Thesis
IT environments are growing increasingly complex, with massive user bases, countless connected devices, and assets spanning on-premises systems and cloud services. Organizations face mounting pressure to establish asset visibility and proactive security posture management. As enterprises increasingly depend on cloud infrastructure and SaaS solutions, they face more incidents like the Microsoft data leak in 2023 where 38TB of data were exposed, including passwords, private keys, and 30K internal Teams messages. These breaches serve as a stark reminder of the importance of strong SaaS security posture management (SSPM), which focuses on continuously monitoring and securing SaaS applications. Vulnerabilities can include issues like overly permissive access and inadequate monitoring. Without proper SSPM controls in place, misconfigurations like these can go undetected, putting critical corporate data at risk.
Modern enterprises operate across varied ecosystems that include on-premises infrastructure, cloud resources, virtual machines, and flexible Bring Your Own Device (BYOD) policies. Companies are rapidly adopting SaaS solutions, with the average number of software licenses used in large enterprises growing from 317 in 2021 to 473 in 2023. However, approximately 53% of these licenses go unused—underscoring the urgent need for better management and visibility tools.
Compounding these challenges is the rapid shift to remote and hybrid work models. With over 100 million workers globally engaging in hybrid work in 2024, and more than 82% of companies already having at least 10% of their workforce operating in a hybrid model, organizations must secure an ever-expanding array of endpoints. Endpoints, including desktops, laptops, mobile phones, and servers, act as the primary access points to an organization’s network and are prime targets for cyber threats. By 2026, 78% of employers anticipate widespread hybrid work adoption, further driving the need for scalable security management solutions.
Simultaneously, budget constraints are leading to a trend of vendor consolidation and reduced budget growth. Security budgets have increased by only 8% in 2024—a notable decline from the double-digit growth seen in previous years—with a quarter of Chief Information Security Officers reporting flat budgets and 12% experiencing reductions. This financial pressure forces organizations to optimize spending while maintaining robust security postures.
That’s where Axonius comes in. Axonius is an asset management platform. Serving as a central hub, Axonius aggregates and normalizes security data from over 1.1K diverse business, IT, and security sources via APIs as of February 2025. By leveraging adapter-based data collection and graph-based mapping, Axonius provides a unified view of an organization’s entire asset landscape—including endpoints, cloud services, and SaaS applications—while automatically identifying security gaps and enforcing policies. Rather than replacing specialized security tools such as endpoint protection, firewalls, or vulnerability scanners, Axonius complements them by offering an overarching analysis of the overall security posture.
Founding Story

Source: FINSMES
Axonius was founded in 2017 by Dean Sysman (CEO), Ofri Shur (CTO), and Avidor Bartov (Chief Product Officer). The three longtime collaborators first worked together in the Israeli military. Sysman, a former intelligence officer in an elite Israeli Intelligence Corps unit, co-founded and served as CTO of Cymmetria, a YC-backed cyber deception company, and was featured in Forbes 30 Under 30 Israel in 2017. Shur, a graduate of the Taliot military academy, served eight years in the IDF intelligence corps, leading an R&D section before becoming CTO of Kayhut, a cybersecurity provider. Bartov, active in the Israeli cybersecurity community since age 13, became a leading penetration tester at BugSec by 17 and later served as a researcher and team lead in Unit 8200. Sysman and Bartov hold B.Sc. degrees in Computer Science, while Shur earned a BSc in Physics and Mathematics.
The idea for Axonius emerged when Sysman, while deploying Cymmetria’s security solutions at a major retailer, discovered the company lacked a clear inventory of its devices. When asked which deployment tools they used — SCCM, Tanium, ePO, Puppet, or Chef — the response was simply, “Yes.” This highlighted a fragmented security landscape with multiple tools but no centralized visibility. Sysman likened it to a "Cambrian explosion" of devices, with gaps in asset visibility creating inefficiencies and security blind spots. Seeing the need for a unified solution, the founders built Axonius to consolidate asset management, providing comprehensive visibility and control. In one interview, Sysman explained that Axonius focused on foundational cybersecurity needs rather than chasing flashy innovations.
Axonius secured early funding from YL Ventures, with Sysman convincing investors that every connected device posed a security risk, yet organizations lacked visibility into their total inventory. As the company expanded, it strengthened its leadership team to drive product development. In 2021, Axonius launched AxoniusX, a research arm led by Amir Ofek as CEO of the division, to tackle complex IT and security challenges. As of 2025, Sysman remains CEO, with Shur as CTO and Bartov as Chief Product Officer.
Product
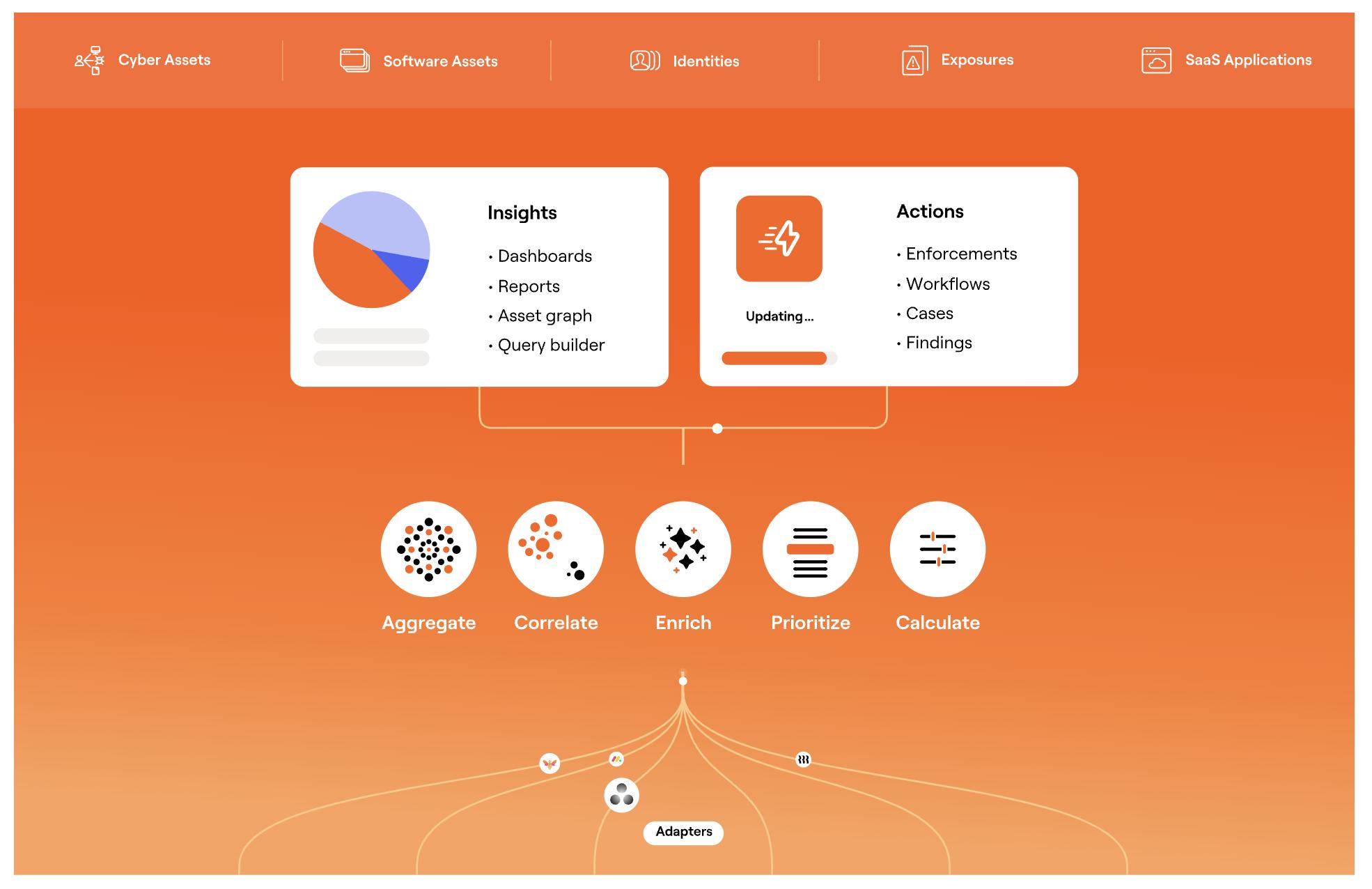
Source: Axonius
Axonius delivers asset visibility, risk assessment, and automated policy enforcement. As of February 2025, its flagship product is the Axonius Platform, an asset cloud that provides unified asset intelligence. Within the Platform, major focus areas include: Cyber Assets, Identity, Exposure, SaaS Applications, and Software Assets.
Some key terms in the cybersecurity asset management industry include:
Asset / Asset Inventory: A complete list of an organization’s resources, including devices, software, and cloud assets.
Adapter: A connector that integrates with third-party solutions to pull asset and configuration data.
Common Vulnerabilities and Exposures (CVE): Identified weaknesses in systems that could be exploited. Axonius helps organizations prioritize and automate vulnerability remediation.
IT Service Management (ITSM) / Configuration Management Databases (CMDBs): ITSM platforms, such as ServiceNow, manage IT services and use CMDBs to track assets and configurations.
Attack Surface: The sum of potential entry points that attackers can exploit within an organization’s network.
Product Overview
Source: Axonius
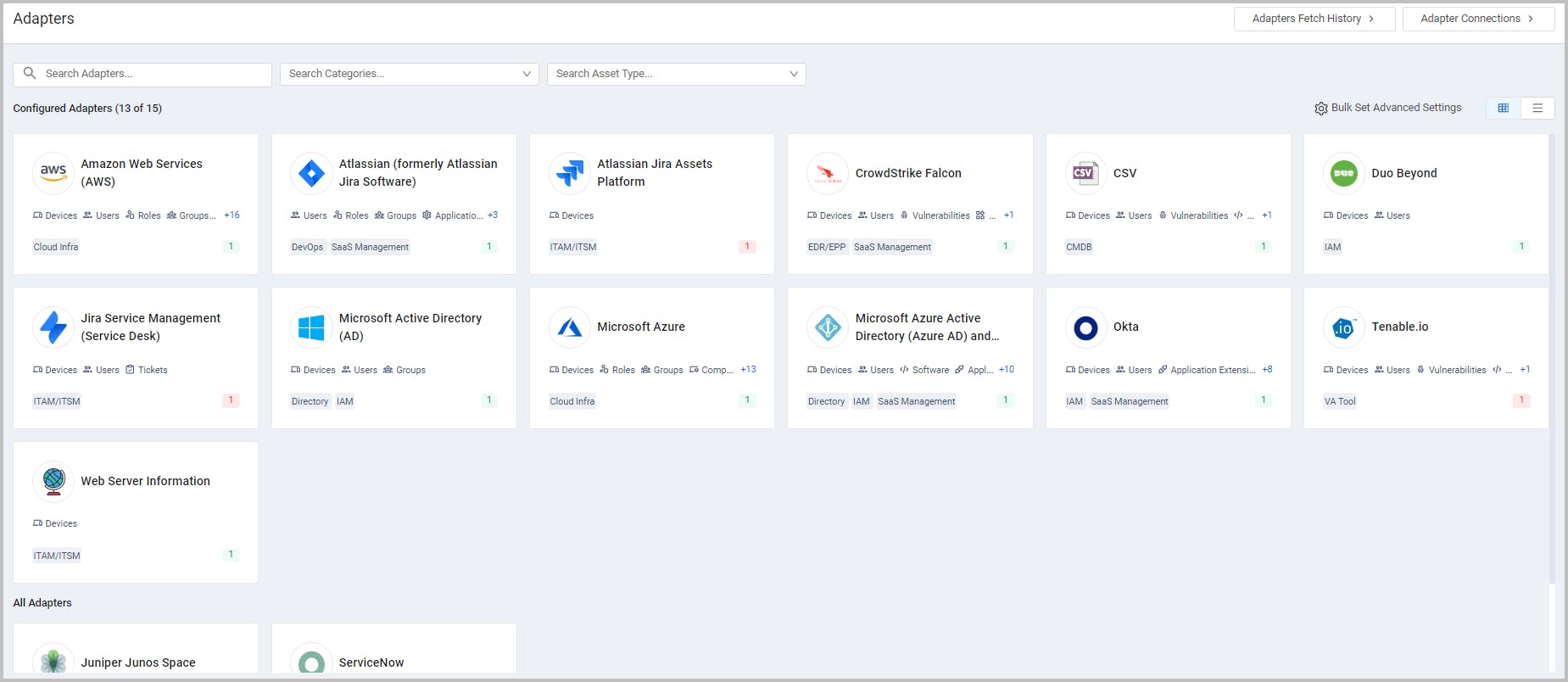
Axonius' adapter ecosystem is the foundation of its Cyber Asset Intelligence platform, seamlessly detecting and managing assets across diverse environments. Unlike traditional agent-based methods prone to missing shadow IT and evasion techniques, Axonius integrates with over 1.1K third-party solutions (e.g., AWS, CrowdStrike) to continuously gather and cross-correlate data from devices, users, software, and security configurations. Each adapter is represented by an intuitive Adapter Card displaying its logo, name, supported asset types, and connection status, enabling easy search and filtering. This comprehensive approach eliminates blind spots, identifies shadow IT, and ensures accurate data through automated updates within a customizable Discovery Cycle.
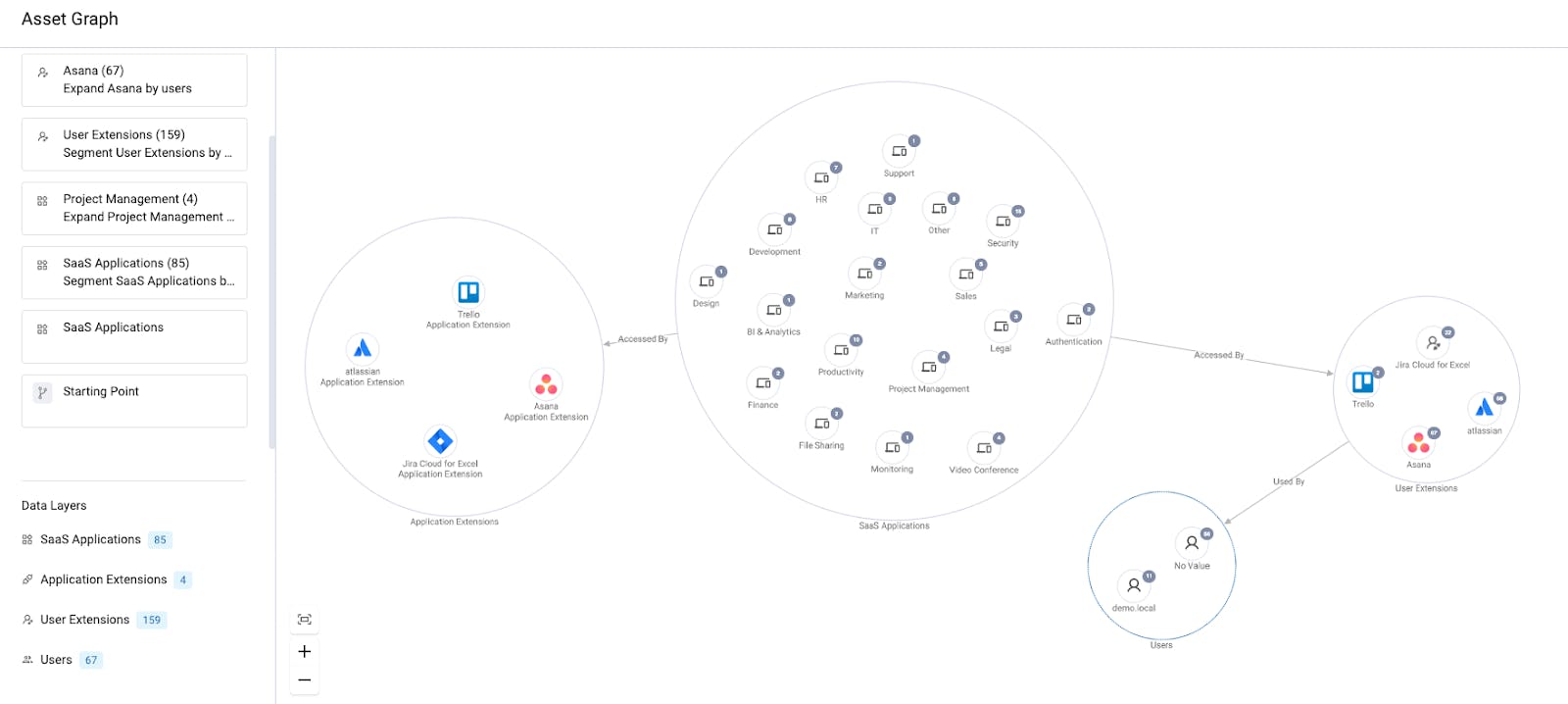
Source: Axonius
The Platform aggregates enriched data into an interactive Asset Graph, visualizing relationships across key categories: Compute (devices and virtual machines), Identity (user accounts), Applications (SaaS and installed software), and Infrastructure (firewalls and routers). This holistic view allows organizations to prioritize remediation based on asset risk and potential threat impact.
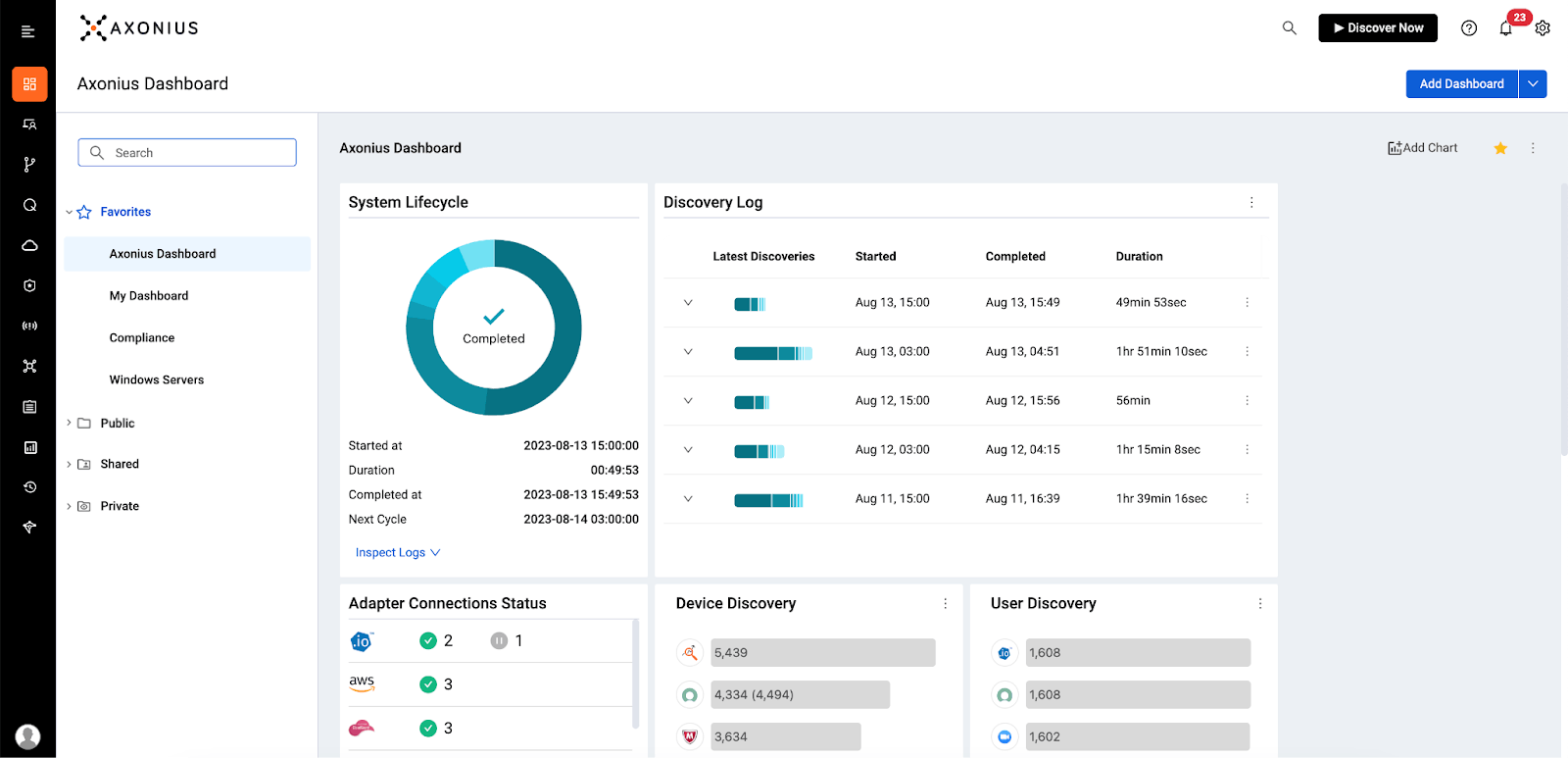
Source: Axonius
Advanced query capabilities — delivered through both a Query Wizard with AI assistance and a streamlined Basic mode—allow users to precisely filter and refine asset searches for compliance tracking. These queries power customizable Dashboards and detailed Reports that offer real-time insights into system health, performance, and policy adherence.
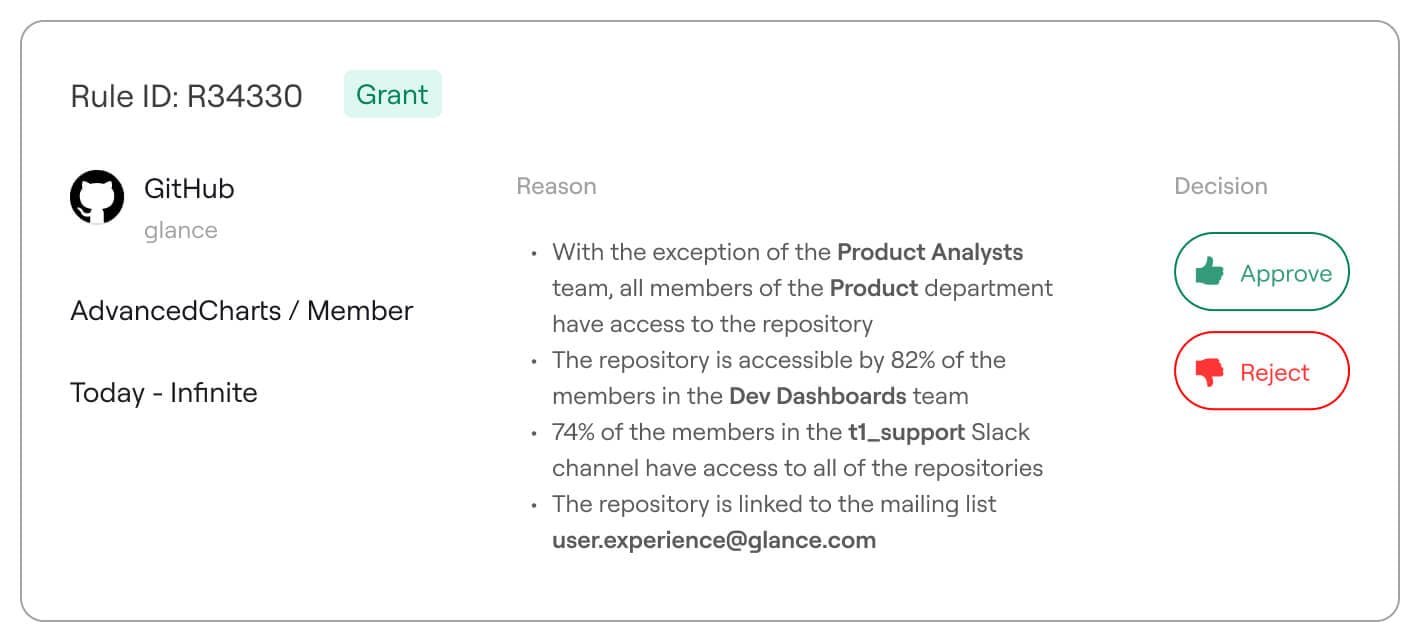
Beyond visibility, Axonius automates asset management and incident response. The platform monitors third-party system tickets from tools like ServiceNow, enabling security teams to track incidents, update tickets in real time, and analyze asset-specific remediation efforts. Its Policy Enforcement module streamlines security workflows by triggering actions such as ticket creation, asset enrichment, vulnerability scans, and device isolation.
The Findings Center centralizes alerts, system events, and activity logs, providing comprehensive asset performance visibility. Axonius’ Case Management system allows users to create cases directly from queries to address anomalies, such as unpatched vulnerabilities, streamlining remediation through automated Enforcement Sets.
Without proper compliance measures, organizations risk data breaches, legal penalties, and operational disruptions. Axonius assesses cloud security posture by analyzing asset configurations across public, multi-cloud, and hybrid environments, benchmarking implementations against industry standards like the Center for Internet Security (CIS) Benchmarks. It continuously identifies non-compliance issues and provides visibility into security gaps across major providers, including AWS, Azure, Google Cloud, and Oracle Cloud.
Cyber Assets
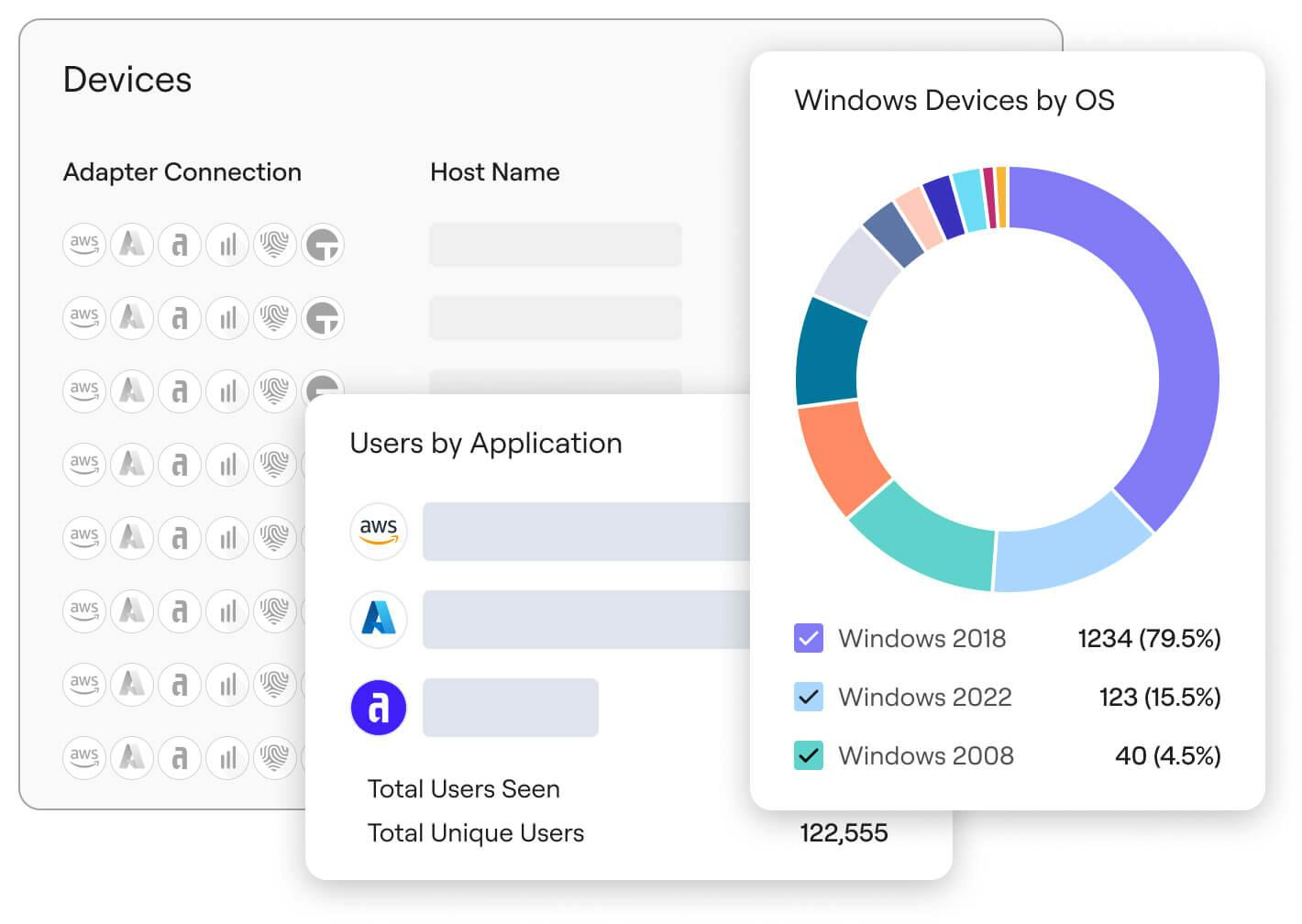
Source: Axonius
Axonius’ Cyber Assets solution structures static inventories into a more dynamic, unified view of an organization’s technology landscape. It normalizes, deduplicates, and enriches asset data from endpoints, cloud services, and on-premises systems. This unified model enables searches to identify configuration drifts, compliance gaps, and vulnerabilities, empowering teams to take informed action. Moreover, the platform automates policy enforcement and remediation with bi-directional integrations ensuring continuous verification of asset state, cost, and posture. By integrating enriched asset data with CMDB platforms, Axonius breaks down silos between security, IT, and risk teams — enabling a proactive cybersecurity posture.
Identity
Axonius’ Identity solution transforms fragmented identity data into actionable insights by unifying discovery, lifecycle management, governance, and security posture. This consolidated approach empowers organizations to break down silos, reduce sprawl, and swiftly act across the broader identity lifecycle—strengthening the resilience of their Identity Asset Management (IAM) programs.
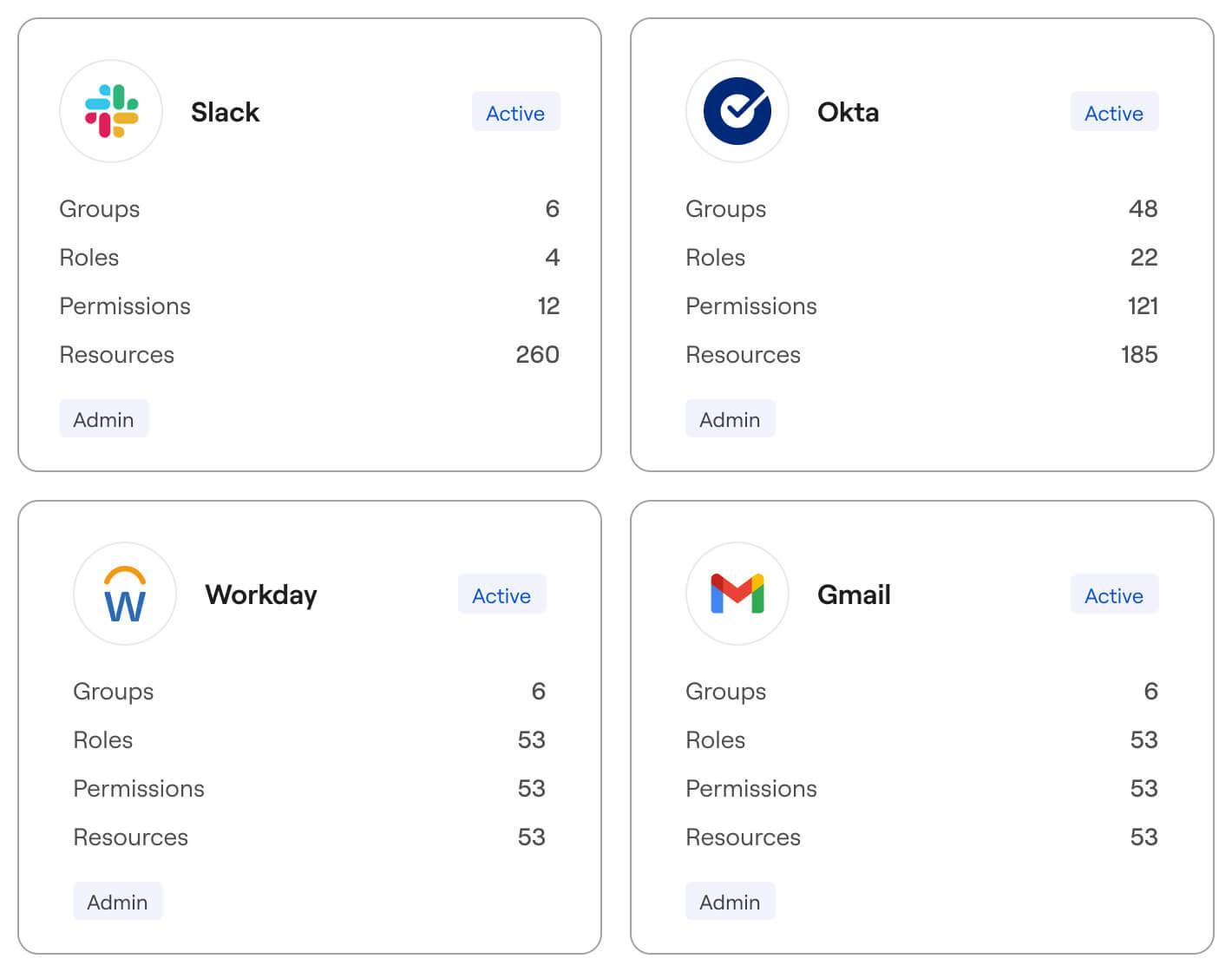
Source: Axonius
By continuously aggregating identity artifacts from each system and application, Axonius provides visibility into both human and machine accounts across cloud, on-premises, and hybrid environments. The platform synchronizes accounts, roles, policies, entitlements, and permission sets to ensure that no identity is missed, effectively illuminating blind spots.
Axonius also streamlines identity lifecycle management by orchestrating joiner, mover, and leaver scenarios in one place, which encompass the onboarding, internal movement, and departure of employees. This unified approach guarantees that changes cascade seamlessly across all systems, reducing operational overhead and ensuring consistent enforcement of security policies.
Insights into access patterns and entitlement calculations further enhance identity governance. Axonius enables organizations to right-size access, identify excessive permissions, and uncover policy gaps—empowering teams to optimize access rights and mitigate risks proactively. Continuous monitoring of multi-factor authentication coverage, weak controls, and policy conflicts ensures that vulnerabilities are addressed.
Source: Axonius
Leveraging AI-driven insights, the solution simplifies identity hygiene by recommending optimal policies and enforcing least privilege principles. This intelligent optimization minimizes orphaned accounts and streamlines governance, allowing IT and security teams to maintain a clean, efficient, and resilient identity environment.
Exposure
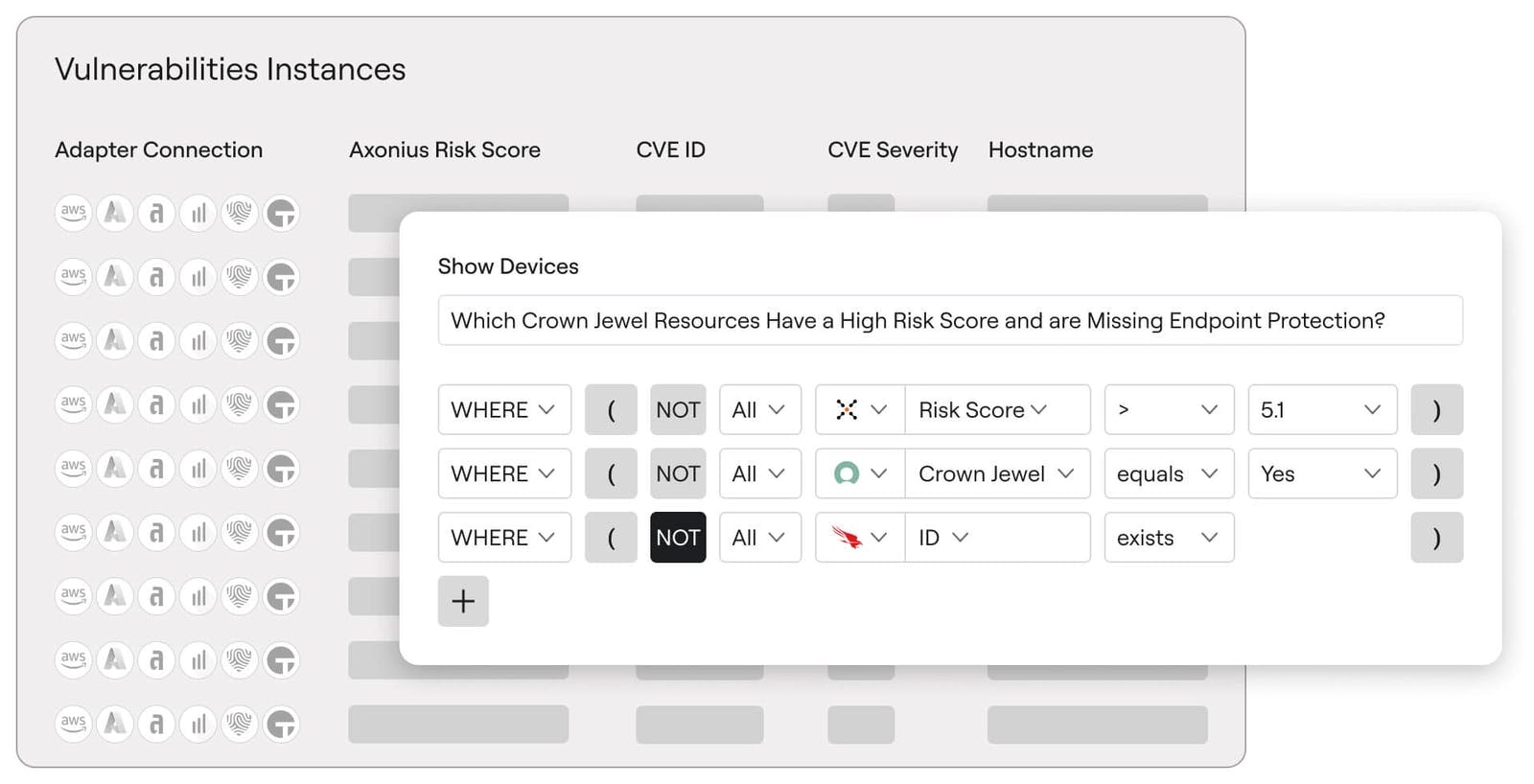
Source: Axonius
Axonius empowers organizations to take proactive control of their cybersecurity by unifying exposure findings across the entire IT and security ecosystem. By aggregating vulnerabilities, misconfigurations, and other risk indicators from disparate systems into one centralized view, the platform transforms fragmented data into a comprehensive, actionable risk landscape. This approach enables teams to quickly identify and address critical gaps before they escalate into full-blown exploits.
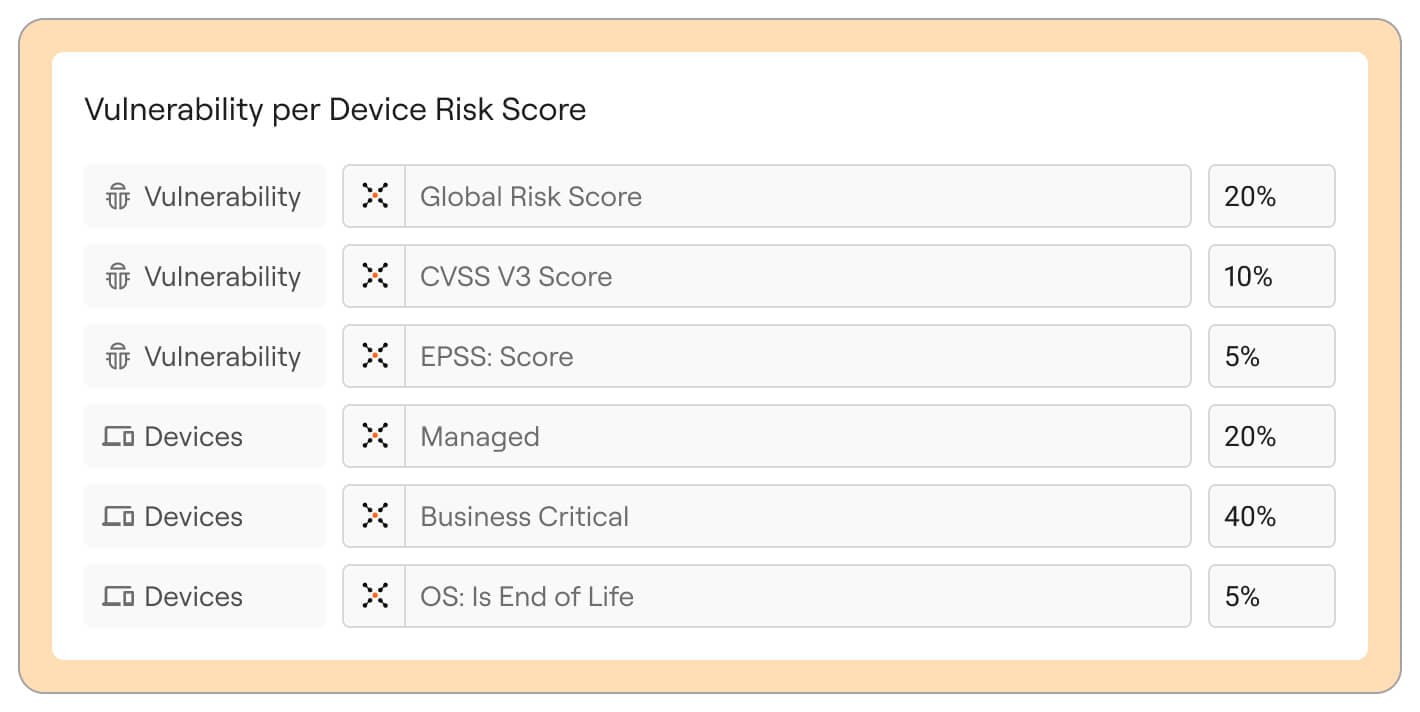
Source: Axonius
Axonius’ product continuously scans for a wide range of exposures—from vulnerable software and non-compliant devices to misconfigured applications and weak access controls. By integrating enriched asset context, Axonius maps the relationships between affected devices, identities, and infrastructure, allowing organizations to understand the full scope and potential impact of each risk. Dynamic risk scoring further refines this process by evaluating exposure, business impact, and exploitability, ensuring that remediation efforts are prioritized in line with organizational capacity and strategic objectives.
Axonius provides advanced public access modeling, which identifies vulnerable assets that could be exploited via external entry points such as load balancers, firewalls, and suboptimal subnet configurations. This capability enables organizations to anticipate and mitigate potential attack vectors from both inside and outside their networks.
SaaS Applications
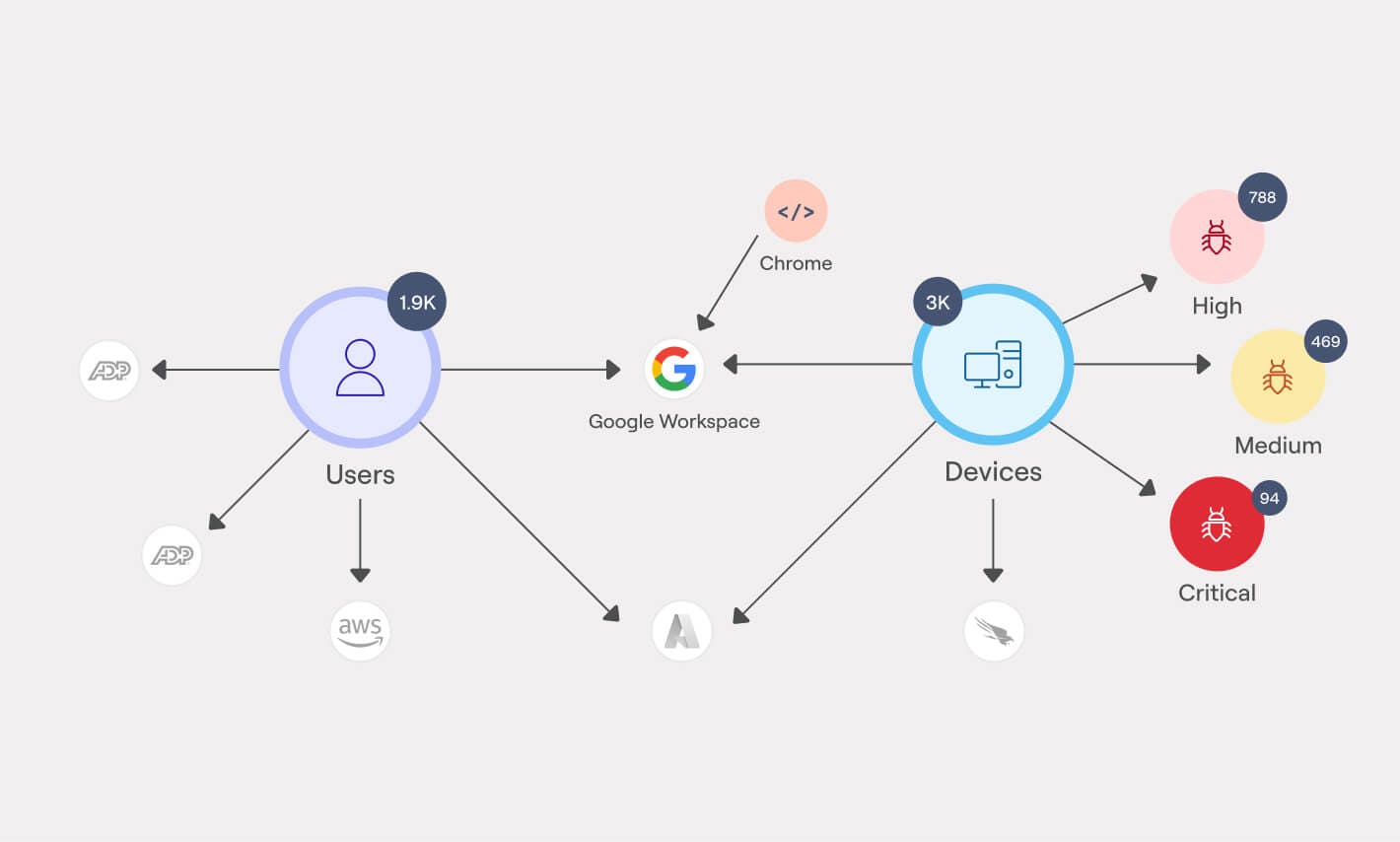
Source: Axonius
As organizations increasingly adopt SaaS applications to enhance productivity, Axonius’ SaaS Management solution helps mitigate security risks, noncompliance, and financial inefficiencies caused by untracked applications, unused licenses, and misconfigurations. Designed to combat shadow IT sprawl without increasing complexity, the platform continuously discovers both known and unknown applications, ensuring no asset or access pattern is overlooked.
By aggregating data from diverse sources, Axonius eliminates blind spots and exposes risky apps, unmanaged extensions, OAuth tokens, and non-compliant user behaviors.
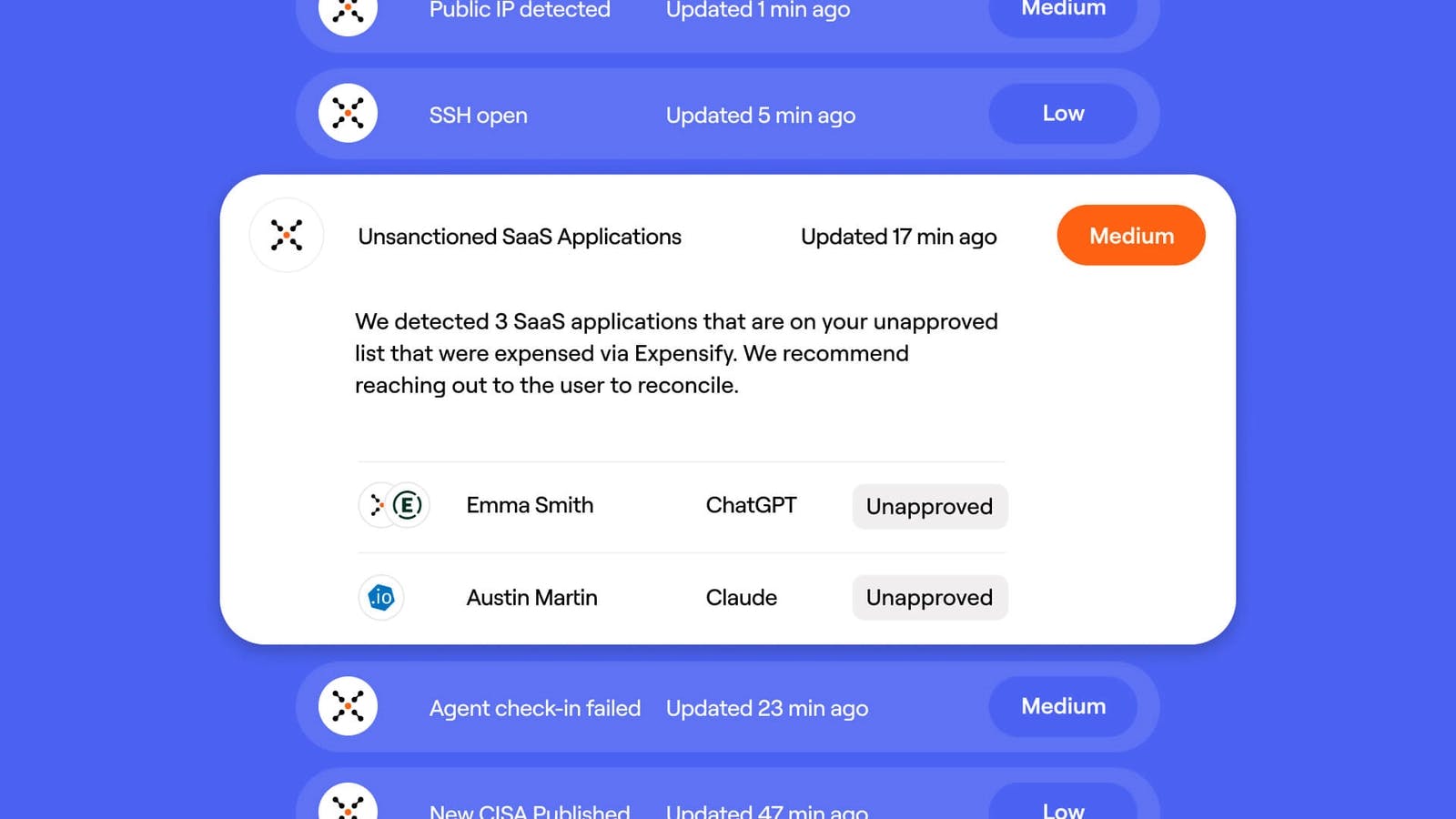
Source: Axonius
The platform also enhances operational efficiency by offering deep visibility into SaaS usage and licensing. Organizations can analyze license utilization, identify redundant applications, and detect shadow users to optimize spending and maximize value. Axonius’ intelligent data model maps SaaS applications to the underlying devices, identities, and infrastructure they interact with, revealing hidden connections that improve risk management and streamline operations.
Software Assets
This focus area delivers comprehensive, actionable visibility into software usage across the organization, empowering Security and IT teams to take control of unsanctioned software, end-of-life risks, and vulnerabilities. By automatically creating an inventory of software across all devices—whether managed or unmanaged — the platform replaces manual, outdated assessments with a unified software catalog that aggregates data from endpoint detection and response, endpoint management, and vulnerability tools without the need for additional agents or network scans.
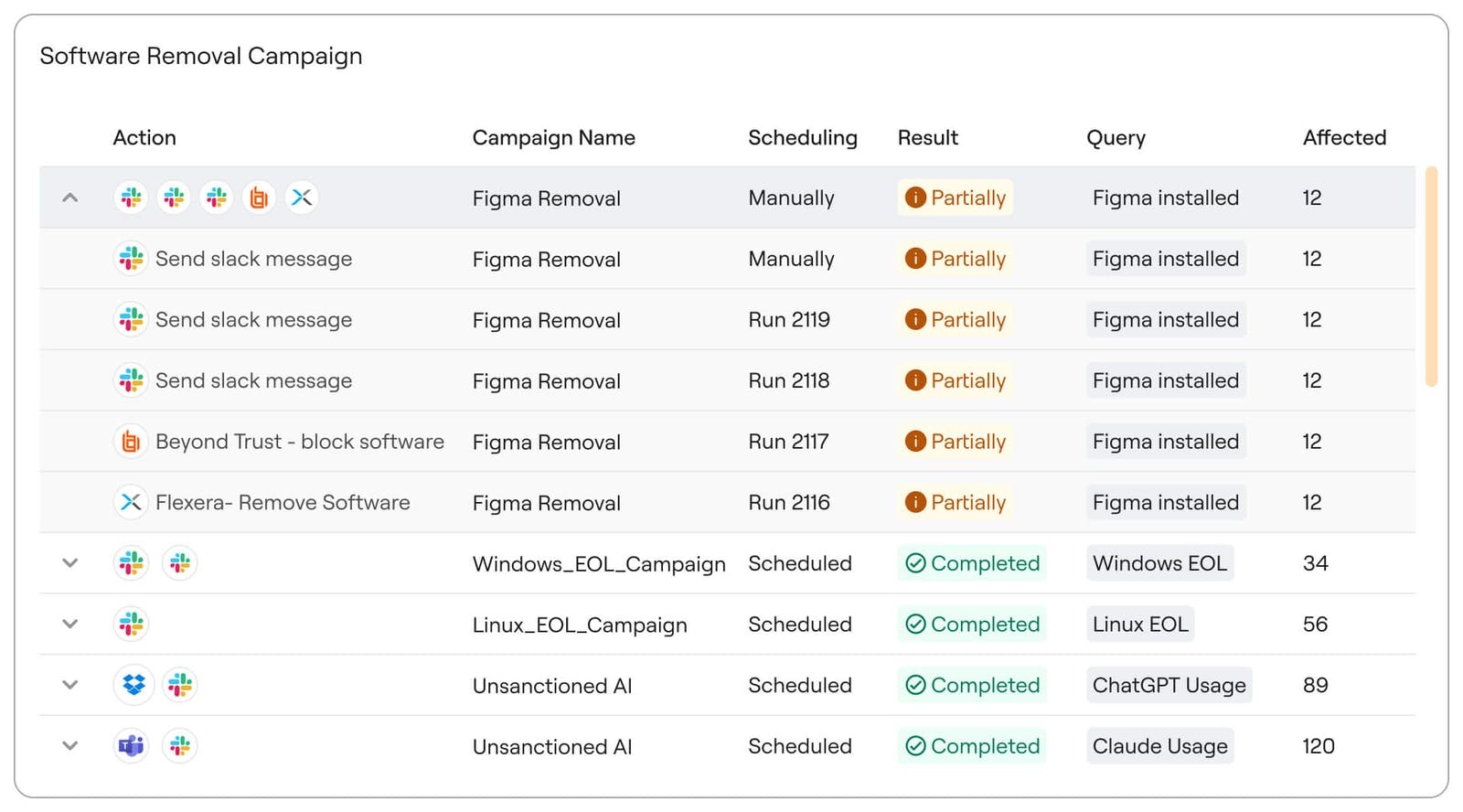
Source: Axonius
The solution provides full lifecycle management for software, offering end-to-end visibility from discovery through decommissioning. Organizations can track applications with custom tagging, gaining insights into user ownership and patch status. This contextual view enables teams to pinpoint where software is installed, assess its risk profile, and ensure compliance, ultimately streamlining IT operations and mitigating potential vulnerabilities before they become costly issues.
Market
Customer
Axonius helps organizations combat rising cyber threats, resource constraints, and the challenge of maintaining real-time IT visibility. Designed primarily for security and IT teams, Axonius serves customers like Epiq, Mindbody, InComm Payments, Safebreach, The New York Times, Schneider Electric, and AB InBev. It categorizes its clients across industries including healthcare, federal agencies, state and local governments, financial services, energy, manufacturing, and education.
Healthcare: The increasing use of Internet of Medical Things (IoMT) devices, electronic health records, and cloud applications has expanded the attack surface in healthcare, while regulations like HIPAA require continuous monitoring. Many hospitals still rely on manual asset tracking, leading to inefficiencies and security gaps. In extreme cases, hospitals revert to paper-based workflows, delaying patient care. Axonius addresses these challenges by consolidating cyber asset visibility, ensuring HIPAA compliance, and detecting rogue medical devices. CoverMyMeds, a McKesson subsidiary, used Axonius’ API to develop Looking Glass, an internal tool that automates asset tracking, assigns team responsibilities, and streamlines data collection.
Federal Agencies: Federal agencies manage complex IT environments and must comply with regulations such as the Federal Information Security Management Act and the DoD Risk Management Framework. Visibility gaps have left agencies vulnerable to breaches, as seen in the 2020 SolarWinds attack, where Russian hackers inserted malicious code into Orion, an IT management tool, creating backdoor access to government networks, including the Department of Homeland Security and the Treasury Department. Axonius Federal Systems mitigates such risks by detecting unauthorized devices, ensuring OS and software consistency, and providing visibility on security coverage tools in a unified platform.
Axonius is available to federal agencies through pre-negotiated procurement agreements, known as government contract vehicles, including:
GSA Multiple Award Schedules: Enables federal agencies to procure IT solutions from pre-approved vendors.
NASA Solutions for Enterprise-Wide Procurement: Used by NASA and other agencies to acquire IT products and services.
Continuous Diagnostics & Mitigation (CDM): A DHS initiative to enhance federal cybersecurity risk management.
DoD Enterprise Software Initiative BPA: A bulk purchasing agreement offering cybersecurity software at discounted rates.
State and local governments often operate with outdated infrastructure and tight budgets, making them prime ransomware targets. Initiatives like Cal-Secure emphasize asset management as a security priority. Additionally, agencies such as the Los Angeles Cyber Intrusion Command Center rely on Axonius to enhance cybersecurity and improve asset visibility.
Market Size
The global cybersecurity market is expanding rapidly due to rising cyber threats, regulatory demands, and increasing IT complexity. Valued at $245.6 billion in 2024, it is projected to grow at a 12.9% CAGR from 2025 to 2030. Axonius operates in Cybersecurity Asset Management (CSAM) by providing real-time visibility, automating security enforcement, and ensuring compliance across IT environments. As organizations scale, asset sprawl and security gaps become critical risks, driving demand for CSAM solutions.
Beyond CSAM, Axonius integrates with key adjacent cybersecurity markets to enhance its value. In SaaS Management, it identifies shadow IT and redundant software, addressing SaaS sprawl, security risks, and cost inefficiencies with subscription tools. With 22.8% of U.S. employees working remotely in August 2024, businesses face increased SaaS sprawl and shadow IT risks. The SaaS Management Platforms market, valued at $3 billion in 2023, is projected to hit $10 billion in 2032, with growth driven by cost optimization and security concerns.
While not a standalone ITAM provider, Axonius leverages ITAM platforms via adapters to maintain contextualized asset inventories. ITAM plays a crucial role in regulatory compliance and risk mitigation, with large enterprises increasing spending to meet security standards. The ITAM market is expected to grow from $1.6 billion in 2024 to $2.8 billion by 2034 at a 6.1% CAGR.
Competition
Competitive Landscape
The CSAM market remains fragmented compared to more established IT security segments. Axonius competes with Armis, JupiterOne, and Tanium in asset visibility, risk management, and compliance enforcement. Armis specializes in IoT and operational technology (OT) security, Tanium focuses on endpoint management, and JupiterOne is a cloud-native Cyber Asset Attack Surface Management platform. Axonius sets out to differentiate itself with an adapter-based model that integrates seamlessly with existing security tools.
In contrast to CSAM’s fragmented landscape, ITAM and Attack Surface Management (ASM) are dominated by major players. ServiceNow (30.4% market share as of February 2025), Jira, and IBM Maximo lead ITAM, offering centralized asset tracking and lifecycle management. Rather than competing directly, Axonius integrates with ITAM platforms for CMDB reconciliation and maintenance, ensuring accurate asset inventories. Similarly, Cisco, CrowdStrike, and Palo Alto Networks focus on external attack surface monitoring, but lack holistic internal asset visibility. Axonius complements ASM solutions by detecting and securing unmanaged assets that expand attack vectors.
Beyond ITAM and ASM, Axonius competes in SaaS management, risk visibility, and threat Detection. In SaaS Management, firms like Zylo, BetterCloud, and Torii manage SaaS sprawl, but Axonius identifies shadow IT and redundant software, reducing security risks and costs. In Risk Visibility and Threat Detection, Qualys, Splunk, and Sepio specialize in threat monitoring and incident response, while Axonius proactively identifies security gaps by correlating asset data to detect misconfigured or unmonitored assets.
Competitors
Comprehensive Cybersecurity Asset Management
This type of offering provides organizations full visibility and control over IT and security assets, including hardware, software, and cloud resources. It involves automating asset discovery, tracking, and compliance enforcement to ensure accurate, real-time insights into asset configurations, vulnerabilities, and risk exposure. By unifying IT and security data, it helps organizations streamline security operations and reduce potential attack surfaces.
JupiterOne
Founded in 2018, JupiterOne is Axonius’ primary competitor in cybersecurity asset management. JupiterOne employs an agentless approach to aggregate data from IT, security, DevOps, and HR systems—providing a holistic view of devices, users, networks, applications, and data. Its visual mapping tool highlights asset relationships, dependencies, and security risks, appealing to organizations that need clarity on complex interdependencies.
As of February 2025, JupiterOne had raised $119 million—most notably a $70 million Series C in June 2022 led by Tribe Capital and Bain Capital Ventures—achieving a valuation north of $1 billion. JupiterOne appeals to organizations seeking streamlined digital asset visibility. Notable customers of JupiterOne include Auth0, Robinhood, and Databricks. By contrast, Axonius has experienced meaningful market penetration, capturing an estimated 36% market share in the Cyber Asset Attack Surface Management (CAASM) category, compared to JupiterOne’s 6.6% as of February 2025.
Source: JupiterOne
Product innovation further differentiates the two. In July 2023, JupiterOne expanded its portfolio with an AI solution—the J1 On-premises Collector—that leverages natural language processing to enable intuitive queries and delivers step-by-step remediation guidance. Axonius launched its AI Query Assistant in February 2024; however, while it supports natural language input, its functionality is confined to pre-formatted query structures, offering less flexibility than JupiterOne’s more open-ended approach.
Overall, JupiterOne prioritizes visualizing asset interdependencies—especially within cloud infrastructures and security configurations—while Axonius emphasizes broader integrations and robust automation for enforcing security policies.
Tanium
Founded in 2007, Tanium specializes in real-time endpoint management, risk assessment, and compliance, offering features such as endpoint detection and response (EDR), vulnerability and patch management, asset discovery, and enforcement of security policies. Backed by investors such as Fidelity and Baillie Gifford, Tanium had raised roughly $1 billion in funding as of February 2025, including a $150 million Series G in June 2021 pushing its valuation to around $9 billion. Tanium’s strategy has been to build scalable, enterprise-focused solutions—even as it contemplates an eventual IPO to stay competitive against peers like CrowdStrike and Darktrace, which went public in 2019 and 2021 respectively. While both companies utilize a zero trust model, Tanium targets large enterprises by emphasizing high-scale endpoint control, whereas Axonius specializes in integration of endpoint and security solutions to provide full coverage of assets.
In terms of customers, Tanium’s solution is widely adopted in sectors like finance, retail, healthcare, and government where the ability to collect, analyze, and act on real-time endpoint data at scale is critical. Its clientele comprises large enterprises such as AstraZeneca and Barclays.
Tanium has also differentiated its product offerings through continuous innovation. In February 2025, Tanium launched an AI-powered autonomous endpoint management solution that can automatically resolve issues by patching and configuring software without manual intervention. Although different use-cases, this contrasts with Axonius’ automated enforcement framework, where customers must initially configure enforcement actions before automation takes over.
Risk Visibility & Threat Detection
This area focuses on enabling organizations to identify, assess, and respond to security risks across their IT environments in real time. Companies in this market segment provide continuous monitoring, advanced analytics, and threat intelligence to detect vulnerabilities, misconfigurations, and potential cyber threats before they can be exploited. These solutions leverage machine learning, behavioral analysis, and automated alerts to enhance security teams’ ability to prioritize and remediate risks efficiently
Armis
Founded in 2015, Armis provides agentless security for IoT, Operational Technology (OT), and unmanaged devices by continuously monitoring network traffic and using machine learning to detect threats. It maintains an up-to-date inventory of devices, including medical equipment, industrial control systems, and smart sensors, which often lack built-in security. Armis integrates with SIEMs and network management tools, offering visibility across complex IT environments.
As of February 2025, Armis had raised $792 million in total funding, including a $200 million Series D from investors like General Catalyst and Alkeon Capital in 2024 at a $4.2 billion valuation.
In the CAASM space, Axonius holds an estimated 36% market share versus Armis' 23.6% as of February 2025. While both platforms use agentless data collection, Axonius’ integration and automation capabilities help organizations identify security gaps and enforce policies at scale. However, Armis reportedly has a more expansive product suite and specializes in real-time threat detection for unmanaged and OT devices, making it a preferred solution for industries reliant on non-traditional connected assets. Axonius even integrates Armis into its ecosystem to fetch device data.
Qualys
Founded in 1999, Qualys is a cloud-based cybersecurity platform specializing in vulnerability management, continuous monitoring, and compliance solutions. The platform helps organizations streamline IT security operations by delivering critical security intelligence, automating auditing and compliance processes, and providing real-time visibility into security risks across on-premises, cloud, and mobile environments. Qualys integrates with SIEMs and IT management tools to enhance security posture management.
Prior to its 2012 IPO, Qualys had raised $34 million in funding from investors like Mercury Interactive and Trident Capital. In February 2024, the company had a $4.8 billion market cap.
Organizations looking for deep vulnerability scanning may prioritize Qualys, whereas those needing full IT asset visibility and security automation may prefer Axonius. Qualys provides strong scanning and risk assessment tools. Although both platforms compete in the vulnerability management space, they complement each other. Recognizing this, Axonius integrates Qualys as an adapter.
Business Model
Axonius operates on a subscription-based model, generating revenue through tiered pricing that adapts to customer needs. Organizations can explore the platform with a free demo or trial. Pricing varies based on deployment scale and feature set, with an average annual cost of $55K, and premium tiers reaching up to $126K. However, it is challenging to obtain clear pricing details from Axonius’ website.
The company’s major costs include cloud infrastructure, along with customer service, sales, and marketing, which are critical for customer acquisition and retention. Axonius also invests in innovation through AxoniusX, a separate research and development arm. While R&D contributes to product expansion, it was integrated early and is not expected to impose significant long-term profitability constraints.
Traction
In 2020, the company launched the Correlated Partner Program, which gained momentum, signing nearly 70 global partners within its first year. This initiative drove over 50% of new business, fueling Axonius’ long-term growth. During the same period, the company doubled its employee count.
The launch of Axonius Federal Systems marked the company’s expansion into the public sector, providing solutions to 70 Department of Homeland Security Group F agencies and making Axonius available through the General Services Administration (GSA), the most widely used acquisition medium in the federal system.
By 2024, Axonius had surpassed 500 customers, including Fortune 500 companies like Schneider Electric, News Corp, and Anheuser-Busch InBev, as well as U.S. Department of Defense agencies. As of 2023, the company had crossed $100 million in annual recurring revenue (ARR) after four and a half years of operations. One unverified estimate indicated the company had grown ~50% to $151 million in 2024. As of February 2025, Axonius has an estimated 36% market share in the Cyber Asset Attack Surface Management (CAASM) market, down from an estimated 43.0% share in 2024.
Valuation
As of February 2025, Axonius had raised $865 million across eight funding rounds, including a Series E extension of $200 million in March 2024 at a $2.6 billion valuation led by Lightspeed Venture Partners and Accel. This round followed a $200 million Series E in 2022 and a $100 million Series D in 2021. Other investors include Stripes Group, ICONIQ Growth, Alkeon, Owl Rock, and DTCP.
Publicly traded cybersecurity firms experienced fluctuating valuations from 2020 to 2023. After hitting a 17.7x median trailing-twelve-months revenue multiple in Q3 2021, the sector saw a sharp decline in Q1 2023. However, throughout the year, rising demand for AI-driven security solutions contributed to a recovery, bringing valuations back to 7.3x by Q4 2023. Based on the unverified estimate of Axonius 2024 ARR at $151 million, the company’s $2.6 billion valuation represents a 17x ARR multiple.
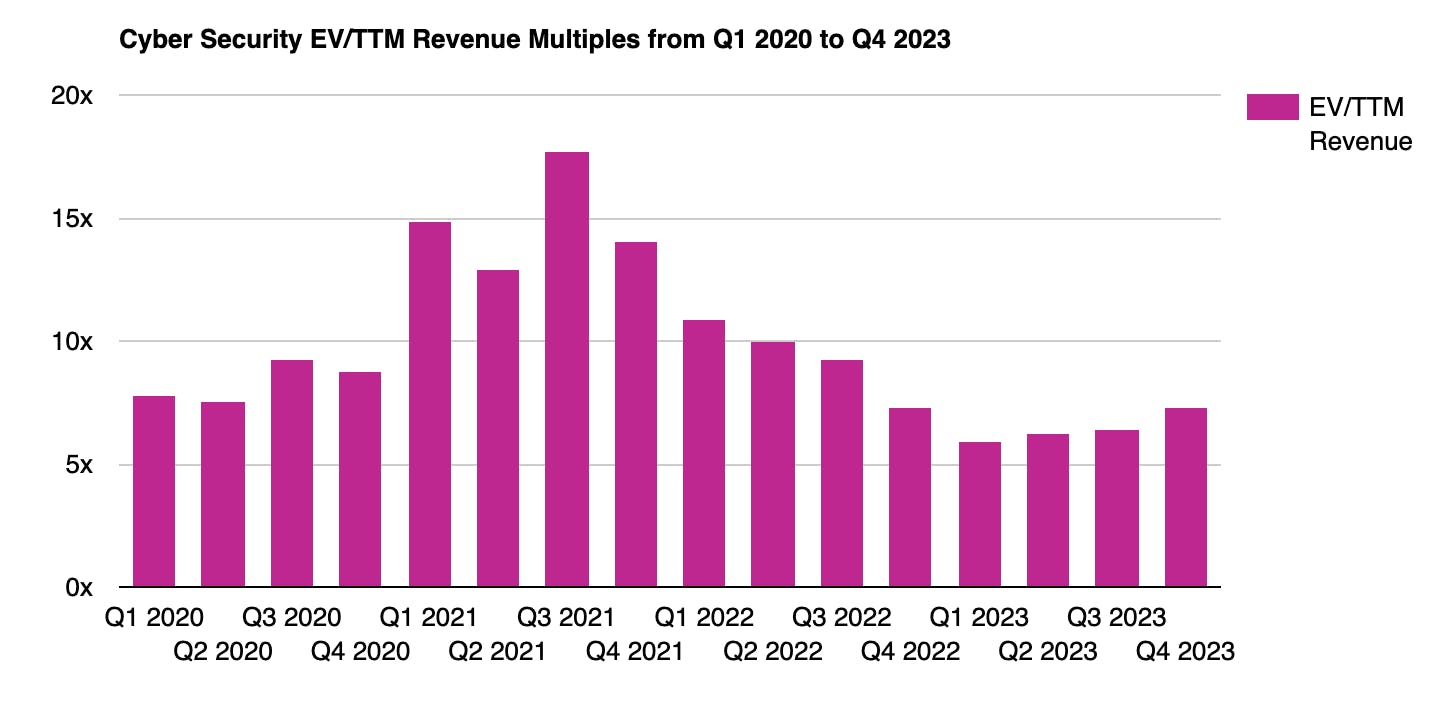
Source: Finerva
Key Opportunities
Enhancing Security with AI & ML
AI and ML are transforming cybersecurity by enabling predictive analytics, automation, and advanced threat detection. With a 65% increase in demand for AI-driven predictive analytics tools in 2024, Axonius has a significant opportunity to enhance its platform through deeper AI integration.
Axonius has already incorporated AI into its Query Wizard, allowing users to create queries using natural language. Additionally, it leverages AI-powered insights through integrations with partners like Palo Alto Networks Cortex XDR, showcasing its ability to integrate within existing security ecosystems. However, competitors like JupiterOne lead in user accessibility by offering a ChatGPT-like interface for their platform.
AI-driven automation can reduce incident response, such as with IBM’s AI technology which accelerates alert investigations by up to 55%, delivering substantial efficiency gains for organizations looking to streamline security operations. By expanding its AI capabilities and automation features, Axonius can further establish itself as a leader in intelligent asset management and cybersecurity automation.
Capitalizing on the Agent-less Approach
The explosion of connected devices in enterprise environments has made traditional agent-based security solutions increasingly inadequate. The global cloud market is projected to grow from approximately $262 billion in 2024 to over $837 billion by 2034, demonstrating a rapid increase in cloud adoption and the need for scalable security solutions. Axonius’ agent-less approach provides a unique advantage by allowing organizations to manage their growing attack surface without manually checking deployed agents on every device. Unlike siloed agent-based solutions that typically cover less than 50% of assets, Axonius allows for full asset visibility, reducing blind spots and enhancing security posture. As companies seek to unify security tools, the demand for agent-less asset management will continue to rise.
Integrated Security Platforms
The cybersecurity industry is shifting toward integrated security platforms as organizations recognize the inefficiencies of siloed security tools. The integrated security services market was valued at $21.1 billion in 2023 and is expected to reach nearly $54.7 billion by 2030. Many organizations struggle with siloed security data—as of October 2023, 72% of IT and security professionals report that fragmented data hinders their ability to manage security effectively. Axonius is positioning itself to capitalize on this trend by providing a unified platform that aggregates security data from multiple sources, improving decision-making and response times.
Key Risks
Intensifying Competition
Cybersecurity competition is intensifying as major players expand into asset management and automation. Companies like ServiceNow, while not direct competitors, dominate ITAM and could leverage their existing market presence to expand into adjacent areas that overlap with Axonius' offerings. Additionally, larger cybersecurity firms with deep financial resources may acquire direct competitors or integrate similar asset management functionalities into their existing platforms. This could pressure Axonius to continuously innovate to maintain differentiation.
Talent Acquisition & Retention
As Axonius continues to scale its core platform and the AxoniusX research wing, securing top cybersecurity and IT talent will be critical to sustaining its innovation and market position. However, the cybersecurity industry faces a severe talent shortage, with 3.5 million jobs expected to be unfilled in 2025. This skills gap is already impacting companies, with 57% of organizations reporting that it hinders their security operations in 2024. This shortage threatens Axonius' innovation and product development. If the company cannot attract and retain top-tier security professionals, it may struggle to execute on its long-term vision and compete against larger firms that have the resources to offer higher salaries, better benefits, and more extensive career development opportunities.
Summary
With large percentages of deployed SaaS licenses going unused and the number of cybersecurity and endpoint management solutions expanding, the need for asset visibility and discovery remains a critical priority for IT and cybersecurity teams. Axonius addresses this demand by providing an adapter-based platform, aiming to reduce security gaps caused by fragmented asset data, unmanaged devices, and compliance challenges. Its focus on automation, ease of deployment, and integration with existing security tools is critical in cybersecurity asset management. While Axonius has seen meaningful penetration into its core market, competition continues to intensify and AI-driven security solutions gain traction, it’s ability to differentiate itself will be tested.




