teams using Snyk must manually filter and prioritize findings due to a lack of reachability analysis. This can slow down developers’ productivity and may not be conducive to resolving the most pressing vulnerabilities. In contrast, Semgrep’s built-in reachability analysis and EPSS filtering features present only high-priority issues to developers in their workflow. Semgrep’s AI triage recommendations also have a 90% user agreement rate, leading to higher productivity and efficiency for Semgrep teams. Finally, teams using Snyk may face long scan times and time outs that block pull requests, generic fix guidance that lacks specificity, and constant switching from their developing environment to security tooling. Semgrep embeds fix guidance and security tooling into developers’ workflows and offers faster scan speeds.
Veracode
Founded in 2006, Veracode is a cloud-based application intelligence and security company catered to industries such as pharmaceutical, media, and automotive, as well as government agencies with customers such as McKesson, Hearst, BMW, and the US Nuclear Regulatory Commission in March 2025. In March 2022, the company was acquired by TA Associates at a $2.5 billion valuation.
Veracode offers comparable products to most of Semgrep’s core suite of services, including SAST, DAST, and SCA products, but it caters to a very different clientele. Veracode’s products have high-accuracy scanning (low false positive and false negative rates), support for scanning over 100 languages and frameworks quickly and accurately, and real-time remediation. In addition, Veracode’s product has been recognized as a leader on the Gartner Magic Quadrant for Application Security Testing 8 times. But while Veracode excels in comprehensive security testing and enterprise-focused features, Semgrep reportedly offers a more granular and adaptable approach to static code analysis, catering to developers who require customized and immediate feedback on their code.
Business Model
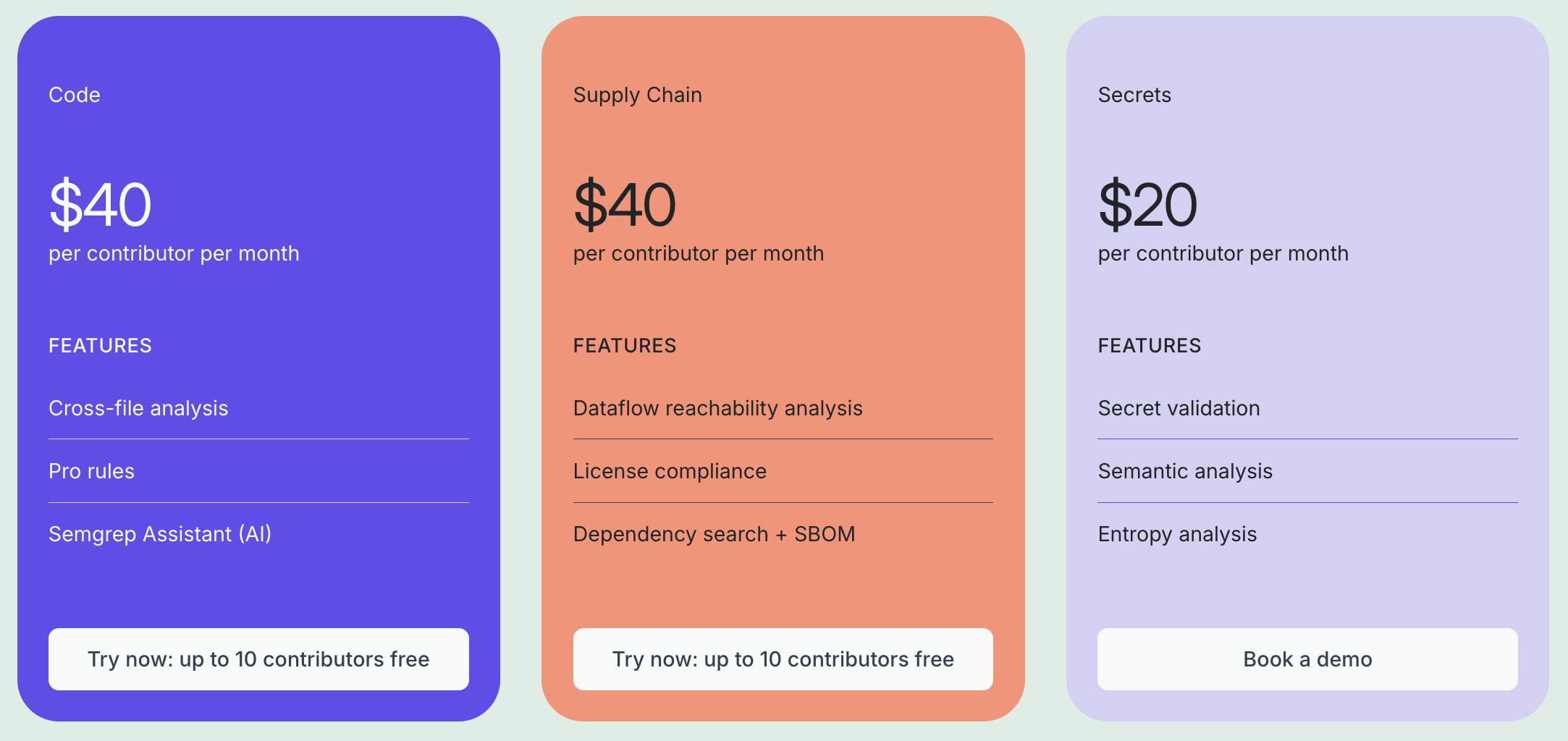
Source: Semgrep
Semgrep's primary revenue stream comes from a SaaS pricing model that charges customers a monthly subscription based on the number of contributors on their team.
Semgrep Code is priced at $40 per contributor per month and includes features like cross-file analysis, pro rules, and the Semgrep Assistant (AI).
Similarly, Semgrep Supply Chain also charges $40 per contributor per month, offering dataflow reachability analysis, license compliance, and dependency search.
Semgrep Secrets is available at $20 per contributor per month, providing features such as secret validation, semantic analysis, and entropy analysis.
Semgrep makes its products accessible to smaller teams by making Semgrep Code and Supply Chain free to use for projects with fewer than 10 monthly contributors. Startups also benefit from special pricing options tailored to their needs. For larger organizations, team and enterprise tier plans are customized based on specific requirements.
Traction
As of April 2023, Semgrep’s OSS had around 2 million users and its revenue-producing products grew by 750% from 2022. Its products also hit 100 million scans annually in 2024. An unverified estimate also indicated that Semgrep’s annual revenue could be around $15 million in 2024 servicing more than 150 enterprise customers.
Valuation
In February 2025, Semgrep raised a $100 million Series D from Menlo Ventures at an undisclosed valuation, with participation from existing investors, such as Felicis Ventures, Harpoon Ventures, Lightspeed Venture Partners, Redpoint Ventures, and Sequoia Capital. The company had previously raised a $53 million Series C in April 2023 at a $395 million valuation. This Series D brought the company’s total funding to $193 million as of March 2025.
Key Opportunities
Evolving Threat Landscape
Ransomware, or malicious software that blocks access or steals a victim's sensitive data unless a "ransom" is paid, has become a serious threat to corporations worldwide since the WannaCry ransomware attack in 2017. That major incident affected more than 200K computers in over 150 countries, with notable victims including FedEx, Honda, and even the UK’s National Health Service (NHS). Since then, 71% of companies have encountered at least one ransomware attack, resulting in an average financial loss of $4.9 million per breach.
In 2023 alone, organizations worldwide encountered over 60K attempted cyberattacks, with approximately 72% falling victim to one. 2023 also represents an all-time peak for global ransomware attacks, with 10% of organizations experiencing an attempt (up from 7% in 2022). Today’s attackers are also ever-evolving, employing new methods like double-extortion (stealing data on top of encrypting, threatening to leak) and triple-extortion (same as former, but also demands ransom from a company’s customers and partners), causing organizations to incur additional damages. This worrisome backdrop represents a key opportunity for Semgrep to continue to develop its Supply Chain product to ensure sensitive information is protected as early on as possible.
AppSec AI Agent
Semgrep Assistant today already helps AppSec engineers and developers on its platform make correct security decisions faster with 95% positive feedback on its suggestions. So as software engineers increasingly offload their cognitive load to AI for repetitive and tedious busy work, Semgrep has an opportunity to automate some or all of security developers’ work. This opportunity is especially pertinent when considering the 2.8 million unfilled jobs in cybersecurity globally, with the biggest gap in the Asia-Pacific region.
To achieve this goal, Semgrep can continue to fine-tune its assistant using cutting-edge AI models. Semgrep can also use advanced ML techniques like chain-of-thought to ensure that Semgrep Assistant does not give vulnerable or incorrect fix suggestions. Additionally, onboarding the Assistant with organization-specific rules, categories, and even objectives may yield better results during auto-triage.
Securing Third-Party Vulnerabilities
Traditionally, businesses have primarily focused on due diligence as a means of managing third-party risk. This has involved lengthy questionnaires, certifications, and collaborations with vendors to verify security controls. However, the increasing popularity of third-party applications across mobile and desktop platforms from various industries has led to a complex and challenging ecosystem to manage. This is because more interconnected apps within an organization create more potential vulnerabilities, as evidenced by significant attacks in the supply chain and healthcare industries.
As a result, companies globally are playing catchup as 45% of them experienced third-party-related issues over the past two years. 65% of security leaders today have increased their third-party risk management budgets, and 76% are dedicating more time to third-party cybersecurity risk management initiatives compared to two years ago. However, the additional time and resources haven’t yielded the desired outcomes; over 50% of respondents have reported an increase in disruptions due to third-party-related incidents. For Semgrep, this represents a valuable opportunity to secure third-party applications and its integration with other parties’ platforms.
Key Risks
Ensuring Community Rules’ Quality
Semgrep’s extensive catalog of community rules is essential to securing organizations’ applications. The rules serve as the basis for the over 100 million annual scans that Semgrep’s products conduct. While Semgrep has an in-house team that writes professional, proprietary rules for its users and allows custom, private rules to be written by their customers, community rules, or rules contributed from Semgrep’s community, will be the main source of rules that Semgrep will have as its platform scales. Maintaining the quality of these user-contributed rules will be key to its products’ success. They are currently reviewed manually by Semgrep’s team, which causes slowdowns during extended periods of growth. Solving this bottleneck could prove crucial for Semgrep’s growth.
AI-Powered Cyberattacks
One survey of more than 800 IT and security leaders globally reports that 92% of respondents have observed an increase in AI-powered cyberattacks year-over-year. Some common AI-powered attacks include phishing emails, malware, ransomware, and social engineering techniques.
The increase in cyber threats is driven by several factors, including the widespread use of IoT devices, remote work, and a growing global reliance on virtual connectivity, which together have opened countless opportunities for scams, attacks, and vulnerabilities. Generative AI tools further exacerbate the situation by enabling attackers to create more convincing messages and sophisticated malware with ease. Compounding the issue is a 3.4 million shortage of qualified cybersecurity personnel. Additionally, state-sponsored cyberattacks have become a common tactic for destabilizing geopolitical adversaries.
As Semgrep’s enterprise customers encounter these new forms of cyberattacks, Semgrep’s solutions need to evolve to prevent AI-powered attacks beyond essential protections like code scanning and secrets security.
Shift to Cloud & Microservices
Organizations are increasingly migrating applications and infrastructure to cloud platforms like AWS, Azure, and Google Cloud for scalability, flexibility, and cost-efficiency. Microservices, which break down monolithic applications into smaller, independent services, enhance agility, foster innovation, and enable quicker market response. Adopting cloud and microservices has become a strategic priority for companies seeking digital-era competitiveness.
If Semgrep does not adapt to effectively support cloud and microservice environments, it risks becoming less relevant in the rapidly evolving application security landscape. Microservices architectures introduce new complexities, such as increased inter-service communication and the use of containers and orchestration tools like Docker and Kubernetes. Traditional static analysis may not suffice for detecting security vulnerabilities in such dynamic and distributed systems. Without features that address these specific challenges—like scanning container configurations, infrastructure-as-code files, and integrations with continuous deployment pipelines—Semgrep may fail to meet the security needs of modern development practices and risk its market position.
Summary
Semgrep, founded in 2017 by Isaac Evans, Drew Dennison, and Luke O’Malley, addresses the critical need for robust application security. Recognizing the lack of AppSec resources at startups versus mature companies like Palantir and Facebook, Semgrep offers accessible tools for developers, including its open-source engine, Semgrep Code, Semgrep Assistant, Semgrep Supply Chain, and Semgrep Secrets. These tools provide more accurate, and developer-friendly code analysis and security scanning.
Operating in the $7.4 billion Application Security market, Semgrep serves development and security teams across various industries. It differentiates itself from competitors with faster scans, lower false-positive rates, and better integration into developer workflows. Semgrep has seen notable traction, with over 2 million users and over 100 million scans annually. The company has the opportunity to address evolving threats, advance its AI-powered AppSec agent, and secure third-party vulnerabilities. However, to maintain competitiveness, Semgrep needs to ensure community-contributed rule quality, adapt to AI-powered cyberattacks, and support cloud and microservices architectures.

