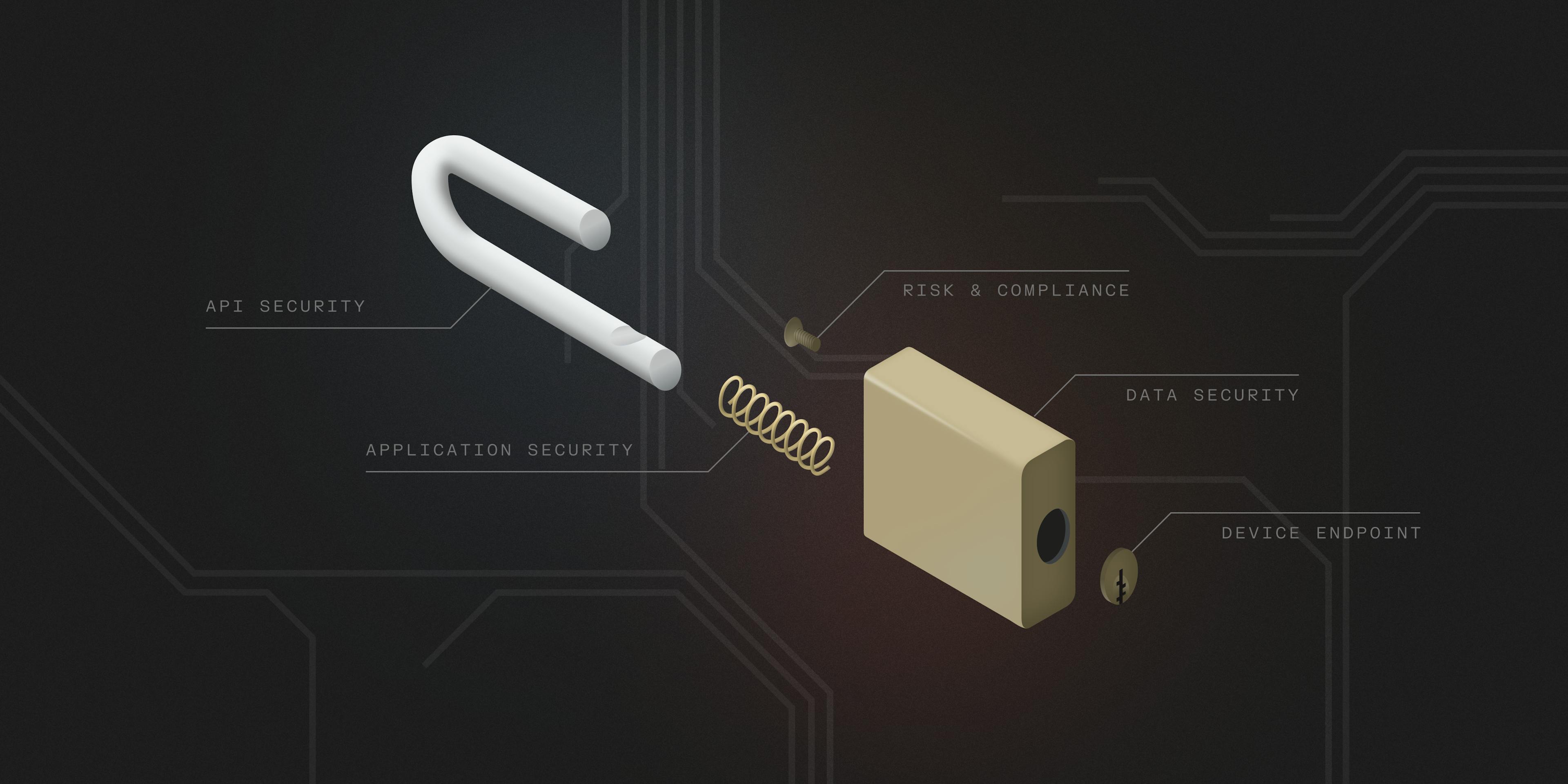
Thesis
Software is no longer generated as a bounded, deterministic artifact, but instead is assembled and continuously modified through sprawling supply chains of open source libraries, cloud services, and increasingly AI-generated code. This compositional model of software has dramatically accelerated delivery but structurally expanded potential attack surface area beyond that which perimeter-based or point-in-time application security tools were designed to defend. Dependency-driven software supply chains are overwhelming traditional, centralized security models: as of 2025, 70% of organizations rely on open-source code for mission-critical workloads, and 70% of IT teams spend more than six hours per week on security patching. As cloud-native architectures have collapsed the notion of a fixed perimeter, security risk has shifted from isolated code defects to emergent failures across dependencies, configurations, and runtime behavior that evolve faster than centralized security processes can govern.
That same dynamic is now intensifying as software development and deployment become increasingly AI-assisted and agentic. Legacy AppSec models assume software can be statically inspected and execution paths can be meaningfully predicted before deployment. AI-native systems violate those assumptions by introducing non-deterministic behavior, tool-augmented execution, and runtime decision-making that continues to change after code is shipped. As with cloud and continuous delivery, this shift renders existing security models structurally insufficient, forcing security protocols to shift upstream to where software is composed, configured, and changed.
Snyk re-architects application security around developer workflows rather than retrofitting legacy controls onto modern systems. By embedding security natively into the tools developers already use and applying it consistently across code and infrastructure, Snyk aligns security outcomes with the reality of continuous, cloud-native software creation. Because the rise of compositional, cloud-native, and increasingly AI-assisted development has made developers the only scalable security control point, Snyk shifts application security left into the developer workflow to continuously secure software as it is assembled and evolves.
Founding Story
Snyk was founded in 2015 by Guy Podjarny (founder, former CEO), Assaf Hefetz (co-founder, former CTO), and Danny Grander (co-founder). Prior to founding the company, Podjarny had worked in the Israel Defense Force’s elite cyber and intelligence unit, and Grander in the IDF R&D cyber division.
Podjarny’s motivation to start Snyk was shaped primarily by his experience building and exiting Blaze, a web front-end performance company acquired by Akamai Technologies in 2012. Following the acquisition, Podjarny served as VP and CTO of Akamai’s Web Performance business. In this seat, Podjarny recognized that while developers were increasingly responsible for performance and reliability, security tooling remained siloed, reactive, and poorly aligned with developer workflows.
Hefetz brought deep technical leadership experience to the team, having previously served as Director of Innovation at Supercom, while Grander had been CTO of Gita Technologies, an intelligence analytics company later acquired by Verint Systems. The founding team believed developers cared about security but lacked tools integrated into their workflows, an insight Podjarny framed as an early DevSecOps philosophy that embeds security directly into the development lifecycle.
In 2015, Podjarny left his executive role at Akamai to build Snyk alongside Hefetz and Grander. The founders explicitly modeled Snyk after developer-first DevOps companies such as New Relic, GitHub, and Heroku, believing that security tools should adopt the usability, distribution, and trust dynamics of developer tooling rather than traditional enterprise security software.
The team initially targeted the Node.js open-source ecosystem, focusing on npm dependency vulnerabilities, which represented a rapidly growing attack surface for modern applications. In October 2015, the team launched a free command-line interface (CLI) tool, originally branded Snyk Stranger, at Velocity Amsterdam. It enabled developers to graph dependencies and detect known vulnerabilities in open-source libraries. By December 2015, the tool had been downloaded approximately 1K times, despite lacking a registration flow, with early feedback gathered informally via Twitter. Podjarny later described an early misstep in focusing too narrowly on depth for individual developers, before realizing that security teams required broader coverage across languages and applications.
In early 2016, Snyk introduced GitHub authentication and Git integrations, allowing vulnerability detection to run continuously inside CI/CD pipelines and establishing what the company described as a “security audit as code review” workflow. While Snyk’s early freemium model drove strong developer adoption, its initial self-serve paid plan failed to convert usage into revenue. By mid-2016, the team had crossed roughly 5K registered developers but realized that while developers were the primary users, enterprise security leaders were the buyers. These security teams’ needs centered on broad governance, visibility across the application stack, and centralized controls. In response, Snyk began expanding beyond Node.js to support additional languages and added reporting and user administration features while maintaining a developer-first product experience. Snyk signed its first commercial contract in March 2017 and reached $100K in annual recurring revenue by August 2017.
In July 2019, Podjarny stepped down as CEO and was succeeded by Peter McKay, a Snyk board member since 2016 and former executive at Desktone, which had been acquired by VMware. Co-founders Assaf Hefetz and Danny Grander also stepped back from day-to-day operational roles, with Grander leaving in 2021. As of January 2026, Danny Allan serves as CTO, following prior CTO roles at Veeam and Desktone and earlier leadership in security research at IBM. Manoj Nair leads Snyk’s Emerging Technologies and Solutions Office, which is responsible for product incubation and acquisition strategy, drawing on prior executive experience at Commvault, HyperGrid, and Hewlett Packard Enterprise.
Product
Evolution of Application Security
From the 1980s through the early 2010s, security in enterprise computing was organized around a perimeter model: defend the boundary, implicitly trust what’s inside, and treat network location as a reliable proxy for legitimacy. This approach assumed that “inside” and “outside” could be meaningfully distinguished at the network layer.
As workloads moved into multi-cloud environments in the 2010s, that assumption began to break down. Static perimeter controls no longer map cleanly to applications, identities, or data flows. Even segmented trust zones preserved a core failure mode: once an attacker compromised a legitimate identity, lateral movement inside the perimeter remained feasible. The emergence of Zero Trust architectures in the mid-to-late 2010s reflected recognition that the failure was structural, not operational.
Application security evolved in parallel and inherited a similar pattern. From the 1990s through the 2000s, the industry progressed from generic web scanners to specialized approaches such as SAST (static application security testing) and DAST (dynamic application security testing), later adding IAST (interactive application security testing) and SCA (software composition analysis). This evolution was additive rather than substitutive: new tools accumulated without displacing older ones, increasing coverage while also expanding the volume of findings requiring human triage.
The delivery model of software during this period intensified these pressures. By the early to mid-2010s, CI/CD pipelines, microservices, and rapid release cycles became mainstream. In fast-moving build environments, detection tooling was no longer the bottleneck; human capacity to interpret, prioritize, and remediate findings became the limiting factor.
At the same time, application risk shifted decisively toward third-party and open-source dependencies. Highly interconnected dependency graphs allowed attackers to exploit shared components as force multipliers. Incidents such as SolarWinds (2020) and MOVEit (2023) demonstrated how a single upstream compromise could cascade across thousands of downstream organizations. This reframed AppSec from application-level vulnerability detection to supply-chain visibility and risk propagation, motivating mechanisms such as software bills of materials (SBOMs).
Organizational practices adapted in parallel. Traditional late-stage security reviews produced predictable failure modes: rushed remediation, costly rework, and adversarial handoffs between security and engineering. The “shift-left” movement, popularized in the 2010s, moved security earlier into development workflows, reducing some late-stage risk but often increasing alert volume without resolving prioritization or ownership. In response, security expanded beyond early detection toward continuous validation across the lifecycle.
The advent of AI coding tools in 2022 extends these same pressures into a more complex domain: non-deterministic software behavior. Modern systems increasingly incorporate concurrency, virtualization, distributed execution, and adaptive components that can produce different outcomes under identical inputs and conditions. In such environments, failures may be rare, intermittent, and difficult to reproduce, undermining assumptions that point-in-time testing or static inspection alone can fully characterize risk.
Taken together, this history implies a set of vendor-agnostic requirements for modern application security: security can no longer rely on network boundaries, point-in-time assessments, or centralized human review alone; it must function as a continuous control layer aligned with developer workflows, software supply chains, and non-deterministic runtime behavior.
Product Overview
Snyk is an application security platform designed to operate under modern development constraints: continuous delivery, developer-owned workflows, software supply chains, and increasing use of AI-generated code. Rather than functioning as a point-in-time scanning tool or a centralized security gate, the platform is built to act as a continuous security layer embedded across the software development lifecycle.
At its core, Snyk assumes that security decisions must keep pace with code creation. As development velocity has increased, first through CI/CD automation and now through AI-assisted coding, manual review and post-hoc triage have become structurally insufficient. For this reason, the platform is designed to integrate directly into how software is built, rather than how it is audited after the fact.
By providing centralized visibility, contextual risk prioritization, and enforceable policies that operate continuously, the platform enables organizations to maintain control without reintroducing the bottlenecks of centralized security review.
Additionally, the platform is designed to remain adaptable as development environments evolve. Through APIs and extensibility, Snyk is intended to integrate with existing and emerging tooling, including AI-assisted development environments, without assuming a fixed workflow or technology stack.
Product Suite
Snyk Code
Snyk released Snyk Code in late 2020 after acquiring Deepcode, a code parsing software, in September 2020. Snyk Code is Snyk’s static application security testing (SAST) product, designed to identify security vulnerabilities directly in application source code as it is written. Static analysis examines code without executing it, enabling teams to detect classes of vulnerabilities such as injection flaws, insecure data handling, and logic errors, before software is built or deployed.

Source: Snyk
Unlike legacy SAST tools that operate as slow, batch-oriented scans late in the development cycle, Snyk Code is built to run continuously inside developer workflows. It scans code in real time within IDEs, pull requests, and CI pipelines, returning results quickly enough to influence coding decisions while changes are still in context. This reflects a core constraint of modern development: security feedback that arrives after code is merged or released is often too late to be acted on efficiently.
Rather than optimizing for exhaustive detection, it uses application context and learned patterns from a large, continuously updated knowledge base to surface the issues most likely to matter. To further compress remediation time, Snyk Code provides guided and, where possible, automated fixes that developers can apply directly. It also extends static analysis coverage to modern development inputs, including code produced or influenced by LLM libraries and AI-assisted tooling.
Within the broader Snyk platform, Snyk Code serves as the primary control for securing first-party application logic, which the code developers write themselves. It complements Snyk’s other products, which focus on dependencies, infrastructure configuration, containers, and externally exposed surfaces, together forming a layered approach to application security across the software development lifecycle.
Snyk Open-Source
Snyk Open Source is Snyk’s software composition analysis (SCA) product, designed to manage the security and licensing risks introduced by open source dependencies. Modern applications are largely assembled from third-party libraries rather than written entirely from scratch, making dependency risk a significant source of application vulnerabilities. SCA focuses on identifying these dependencies and assessing the risks they introduce without requiring changes to application code.
Snyk Open Source continuously analyzes both direct and transitive dependencies; the libraries a project explicitly includes as well as those pulled in indirectly, to identify known vulnerabilities and license issues. Rather than treating dependency risk as a one-time audit, the product is built to operate throughout development and after deployment.
The product is designed to integrate directly into developer workflows, including IDEs, pull requests, CI/CD pipelines, and production monitoring. This allows dependency issues to be detected before they are merged, blocked from reaching production, and revisited automatically as new vulnerability disclosures emerge.

Source: Snyk
Snyk Open Source emphasizes prioritization over raw vulnerability counts. Instead of ranking issues solely by severity scores, it evaluates dependency risk using contextual factors such as exploit maturity, reachability within the application, and exposure in deployed environments. This approach is intended to help teams focus remediation efforts on vulnerabilities that pose meaningful risk to production systems rather than chase large volumes of low-impact findings. To reduce remediation friction, Snyk Open Source provides guided and automated fixes, including pull requests that upgrade vulnerable dependencies or apply patches where available.
Snyk Container
Snyk Container is Snyk’s product for securing container images and Kubernetes workloads across the software development lifecycle. Containers package application code together with operating system libraries and dependencies into deployable images, while Kubernetes orchestrates how those images run in production. Container security focuses on identifying vulnerabilities and unsafe configurations introduced at this packaging and deployment layer, risks that are not visible when scanning source code alone.
Snyk Container analyzes container images to identify vulnerabilities originating from base operating systems, installed packages, application dependencies, and Dockerfile instructions. Because container images are often reused across many services, a single insecure base image can propagate risk widely.

Source: Snyk
The product integrates into developer and DevOps workflows, scanning images in source repositories, pull requests, CI/CD pipelines, and running environments. This allows teams to remediate container vulnerabilities during build time, block risky images from being deployed, and continue monitoring workloads after release. Findings are mapped back to specific base images, Dockerfile commands, and dependency layers, with upgrade or replacement recommendations provided in context.
For Kubernetes environments, Snyk Container extends beyond image scanning to monitor deployed workloads and configurations. It detects newly deployed or updated workloads and highlights insecure settings that could increase exposure once containers are running.
Snyk Infrastructure as Code (IaC)
Snyk Infrastructure as Code (IaC) is Snyk’s product for securing cloud and platform configurations defined in code before they are deployed. IaC allows teams to provision infrastructure, such as networks, compute resources, permissions, and Kubernetes configurations, using declarative files rather than manual setup. IaC security focuses on identifying misconfigurations and policy violations at the configuration layer, where insecure defaults or overly permissive settings can introduce systemic risk before any application code runs.

Source: Snyk
Snyk IaC analyzes infrastructure definitions written in formats such as Terraform, CloudFormation, Kubernetes manifests, and Helm charts to detect insecure configurations early in the development process. Because these configurations are often reused, version-controlled, and promoted across environments, a single misconfiguration can propagate widely if not caught before deployment. Unchecked, this also leads to infrastructure drift, where deployed environments gradually diverge from their intended configuration and accumulate unmanaged risk.
Beyond individual misconfigurations, Snyk IaC supports consistent enforcement of infrastructure security standards. Built-in rulesets and policy controls allow organizations to encode best practices and compliance requirements directly into the development lifecycle, ensuring that infrastructure security is applied uniformly across teams and environments without relying on manual review.
Snyk API & Web
Snyk API & Web addresses security risks that only emerge after applications are running, focusing on web applications and APIs as they are exposed in live or pre-production environments. Unlike static or dependency-based testing, API and web security examine how endpoints respond, authentication is enforced, and data flows across exposed interfaces.
As modern applications increasingly rely on APIs, microservices, and AI-generated code, the runtime attack surface has expanded faster than development teams can manually inventory or reason about it. APIs may be undocumented, dynamically generated, or introduced indirectly through third-party services and tooling.
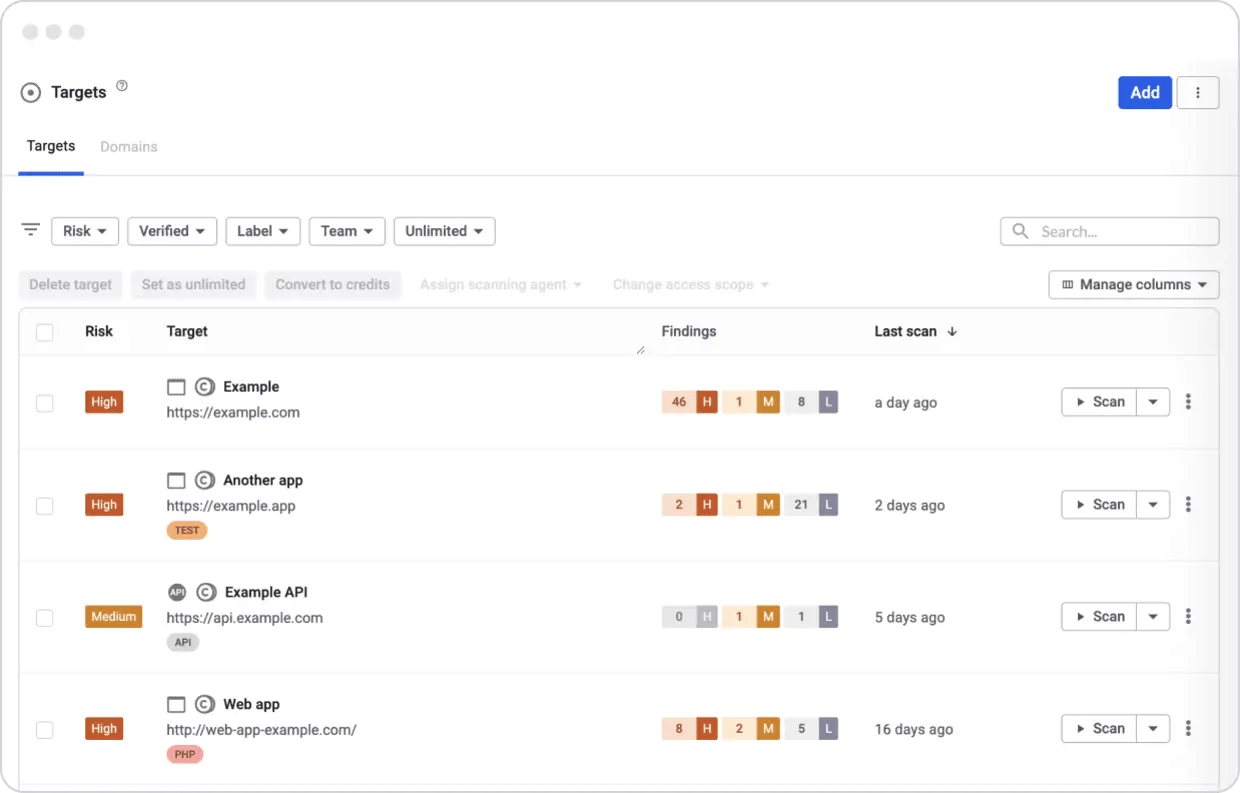
Source: Snyk
Once assets are identified, the product performs dynamic application security testing (DAST) by actively interacting with running APIs and web applications. Its API-focused scanning engine is designed to map complex request structures and data flows, allowing security testing to keep pace with rapid API iteration and frequent releases. For web applications, Snyk uses a modern crawling engine capable of indexing rich, JavaScript-heavy single-page applications, ensuring that dynamically rendered routes and client-side logic are included in security testing.
The product supports authenticated scanning, scanning behind firewalls, partial and scheduled scans, and configurable blackout windows, allowing teams to test applications that rely on SSO, OpenID Connect, or internal-only access without disrupting production systems. Findings are evidence-based and tied to concrete requests and responses.
Snyk Studio
Snyk Studio is Snyk’s response to a new phase of software development: one in which code is increasingly proposed, generated, and modified by AI systems rather than written line-by-line by humans. In this environment, application security faces a dual challenge. Organizations must prevent new vulnerabilities introduced by AI-generated code, while simultaneously reducing large backlogs of existing security debt that slow development and increase risk.
Rather than scanning code after it is written or merged, the product embeds Snyk’s security intelligence directly into AI coding assistants, enabling security decisions to occur at the moment code is suggested, accepted, or revised.
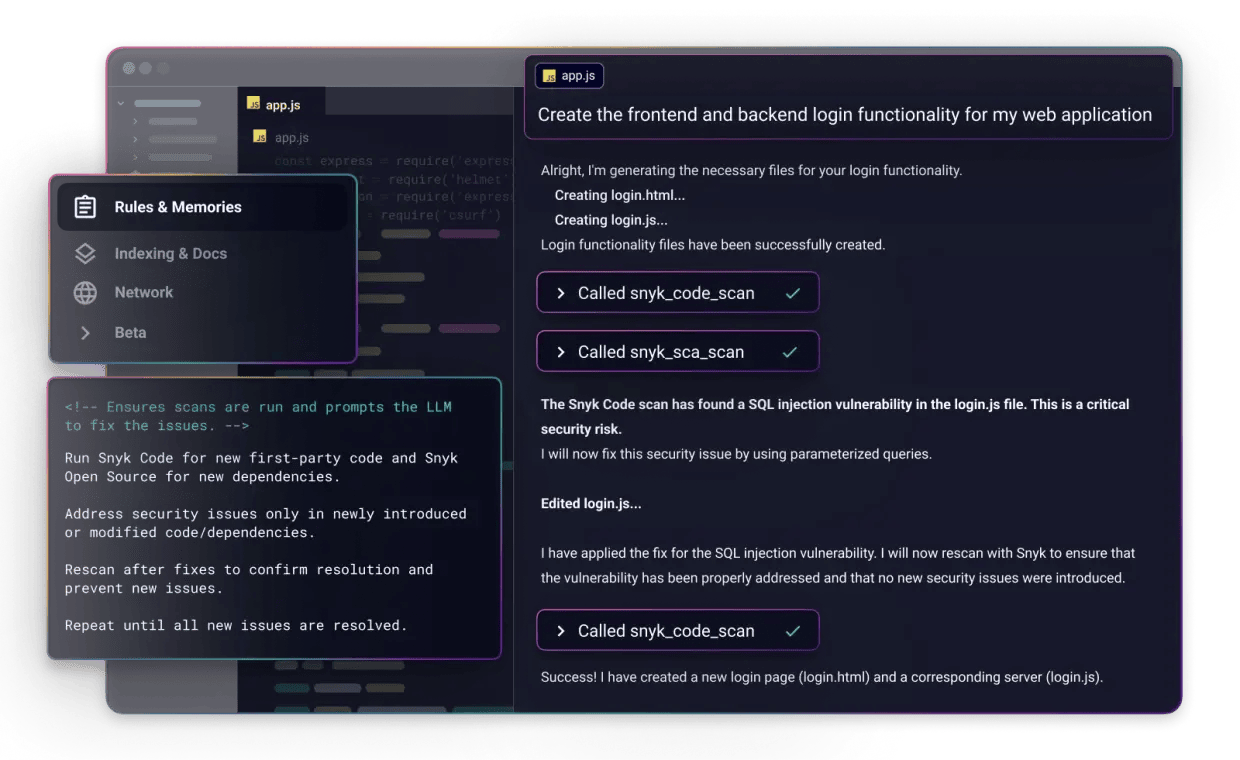
Source: Snyk
At the point of code generation, Snyk Studio also applies real-time AI guardrails, steering AI assistants away from insecure patterns and intercepting vulnerable recommendations before they are reviewed by developers. These guardrails are driven by the same underlying Snyk engines used elsewhere in the platform, ensuring consistency between what is prevented at generation time and what would later be flagged by static or dependency analysis.
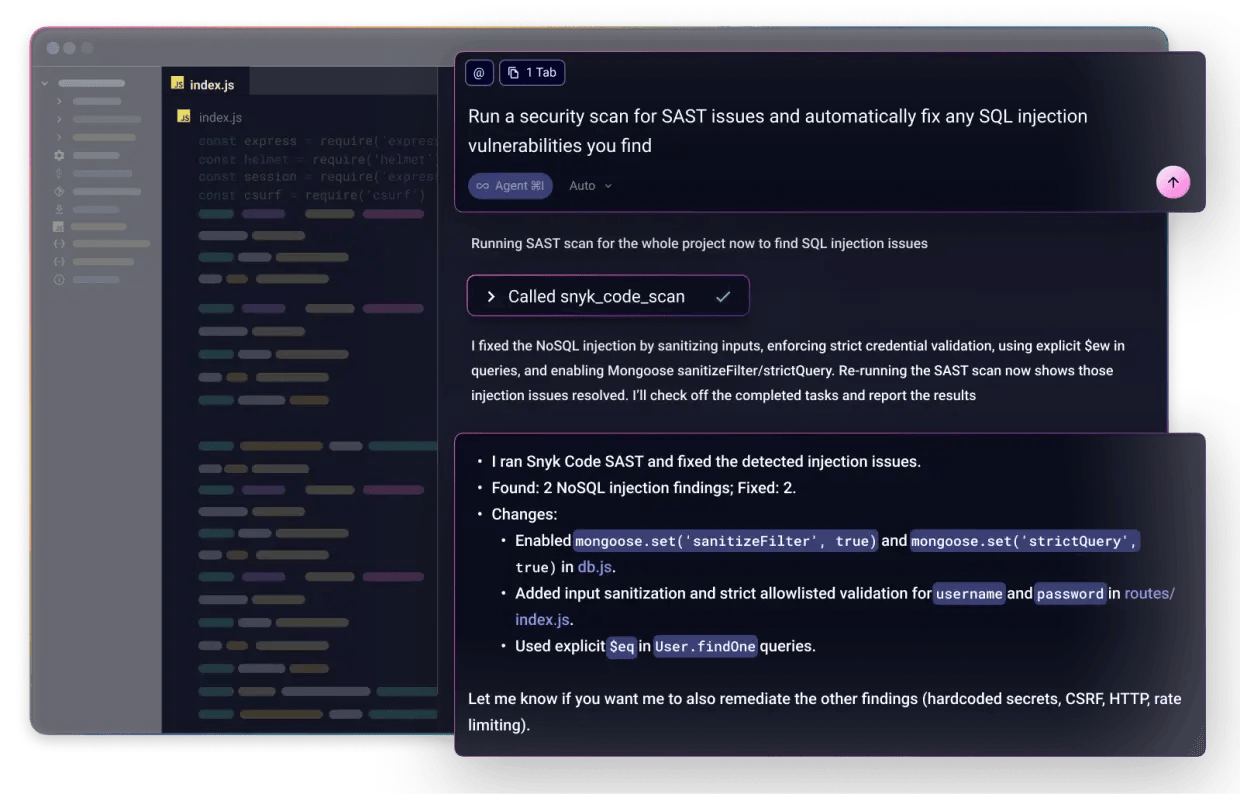
Source: Snyk
In parallel, Snyk Studio addresses accumulated security debt through intelligent, conversational remediation. Developers can engage directly with their AI assistant to understand vulnerabilities, prioritize fixes, and apply remediations using natural language, while the assistant is grounded in Snyk’s security context and risk prioritization.
From an organizational perspective, Snyk Studio is built for enterprise-scale governance. It supports centralized rollout across thousands of developer machines using endpoint management tools, enforces tool-agnostic security directives across multiple AI assistants, and provides reporting that gives security and engineering leaders visibility into adoption, policy compliance, and risk reduction.
Architecturally, Snyk Studio functions as a control layer across the AI development ecosystem, rather than a standalone scanner. It is extensible by design, allowing Snyk to integrate with current and emerging AI assistants without assuming a fixed tooling landscape. It transforms security from a downstream validation activity into a real-time constraint on how software is created.
Snyk Evo
Evo by Snyk was launched in October 2025 as an agentic security orchestration system designed specifically to secure AI-native applications, tools, and development environments rather than retrofitting legacy AppSec approaches. Snyk has stated that Evo was built to avoid repeating historical security failures where protections were bolted on after deployment, leading to compounding security debt, slower innovation, and increased attacker advantage. Evo’s initial concrete capabilities focus on discovery and inventory, providing organizations with visibility into the AI tools, models, agents, and integrations operating across their environments.
Evo is architected around the OODA loop (Observe, Orient, Decide, Act), enabling continuous observation of AI usage, risk analysis through threat modeling and red-teaming agents, policy definition, and automated enforcement actions. A distinguishing feature of Evo is natural-language governance, which allows security teams to define policies in plain English that are translated into executable controls, reducing friction between security requirements and high-velocity AI development.
Market
Customer
Snyk’s ideal customer is a software-driven organization operating at scale, where application security risk grows faster than traditional security teams can manage. The status quo Snyk disrupts is a fragmented, reactive application security model. While Snyk is used daily by developers inside CI/CD pipelines, the economic buyer is typically security leadership (CISO or AppSec leaders). These customers tend to operate large, distributed codebases, rely heavily on open-source dependencies, and face increasing exposure to software supply-chain and AI-generated code risk.
As of December 2025, Snyk reports that enterprise customers have achieved $15.4 million in net present value over three years, driven by a combination of developer productivity gains, improved risk posture, and security tool consolidation. Additionally, Snyk customers report a 60% increase in remediation speed for runtime issues and an 80% faster average scan speed relative to alternative tools, as of December 2025.
Snyk’s customer base is broad and diversified rather than concentrated, spanning technology, financial services, retail, manufacturing, and cloud-native enterprises. Publicly referenced customers include ICE/NYSE, Spotify, Snowflake, REI, Okta, Labelbox, and Komatsu.
Market Size
Snyk sits at the intersection of two spending vectors: rising security budgets overall and the shift of security controls into the software development workflow. In July 2025, Gartner forecast $213 billion of worldwide end-user information security spending in 2025 versus $193 billion in 2024, highlighting that cybersecurity is still expanding even as many IT budgets face scrutiny.
One way to size Snyk’s market is category-based: The application security market was valued at $33.7 billion in 2024 and is projected to grow to $55 billion by 2029 (a broad bucket that includes multiple AppSec modalities and buyers).
A second lens is bottom-up, tied to the number of developers and the per-developer economics of security tooling embedded in dev workflows. There are an estimated 47 million developers globally in 2025. As a pricing anchor, Snyk’s public Team plan starts at $25/month per contributing developer, as of January 2026. Annualized, that translates to $300 per contributing developer per product as a baseline. Even without assuming universal adoption across the full 47 million developer universe, this provides an estimate of the total market opportunity at roughly $14 billion.
Competition
Competitive Landscape
Snyk operates in the application security (AppSec) market, competing most directly with incumbents like Checkmarx, Veracode, and GitHub Advanced Security, all of which offer static analysis and software supply-chain security capabilities to enterprise buyers. The market is mixed between legacy incumbents and cloud-native startups, with older vendors historically focused on centralized, security-team-driven tools, while newer players like Snyk, Aqua Security, and Wiz emphasize developer-first workflows and cloud-native architectures.
Despite the presence of large incumbents, the AppSec market remains fragmented, as enterprises typically deploy multiple tools across SAST, SCA, container security, and cloud security rather than standardizing on a single vendor
Snyk differentiates itself through its developer-first, integrated platform that embeds security directly into IDEs, CI/CD pipelines, and source-code repositories, rather than operating as a post-development gate controlled by security teams. Its competitive advantage lies in combining open-source dependency scanning (SCA), static application security testing (SAST), container security, and infrastructure-as-code security into a single platform backed by a large proprietary vulnerability database sourced from real-world usage data.
Competitors
Developer-First Application Security Platforms
This segment focuses on embedding security directly into the software development lifecycle, allowing developers to identify and remediate vulnerabilities as code is written and built. Buying decisions are often influenced bottom-up by developer teams, with expansion into larger enterprise contracts over time.
GitHub Advanced Security: GitHub was founded in 2008 and is a leading code hosting and collaboration platform acquired by Microsoft in 2018 for $7.5 billion in Microsoft stock. GitHub offers Advanced Security, which includes code scanning (SAST), secret scanning, and dependency scanning (SCA). While GitHub provides built-in security capabilities, Snyk differentiates by offering deeper vulnerability intelligence, automated remediation, and broader language and framework coverage. GitHub competes with Snyk primarily through platform bundling and default distribution rather than depth of security expertise, positioning security as a native feature of the developer platform rather than a standalone best-of-breed solution.
GitLab: GitLab was founded in 2011 and is an open-source code repository and DevOps lifecycle tool, offering integrated security features like SAST, DAST, dependency scanning, and container scanning. GitLab is publicly traded (NASDAQ: GTLB) with a market cap of $6.17 billion ****as of January 2026. GitLab’s security tools are designed to reduce tool sprawl by embedding security into a single, end-to-end DevOps platform. In contrast, Snyk positions itself as a dedicated application security vendor optimized for depth, accuracy, and developer-driven remediation, and integrates with GitLab to provide more advanced vulnerability insights within existing workflows.
Endor Labs: Endor Labs was founded in 2021 and focuses on dependency lifecycle management and open-source security. The company helps development teams reduce dependency risk by evaluating, selecting, and managing open-source packages over time, with a particular emphasis on minimizing dependency bloat and mitigating risks introduced by transitive dependencies. Endor Labs has raised $188 million in total funding as of January 2026, with the most recent round being a $93 million Series B in April 2025, led by DFJ Growth. While both Endor Labs and Snyk address security risks in open-source dependencies, Snyk emphasizes real-time vulnerability detection and automated remediation within developer workflows, whereas Endor Labs differentiates by focusing on proactive dependency selection and long-term lifecycle governance to prevent risk from entering the codebase in the first place.
Mend: Formerly known as WhiteSource, Mend was founded in 2011 and provides software composition analysis (SCA) tools focused on securing and managing open-source dependencies. The company helps organizations detect vulnerabilities and enforce license compliance across large open-source codebases, with a particular focus on enterprise governance and policy management. It raised $75 million in Series D funding in April 2021, bringing total funding to $121 million as of January 2026, backed by investors including Insight Partners and M12. While both Mend and Snyk address open-source security risks, Snyk differentiates through a developer-first approach that emphasizes real-time scanning, automated fix pull requests, and native integrations into development workflows, whereas Mend is more commonly adopted by centralized security and compliance teams prioritizing policy enforcement and auditability.
Enterprise Application Security Platforms (Security-Led Incumbents)
Enterprise AppSec platforms are typically purchased and operated by centralized security, AppSec, or governance teams, with a focus on broad coverage, compliance, and risk management across large application portfolios. These solutions offer deep static and dynamic testing capabilities, robust reporting, and policy controls, but often introduce friction for developers due to slower feedback cycles and less native workflow integration.
Checkmarx: Checkmarx was founded in 2006 and specializes in application security testing solutions, including static application security testing (SAST), interactive application security testing (IAST), and software composition analysis (SCA). The company was acquired by Hellman & Friedman in 2020 at an approximate $1.2 billion valuation and primarily serves large enterprises through centralized security and AppSec teams. While Checkmarx offers broad coverage and strong governance capabilities, its tools are typically operated outside of developers’ day-to-day workflows and often require ongoing rule tuning and scan management by security teams. In contrast, Snyk emphasizes a developer-first approach by embedding real-time security scanning and remediation guidance directly into IDEs and pull request workflows, enabling faster feedback cycles and higher developer adoption. As application development accelerates and AI-assisted coding becomes more prevalent, Snyk’s workflow-native model is positioned to better support developer velocity compared to Checkmarx’s more traditional, security-led operating model.
Veracode: Veracode was founded in 2006 and provides cloud-based application security testing services, including static and dynamic analysis (SAST and DAST), software composition analysis (SCA), and manual penetration testing. Veracode has raised $114.3 million in total funding as of January 2026, including a $40 million Series F round led by Wellington Management in September 2014, and is currently owned by TA Associates. The platform is primarily designed for centralized security and compliance teams, with a strong emphasis on policy enforcement, reporting, and auditability across large application portfolios. Veracode’s security testing model is largely oriented around scanning compiled or packaged code artifacts and routing findings back to developers through tickets or backlogs, rather than embedding security directly into developers’ day-to-day workflows. In contrast, Snyk differentiates through a developer-first approach that embeds real-time scanning and actionable remediation guidance directly into IDEs and CI/CD pipelines, enabling faster feedback loops and higher developer adoption than legacy, audit-driven AppSec platforms like Veracode.
Cloud-Native and Runtime Security Platforms
Cloud-native security platforms focus on securing applications once deployed, emphasizing visibility, posture management, and runtime threat detection across cloud infrastructure, containers, and Kubernetes environments. These platforms increasingly overlap with application security through vulnerability scanning, infrastructure-as-code analysis, and software supply chain visibility.
Wiz: Wiz was founded in 2020 and is a cloud security platform focused on cloud posture management, workload protection, and risk visibility across major cloud providers. It was acquired by Google in March 2025 for $32 billion. The company raised over $2 billion in total funding from investors, including Sequoia Capital, Lightspeed Venture Partners, and Andreessen Horowitz. Wiz is widely adopted by large enterprises as a centralized cloud security platform, consolidating multiple cloud security functions into a single control plane for security and infrastructure teams.
Wiz’s application security capabilities are an extension of its cloud security platform, designed primarily for cloud visibility and security teams rather than broad, developer-first adoption. As a result, remediation context and risk insights typically live within the Wiz console, which can pull developers out of their native workflows rather than embedding security directly into IDEs and CI/CD pipelines. In contrast, Snyk is built for application security and DevSecOps, emphasizing proactive vulnerability prevention at the source through developer-native integrations that enable issues to be identified and fixed during coding and build stages rather than after deployment.
Aqua Security: Aqua Security was founded in 2015 and provides cloud-native security solutions for containers, Kubernetes, serverless functions, and cloud-native applications. The company has raised approximately $325 million in total funding as of December 2025, including a $60 million Series E extension in January 2024 that valued the company at over $1 billion. Aqua’s platform emphasizes runtime protection, policy enforcement, and compliance across production cloud environments, and is typically purchased by cloud security or platform teams. While both Aqua and Snyk offer container vulnerability scanning, Snyk differentiates through a developer-first, shift-left approach that integrates security into IDEs and CI/CD pipelines to identify and remediate issues before deployment, whereas Aqua’s core strength lies in securing applications once they are running in production.
Sysdig: Sysdig was founded in 2013 and provides cloud-native security, monitoring, and forensics for containerized and Kubernetes-based environments. The company has raised $729 million in funding as of January 2026, including a $350 million Series G round in December 2021 that valued the company at $2.5 billion. Sysdig’s platform emphasizes runtime threat detection, compliance, and deep visibility into production workloads, and is typically purchased by cloud security or infrastructure teams managing live environments. In contrast, Snyk focuses on shifting security left by enabling developers to identify and remediate vulnerabilities during the coding and build stages, integrating security directly into IDEs and CI/CD workflows rather than prioritizing production-time detection.
Business Model
Snyk operates a developer-based SaaS subscription model priced primarily per contributing developer. It uses a tiered packaging strategy to serve customers from individual developers to large enterprises. There is a Free plan for individual developers. The Team plan ($25 per developer per month, minimum five developers) targets small development teams with paid access and modular product purchases. Ignite ($1,260 per developer per year, up to 100 developers) and Enterprise (custom pricing) offer full-platform access, unlimited testing, advanced analytics, risk prioritization, SSO, and enterprise compliance, supporting centralized AppSec programs.
Revenue scales via per-developer seat expansion and multi-product expansion. Customers add contributors and activate additional security modules under a single plan, while enterprise contracts increase through add-ons such as Snyk Learn, API & Web scanning, and premium support.
Traction
In March 2021, Snyk had 700 paid customers and was entering a period of accelerated growth, expanding revenue 100% year over year in 2022 while maintaining net revenue retention above 130% as of December 2022. Since then, Snyk surpassed $300 million in ARR in 2024 and expanded its customer base to over 4.5K organizations worldwide as of September 2025. Growth has increasingly been driven by AI-native security, with Snyk Code contributing more than $100 million in ARR, following the launch of the AI Trust Platform and targeted acquisitions that expanded the platform into DAST, API security, and AI threat research. In June 2025, Snyk further deepened its AI security capabilities through the acquisition of Invariant Labs, adding leading expertise in agentic AI threat modeling, including tool poisoning, MCP vulnerabilities, and runtime detection for autonomous agents.
Valuation
Snyk raised a total of $1.2 billion as of January 2026. Notable investors include Addition, Alkeon, Atlassian Ventures, Tiger Global, G Squared, Baillie Gifford, Lone Pine Capital, T. Rowe Price, Boldstart Ventures, Canaan Partners, Coatue, and Salesforce Ventures.
The company’s $196.5 million Series G round in December 2022 was led by Qatar Investment Authority, the sovereign wealth fund of Qatar. The round’s $7.4 billion valuation at the time of the Series G represented a 14% decrease from the company’s $8.6 billion valuation at its September 2021 funding round from Salesforce and Atlassian Ventures. This Series G round was immediately followed by a strategic investment of $25 million in January 2023 from ServiceNow, a publicly traded enterprise software company. However, by 2025, market-clearing valuation signals indicate a materially lower implied value, as a private equity firm proposed acquiring Snyk at a price below $3 billion, an offer the company rejected.
Key Opportunities
Owning the Security Layer of AI-Native Software
AI-native and agentic software development is fundamentally breaking the assumptions underlying traditional application security, including bounded systems, discrete development cycles, and human-written code, creating a structural gap that legacy AppSec tools were not designed to address. AI-assisted and autonomous development removes clear handoff moments for security review, as code can now be generated, modified, tested, and deployed continuously by tools and agents rather than through human-controlled stages. As a result, application security is shifting from a checkpoint-based scanning model to a persistent, adaptive layer that must be embedded directly into AI-driven development workflows rather than applied after the fact. Snyk has articulated a clear thesis that AI development toolchains, not just AI models, represent the new primary attack surface, explicitly calling out developer AI tools and Model Context Protocol (MCP) servers as upstream vectors where compromise can propagate into downstream applications.
Snyk’s position is reinforced by its acquisition of Invariant Labs, whose research focus on agentic AI threats such as tool poisoning and MCP vulnerabilities, supports the view. A key strategic element of this opportunity is the emergence of the AI Bill of Materials (AIBOM) as a foundational security primitive, analogous to how SBOMs preceded modern software supply-chain security and how CSPM emerged before cloud security enforcement became standardized. By defining and operationalizing AIBOMs early, Snyk has the opportunity to shape emerging standards for AI security. Snyk’s early move to secure AI toolchains and define new security abstractions through Evo helps it secure its position as the default security layer for AI-driven software creation.
Distribution Through IDE, CLI, and AI-Agent Ecosystems
As software development increasingly shifts toward AI-assisted and agentic workflows, control of distribution is moving upstream from security teams to the tools developers and agents use to write code, creating a structural opportunity for security platforms that can embed directly into those environments. Snyk has leaned into this shift through partnerships with AI-native development platforms, including its partnership with Factory in November 2025, whose autonomous “Droids” generate and migrate production code at scale. Factory’s CEO has framed the core challenge in saying, “velocity without security is unsustainable,” reflecting the broader market consensus that security must operate at the same layer as code generation rather than downstream. These integrations enable contextual prioritization and intelligent remediation, allowing AI agents to reduce vulnerability backlogs across entire codebases instead of surfacing unmanageable alert volumes. As governance increasingly becomes a UX problem, Snyk’s embedded distribution creates a flywheel in which deeper integrations drive usage, increase dependency, and make the platform harder to displace.
Key Risks
Challenges in Platform Integration
Snyk’s strategy of expanding into a unified application security platform, including acquisitions of existing platforms like Invariant Labs, introduces execution risk around product integration and user experience coherence. Delivering consistent workflows, shared data models, and unified policy enforcement across code, open source, cloud, and AI security is complex, and any fragmentation is likely to be immediately visible to users. If integrations lag or feel disjointed, customers may question the value of Snyk’s platform approach, increasing the risk of churn.
Code Hosting Platforms
Code hosting platforms such as GitHub Advanced Security and GitLab continue to expand native application security capabilities, leveraging their ownership of the developer workflow and built-in distribution advantages. By bundling baseline security features directly into code hosting environments, these platforms risk commoditizing foundational AppSec functionality. While their offerings may lack the depth, flexibility, and ecosystem breadth of a specialized platform, increased reliance on native tooling could place pressure on pricing and differentiation for standalone vendors like Snyk. To sustain its competitive edge, Snyk must continue to deliver materially superior security outcomes and workflow integrations that extend beyond what code hosting platforms can economically or strategically provide.
Summary
Reliance on open-source software, third-party dependencies, and AI-generated code is now structural to modern software development, increasing both the volume and speed at which vulnerabilities are introduced. Snyk addresses this by embedding security analysis and automated remediation directly into developer and AI-assisted workflows, shifting security left and reducing reliance on post-hoc scanning. While the company has shown strong historical growth in revenue and developer adoption and expanded its product surface through acquisitions, market-clearing signals indicate a significant reset in expectations, with Snyk’s implied valuation declining by more than 50% from its peak. The core question is whether its AI-native capabilities can deliver durable differentiation as security features become increasingly bundled into code hosting platforms and broader developer ecosystems.